ABSTRACT:
We mainly explain about the importance of data security while transmitting data on network. SECURE DATA TRANSFER is a .exe file which enables the employee of a particular organisation to encrypt and decrypt data for security purpose using AES algorithm.
The encryption and decryption methods of cryptography used in developing this system make the surety of the proposed system more efficient in securing the data from unauthorized access.
This project is based on a new mechanism for data transfer over a secure network and through simplex transmission. We do so using simple embedded system technology.
Many government organizations which require high security and confidentiality of data use an intranet in order to prevent data leakage. This is often done by air gapping the system and physically isolating the hardware in order to prevent security attacks via the internet.
However, this can prove to be a hindrance when we are actually required to transmit some data to another device without the use of the internet.
Also, if our system needs upgradation of some software, there is inevitable use of the internet.
Because of this reason the databases and the systems become unfenced and vulnerable to malicious files. To prevent any hacking/misuse of the data and information, this particular technology is used.
MOTIVATION:
It is a guaranteed one way network connection, which protects secrets and safeguard availability and integrity of critical assets.
It can be conveniently used by the government and its defense organizations, as it provides zero compromise on security. Security and confidentiality of informations is very vital, because of which more than often isolated networks or intra-networks are developed and used. But with this technology no such measures are required as it provides immediate protection, confidentiality and availability.
EXISTING SYSTEM:
At present we normally send data by compressing large amount of data by adding security methods like password protection. There are many algorithms available in the market for finding passwords so we need effective algorithms.
Sending sensitive messages, documents and files over the internet, our information is directly open to interception by anyone using different hacking techniques.
PROPOSED SYSTEM:
Now a days when more and more sensitive information is stored on computers and transmitted over communication means, so we need to ensure information security and safety.
In Proposed system we are introducing the secure data transfer using Intranet(data is transfered with in organization) before it was existed for internet users.
We are implementing this through Air gap networking using AES algorithm (implemented to encrypt data) and MD5 algorithm( is a widely used hash function producing a 128-bit hash value) which is simple, easy to implement and provide high security.
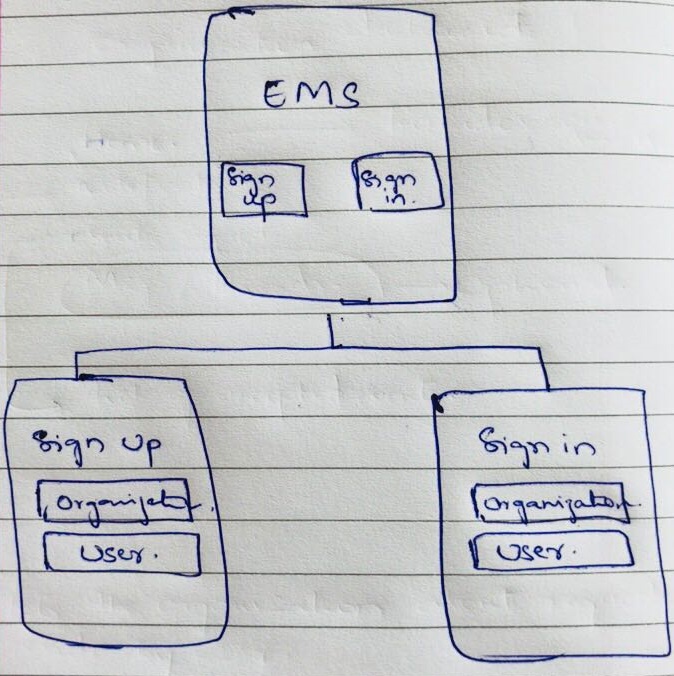
We develop a facility where users who wish to use the platform register their credentials with our database.
When the user wants to login so as to encrypt or decrypt data, he does so by entering his username and password which are validated against the database.
The username and password are concatenated and then, the resulting string is passed to a hash function which generates a unique 160 bit hash code.
This is then truncated to 128-bits and the result is used as the key to our symmetric key cipher. In this system, we are using AES.
The file to be encrypted is zipped and then converted to cipher text.
This file can be transmitted or sent to any other system via serial transfer.
At the receivers end, the exact mechanism occurs, except, to decrypt the data. Received file is unzipped and then passed back to AES for decryption.
Requirement Analysis:
In such an environment, it is absolutely necessary that we create a mechanism in order to transfer data to and from two communication points, albeit securely.
Only authentic user must be able to access his or her documents and should enforce some kind of validation mechanism.
In order to achieve the above, we create a platform through which we can safely access our personal files and encrypt or decrypt as per our discretion.
Also, we must be able to safely send any type of file.
Implementation
Essentially, we implement techniques such as hashing and message digest to provide security.
We make use of symmetric key cryptography in order to facilitate encryption.
We are also utilizing database validation in order to store records of authentic users.
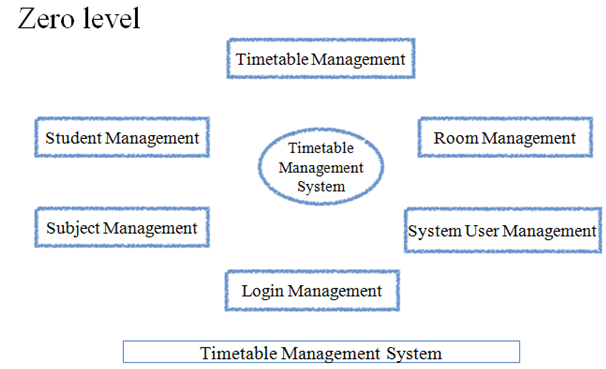
SYSTEM ARCHITECTURE:
Software Requirements :
- Operating System: Windows 7 or higher.
- Language: JAVA.
- Database: MySQL.
Hardware Requirements :
- Processor: Intel Dual core and newer.
- Hard Disk: 20GB.
- RAM: 1GB.
Conclusion:
In conclusion, this project is highly useful in order to transmit data through simplex or half duplex communication.
We avoid connection to any networks and hence maintain the integrity of the air gap network.
Any upgradation is done via serial-usb data transfer and thus we are completely isolating our network and protecting it from malicious data.
The confidentiality, integrity and authenticity of our data is maintained and data leakage or loss is avoided.