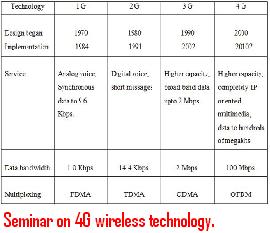
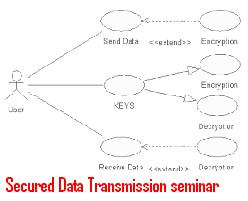
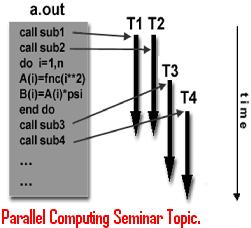
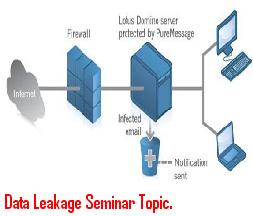
Tripwire technical seminar topic explains about software application which monitors important changes that takes place in system. This paper presentation explains features of Tripwire software, working, how to install Tripwire and software advantages.
Tripwire technical seminar topic explains about software application which monitors important changes that takes place in system. This paper presentation explains features of Tripwire software, working, how to install Tripwire and software advantages.
Tripwire software find out any changes that had taken place in the system and display information of the important files which should not be modified , files that are modified in size, binary signature are also displayed. Tripwire is a open source software which can be used by administrator in a organization to check modified files in the system and perform operations to modify, delete or update those files. Checksum is generated for each modified file which can be viewed by administrator. Admin can compare original checksum with modified checksum and perform addition or deletion of files.
Tripwire software can be installed in servers like firewalls, web servers, transaction servers and development servers. This software will automatically scan servers to find out the changes accoured in the server, database files and policy files are important files that are continuously scanned by Tripwire.
download Technical Seminar On Tripwire , paper presentation.