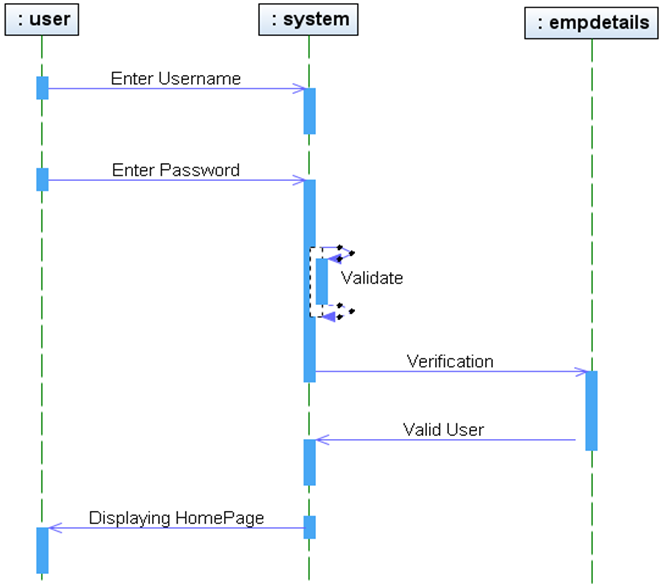
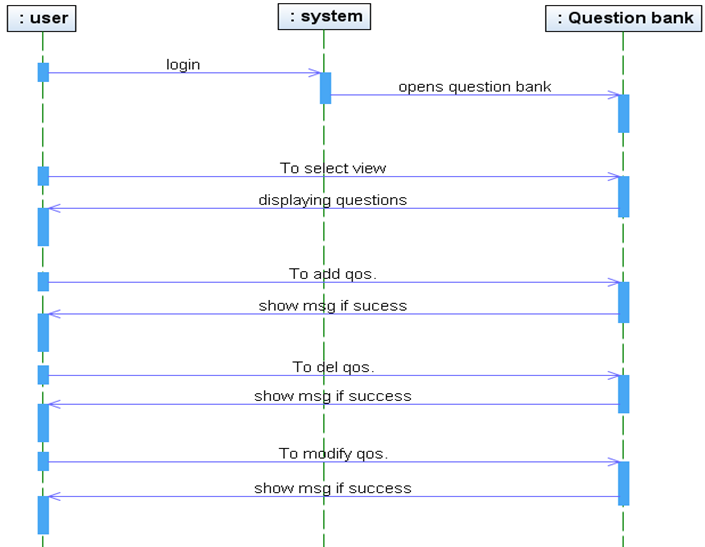
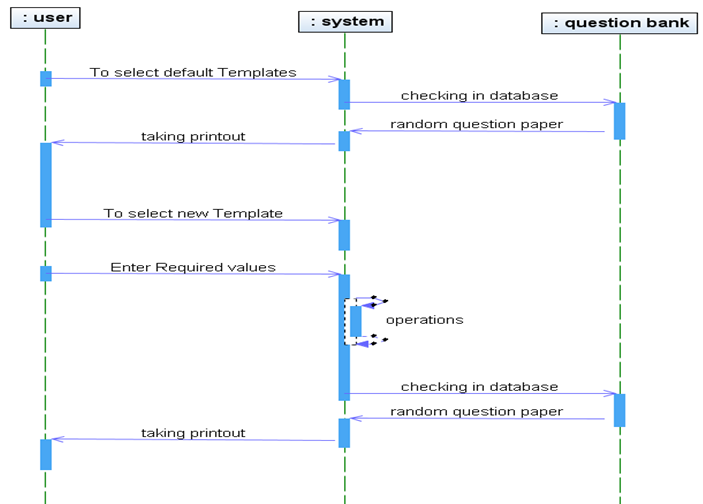
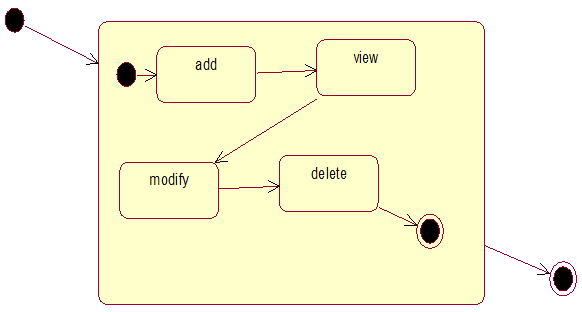
