By making use of the different types of the storage resources in an efficient manner the storage consolidation is capable of offering the considerable savings of cost towards the traditional DAS. The major cost within the establishments of the DAS is that there is a necessity of managing the different systems in which the original storage is considered to be the primary cost within the NAS as well as SANs. The total number of the individuals who are needed to help the DAS entirely depends on the total numbers of the servers that are installed. Anyhow the servers are not being added by means of the SANs and the NAS they will just perform the storage process and for this reason there is only a necessity of the less number of users.
If the customers imagines the total numbers of the TB that belongs to the data could be easily controlled by means of the administrator run which is full time starts from 1.5 to 5.0 for the purpose of the DAS through the 6.0 to 13.3 for the purpose of NAS or SAN. On the other hand if the customer specifies that the usage of the disk is nearly 50% upon the DAS then that specific usage will increase nearly to the 90% which is intended for the purpose of the SAN as well as NAS. The SAN as well as NAs are capable of using the capacity that is available in an efficient manner and it is even simple to scale up the NAS and the SAN.
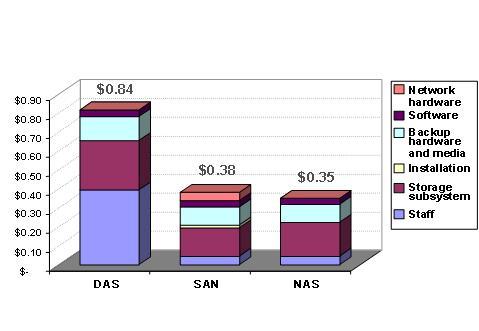
Fig: Breakdown of the storage costs per MB for the DAS, SAN as well as NAS.
This figure will specify the procedure of cost breakdown for the purpose of the DAS, SAN and NAS. By this figure it is clear that the administration is the majority of cost for the DAS and the storage media is the majority of cost for the SAN as well as NAS.
The high availability, the reliability as well as the performance are the major reasons for the establishing the storage consolidation. The high availability is being used for the purpose of accessing the data without any interruption. The reliability is intended for the purpose of the decreasing the downtime and to improve the continuity of the business. The performance is meant for the purpose of processing the quick transaction in order to develop the entire productivity.
Each and every specified attributes could be easily accessed by making use of the SANs as well as NAS. There is a necessity of the several types of the equal systems in which one system will have no work to do that will even wait for the failure of the other system in order to perform this action. Within the entire process if the server of the DAS gets failed then the entire data storage which is associated with the server will not be available and the data can be restored when the server is restored. The process of decreasing the performance as well as the availability for allowing the data to be more vulnerable to the disturbances is the time consuming process and cannot be processed in an easy way. The final solution for the user to access without any interruptions is using the SAN or else the NAS which is not having any failures as well as using several numbers of the paths that are related to the data access times. The final conclusion is that it is better to use the SAN or NAS than that of the DAS.