Abstract:
The Main objective of this Travel & Tourism project is to make the travel easy and comfortable for the users right from finding the routes and buses to till the booking of the tickets. In this project, we have two modules, Admin, and user.
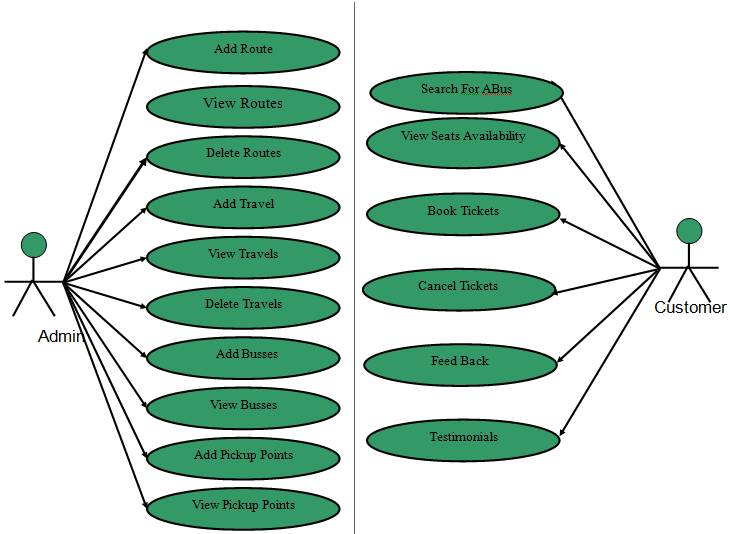
Admin in this Travel & Tourism Management System project will log in with the default username and password and admin has authority to add the bus routes and add the travel and assign the route id’s and bus id’s and finally, the admin will add the buses at particular times in different routes. Admin will also add the different travel agencies while adding buses admin will fix the ticket price and the capacity of seats.
Finally, the user will register and log in and the find the appropriate routes and use the route id he will search the bus by giving all details like date of journey and type of seat etc. After selecting the information user will be headed to select seats in a view the selected seats will be displayed as red and then after successful payment the booking confirmation will be shown.
If the user feels any feedback need to give, he can provide feedback to admin.