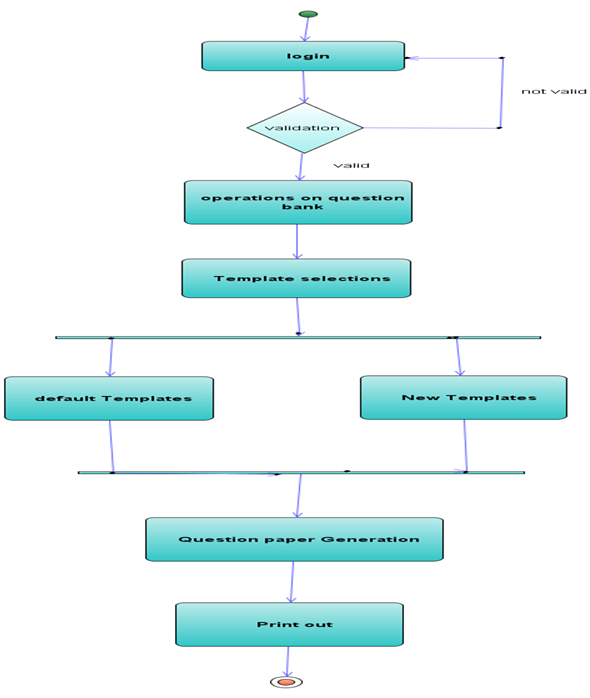
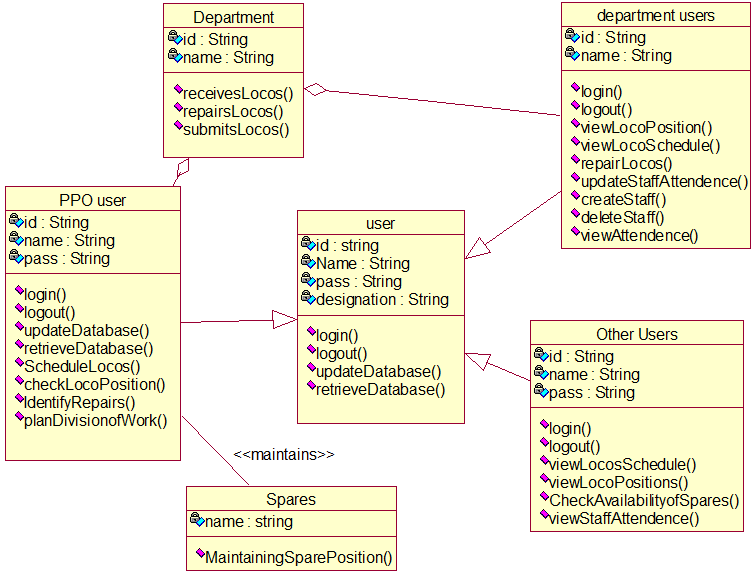
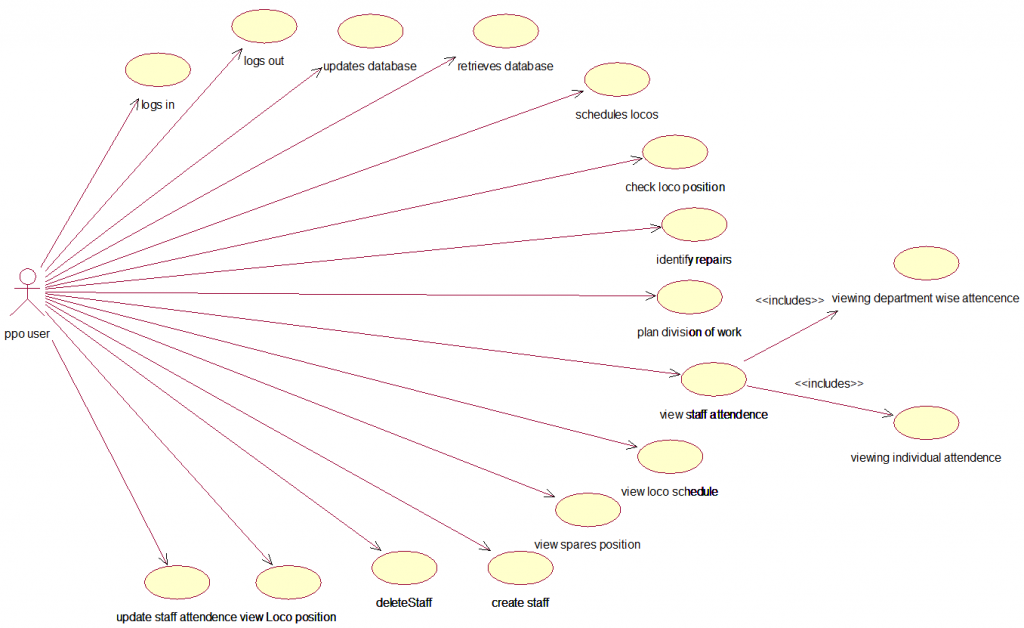
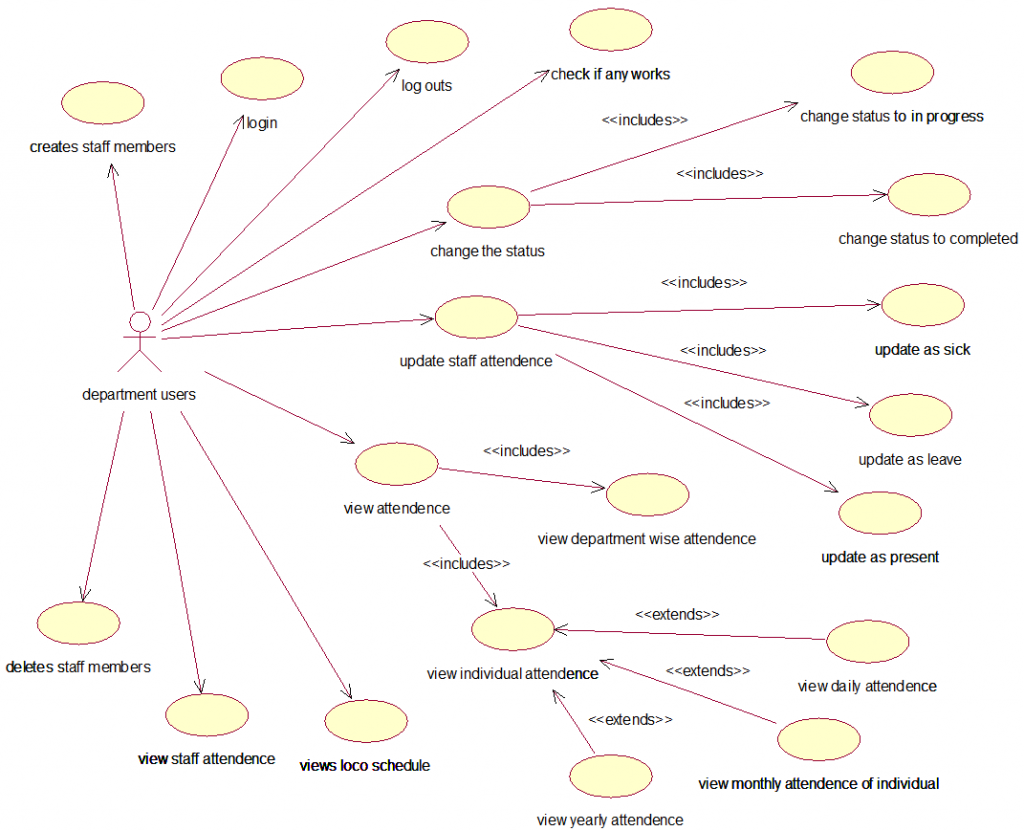
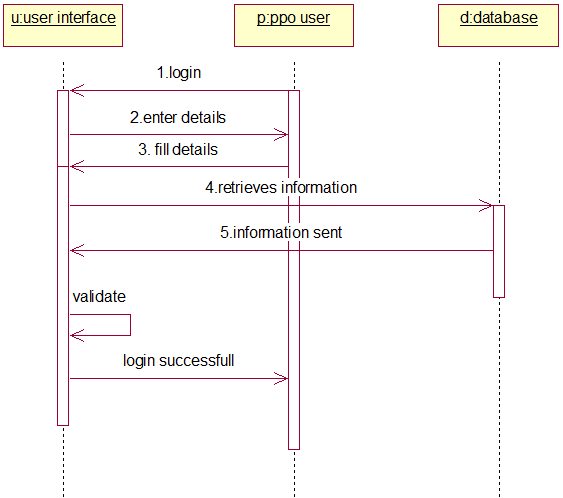
