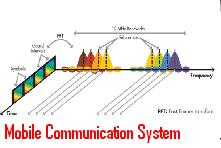
Nanotechnology is abbreviated as Nanotech. It is the study of matter based on the scale of atoms and molecules. It deals generally with the size structures of smaller or 100 nanometers to develop device or material.
It increases various issues of modern technology and nanomaterials impact on environmental and toxicity. There are potential effects on speculation and global economics and many doomsday scenarios.
There are two important approaches employed in nanotechnology. In the approach of bottom-up, the materials and devices are constructed from components of molecular on the molecular recognition principle. In the top-down approach, nano-objects are made from entities which are large without control of atomic-level.
There are many modern developments. They are atomic force microscope (AFM) and Scanning Tunneling Microscope (STM) launched nanotechnology. Marvin Minsky developed scanning probe microscope, scanning confocal microscope, and scanning acoustic microscope. Other developed nanolithography techniques are dip pen nanolithography, electron beam lithography, and nanoimprint lithography.
Many products are made accessible online with this technology. Various applications include cosmetics, titanium dioxide in sunscreen, and other food products. The allotropes of carbon are employed to produce gecko tape, silver in clothing, food packaging, disinfectants, and household appliances, zinc oxide in cosmetics and sunscreens, paints surface coatings, and furniture varnishes, and cerium oxide for fuel catalyst.
Conclusion:
The NANO TECHNOLOGY BASED DATA STORAGE Final Year Seminar Topic concludes that nanotechnology is diverse extremely widely ranging from physics of device to modern approaches depending on molecules with nanoscale dimensions. The technology creates various materials and devices with applications like electronics, medicine, and energy production etc.
Download Nano Technology Based Data Storage Final Year Seminar Topic