Existing System:
In the existing system, the user needs to find the bus routes by visiting the travel desks and enquire the information and the user needs to book the tickets manually and there may be a chance of no availability of tickets. So we Proposed this project this will overcome all difficulties.
Proposed System:
In the proposed system, the user need to just login into the application and can find the routes and booking immediately and complete the booking process for a successful transaction.
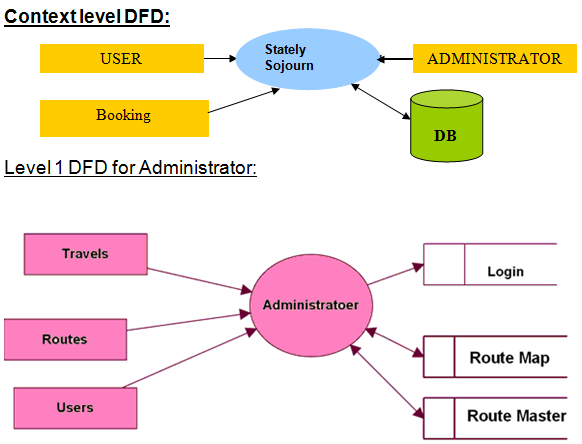
Data Flow Diagrams:
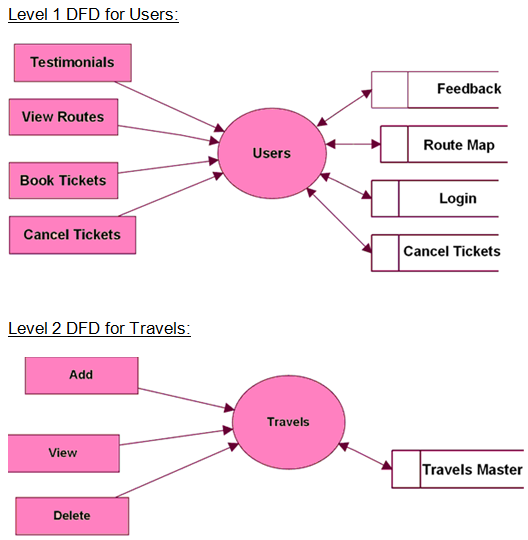
Context Level DFD and Level 1 Data Flow Diagram for Administrator, Users
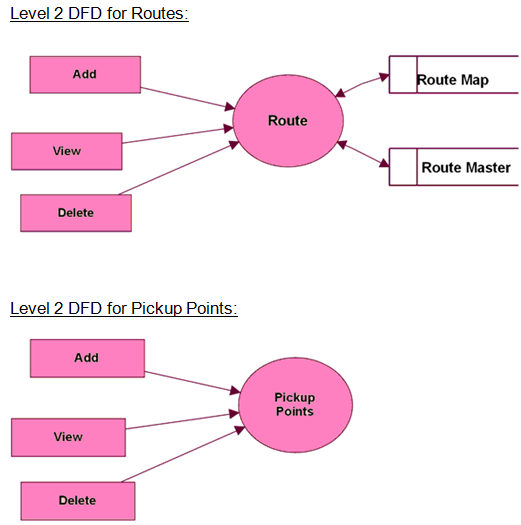
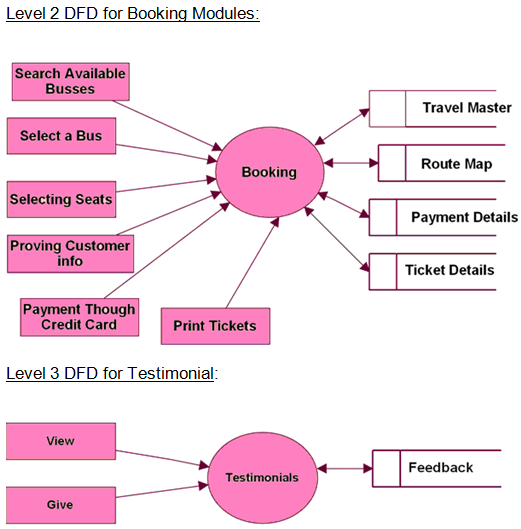
Level 2 Data Flow Diagram for Travels, Routes, Pickup Points, Booking Modules
Use Case Diagram:
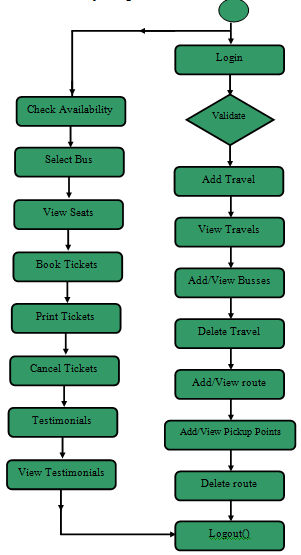
Activity Diagram:
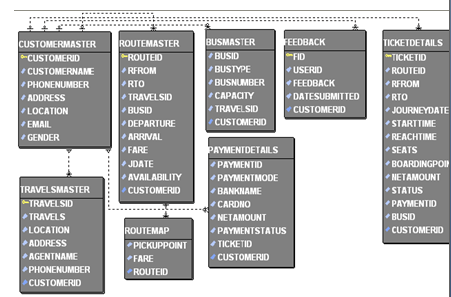
ER Diagram:
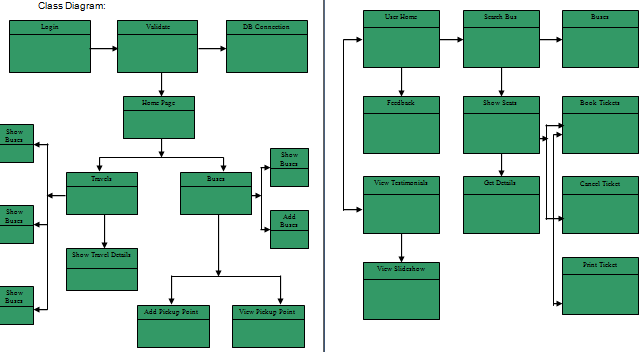
Class Diagram:
Download Travel & Tourism Management System Java Project Source Code, Project Report Documentation, PPT, UML Diagrams and Output Screens.