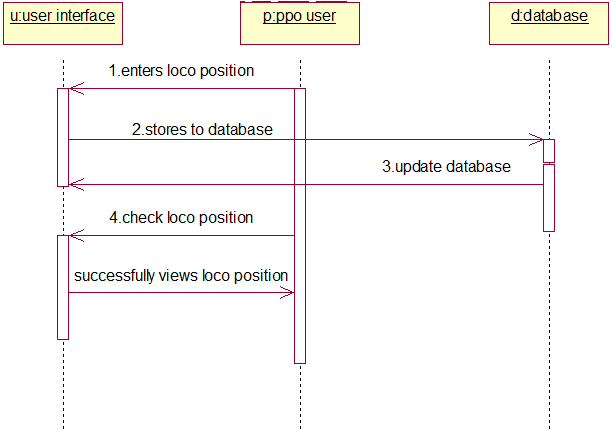
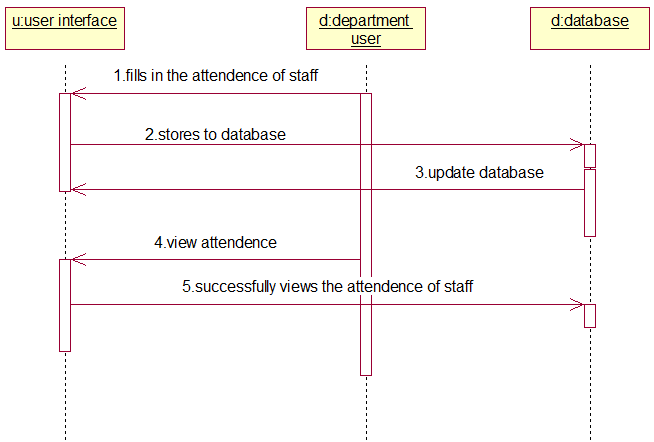
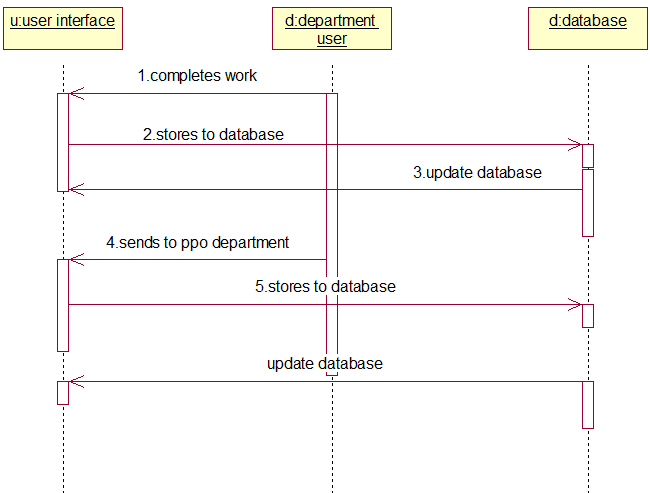
PROJECT DESCRIPTION: The College Sports Management System’s objective is to provide a which manages the activity of many sports at a time. It also manages the registration process and announcement of the results.
