Intelligent Railway System Project is used to manage trains tickets and provide them to the users. It has many things that should be kept in the mind. This application is based on the online and they are connecting with the servers all the time and they have large databases at the server’s side which cannot be access directly.
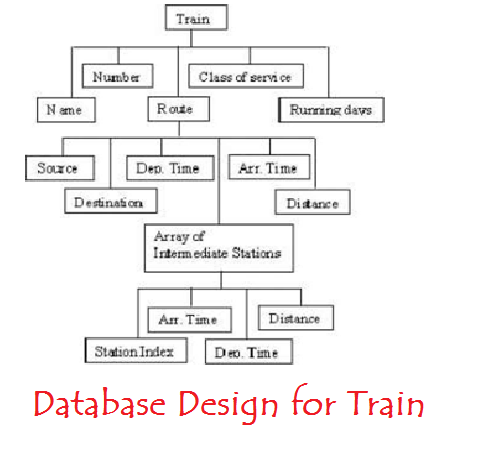
They are completely developed in the java as they provide features like object oriented. This system can be accessed by the admin only. Database is managed according to the city and stations. Every train has its own details like name, source station, destination station, time and days. It also provides feature to the administrator that he can add new trains, cities to the database. Everything is managed with the GUI interface. Students can also refer to Intelligent Train Project Documentation
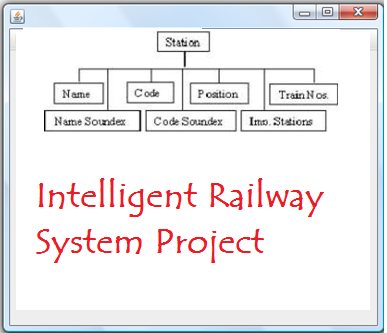
Intelligent Railway System Database Design:
Intelligent Railway System Project Modules Description:
Administrator can modify or delete existing stations. The database must be updated every time and automatically as the train timing are not fixed. For this special tool is designed that will update automatically with the help of internet portal. All the station that are added to the database must be connected to each other see that whether to that station can be reached directly or not.
This Intelligent Railway application also provides user query room. This panel will handle the client query about the trains. They need to enter the train name or train number, after that they have complete information about the train with arrival time and reaching time, fare price to particular station, stoppages.
Next panel is to decide the route which user want, check whether direct trains are available or not, or he need to change trains to reach the destinations. User can set his preference what station he wants to go and also decide the trains that have least stoppage time.
Also Refer: Intelligent Railway Information System Project