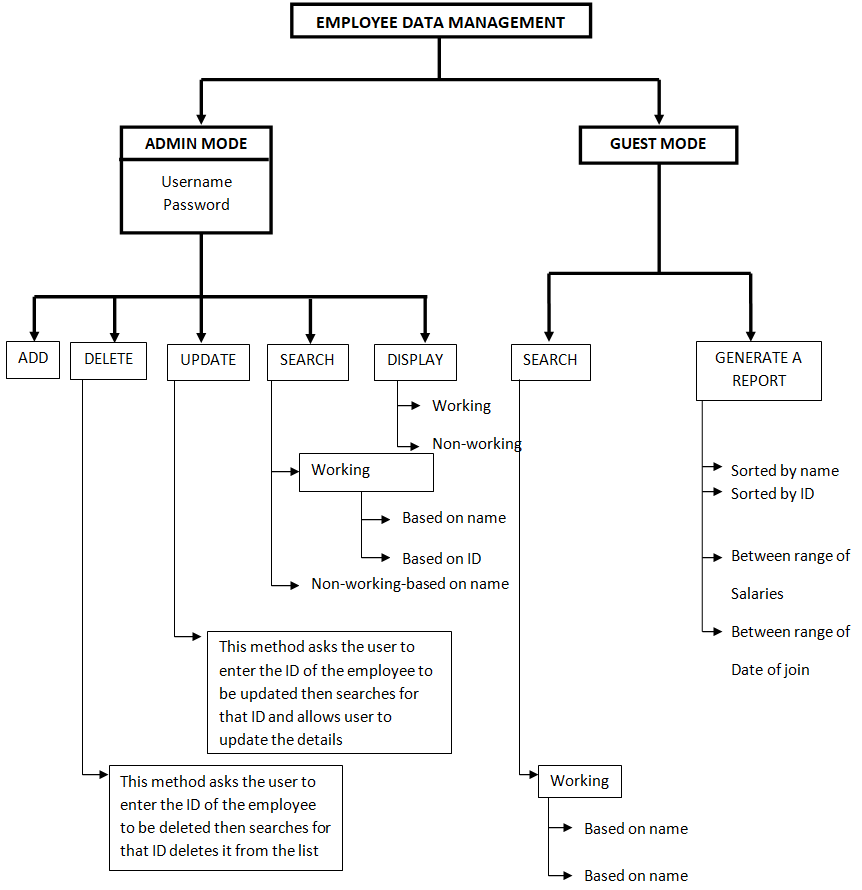
Modules
Add sports
We can add new sports into the system so that we are able to retrieve them later during the registration process. The sports added would be viewed during the creation of a new intra- college or university tournament.
Add Scoreboard
We add a scoreboard so that the students can view it and the results of each match are announced here so that there will be only one platform for the results. This would reduce the chaos during the score announcement.
Add Tournament
Each tournament from an intra-college or a university can be added here. It later would help in the registration of any sports in that tournament. While adding a new tournament the system would show the set of sports that are entered into the system by the director of the sports so only those sports can be included in the tournament while creation.
Remove Sports
This module will help in the removal of any sports that the sports director thinks are not needed in the system. The removed sports would not be shown anywhere in the system that includes during the addition of a new tournament.
Edit Scoreboard
The added scoreboards would be updated here. This module helps in updating the scores on the scoreboard. Only the scoreboard which is added using the add scoreboard module would be present here and only these scoreboards can be updated. We won’t be able to add a new scoreboard here.
Remove players
This module would remove each player after each round of the tournament. So that only the existing player will be present and the one that is not qualified for the next round would be removed using this module. This would give a clear picture of the qualified players. As well as the player from the college team I can also be removed.
Remove Tournament
After each tournament in the college or a university, we should remove it, so that there won’t be any confusion between different tournaments which are going to be held later on. This module would help in removing all the details of the deleted tournament.
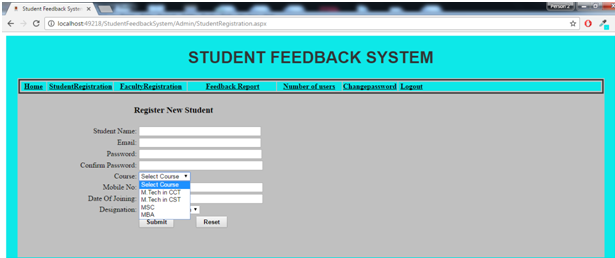
Registration Individual
This module would help in the registration of individual sports events held in the tournament. We selected the tournament in which we want to be part and the sports in which we want to participate in and the player would add his name and the required details asked in the registration form. After all these processes then we can click on the submit button and the student has registered for the tournament that they wish to participate in.
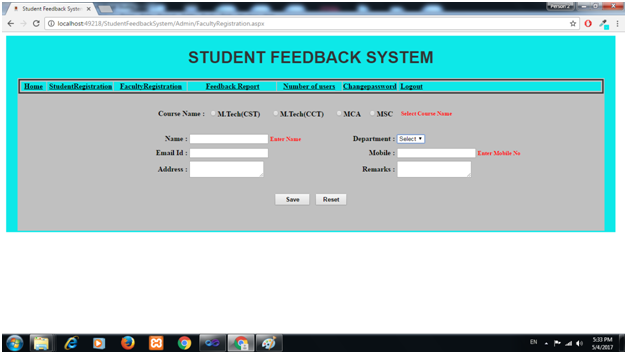
Registration Group
This module would help in the registration of group sports events held in the tournament. We selected the tournament in which we want to be part and the sports in which we want to participate in and the set of player’s names would be added and the other required details asked for in the registration form. After all these processes then we can click on the submit button and the student has registered for the tournament that they wish to participate in.
Payment
This module would help with online payment. So that the students wouldn’t have to stand in a queue or have hard cash in hand in order to do any payment to the sports department. By using this module we are reducing a lot of paperwork and we are giving the students the liberty of doing the payment from wherever they are.
- This College Sports Resource Booking Project is related to the College Sports Management System Project. You can also visit & download the Android Application project on College Sports Resource Booking
SYSTEM STUDY
EXISTING SYSTEM
The existing system is more of a manual work, where the students have to walk up to the sports department and have to register for the events that they desire to participate, it’s not just the registration process but even other activities such as the announcement of the result, the payment, etc. This results in a lot of paperwork and the chance of the data getting mixed up is high. In the existing System, students are not able to get proper information about the games conducted in various venues. The student needs to spend a lot of time to get the information about the game. The student should attend the venue to get information on the game which takes a lot of time. The information such as the qualified player’s list, the timing of the event, the score of the sports happening, etc.
DISADVANTAGE OF THE EXISTING SYSTEM
- Involves a lot of paperwork
- Students have to walk a lot for the registration and other sports-related activities
- Data getting corrupted is high
- Human error is common during intra-college and university tournaments.
- The students need to visit the venue to get all the information about the tournament and would have to wait for a long time.
- Manually recording all information with regard to all data and manually creating the contest schedules, coordinating facility usage, and hand-registering athletes and teams. The dissemination of information would require that documents be typed, photocopied, and put up on the notice board or common place where students can view them.
You can also visit & download the website project on University Leave and Outing Pass Automated System
PROPOSED SYSTEM
In the proposed College Sports Management System student can get all the information about various games and the venue.
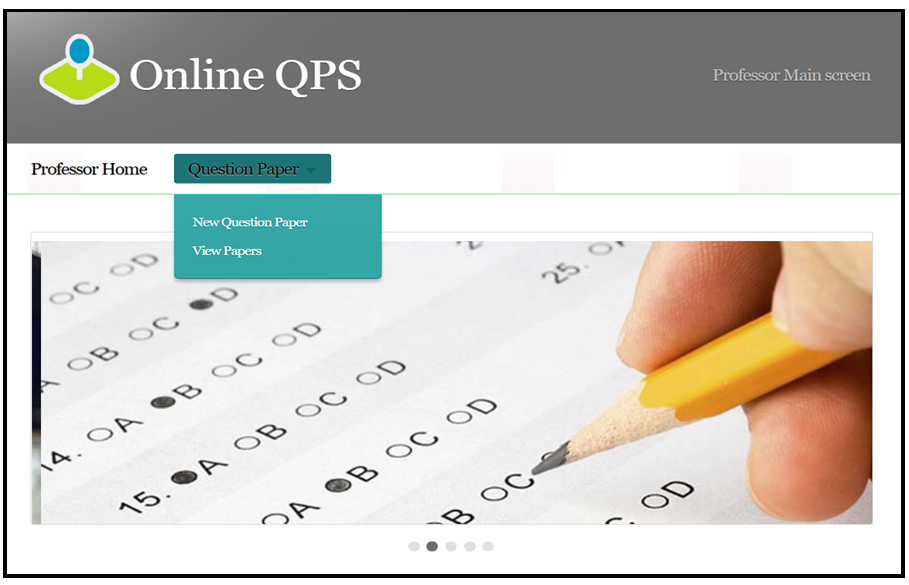
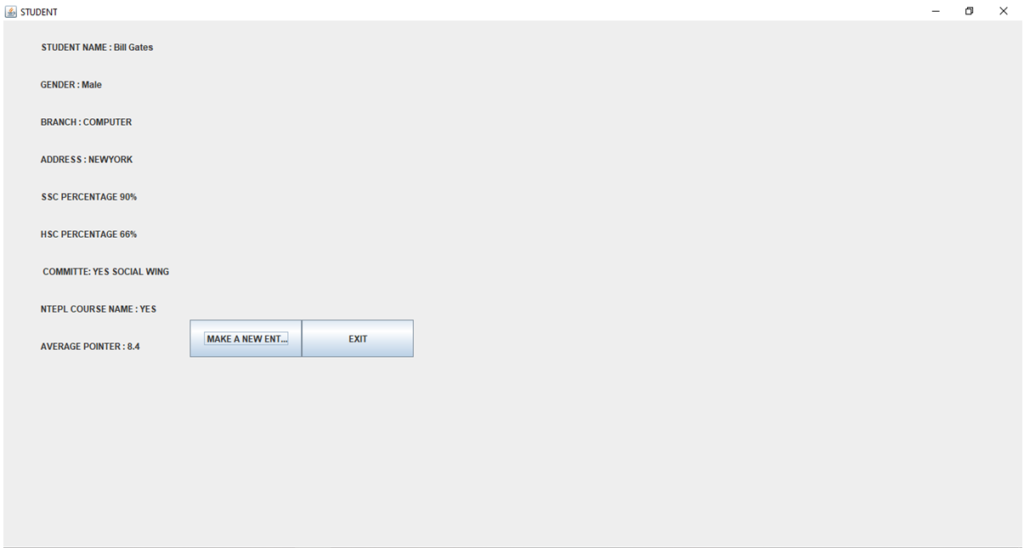
OUTPUT SCREENSHOTS
- Sports team
- Adding new tournament
- Adding new sports
- Removing sports
- Removing Players
- Index page for Registration
- Registration form for intra-sports
- Registration form for group events
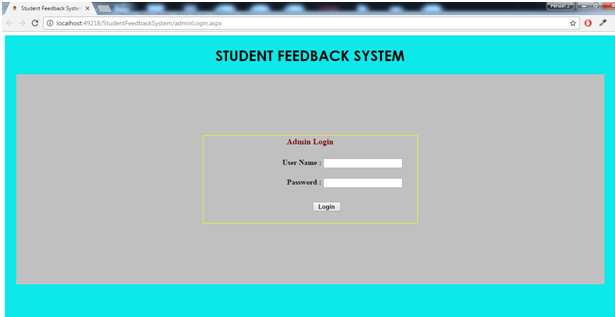
- Admin Login
- Index page
- Admin Home page
- Adding scoreboard
You can also visit & download the web application project on Student Activity on Sports System
CONCLUSION
Sport is a part of the curriculum in college. Hence it’s time for the sports department and its activities to be automated and go online as it will be beneficiary for everyone who is associated with sports in college. The “College Sports Management System” project will assist the sports department of the college and would help the students in saving a lot of time in searching for games being conducted in the college. Our project provides students to get register from anywhere and anytime. It helps the administration by streamlining the current intra-college sports event administrative practices. Specifically. It will allow the administrators to configure a set of Tournaments into the system and simply record the results of those contests so that administrators and the public can track the teams during the course of the tournament.
.NET Framework makes the application robust, secure, and reliable. This system provides better scalability and is open to more enhancements. More levels of abstraction can be implemented at the front end and back end, thereby making the system easily adaptable to any changes in the environment.
The software developed was implemented and tested with real data and was found to be error-free. Also, it is found that the system works successfully. The user has to provide their personal detail to buy a package. All the necessary validations are carried out in this project so that the company can make use of this software and the necessary messages make them conscious of the error they have made. Henceforth, valuable reports have been generated for this organization.
You can also visit & download the Java and MySQL-based web Application project on Sports Event Management System
Download the Complete College Sports Management System .Net Project with ASP.Net, C#.Net, and SQL Server.