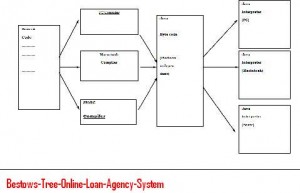
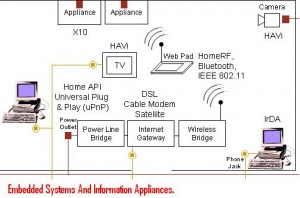
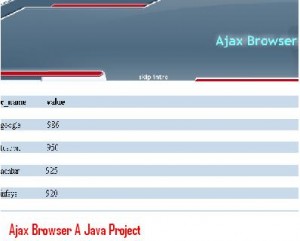
Ajax browser is developed using java script and java swings which can be used by computer science students as a final year project.This projects main idea is to develop new application which will load web page faster than existing HTML Pages.
The existing browsers use synchronous communication with the server in order to get the requested pages. When the page is refreshed the whole page is loaded again from the server which is time consuming moreover increases the network traffic and server load. Also this refresh operation creates white page outs in the web pages due to which the user cannot interact until the whole page is loaded again.
Problem Definition:
The web browsers should communicate with the server asynchronously i.e., when the user requests for a page, the user should be able to interact with the web page while the browser loads the page from the server.
When the page is refreshed, there should be no white page outs and only some part of the web page is updating dynamically instead of loading the whole page again. Partial updation of a web page reduces network traffic and improves the operationally of the applications as that of desktop applications.
Proposed Solution:
We propose a new web browser for Ajax approach with asynchronous communication model. Our web browser can improve the operationally that is equivalent to the operationally of desktop applications without revising program codes of the web applications. When the page is refreshed, the browser initially collects the requested page information from the server and constructs trees for current and requested pages. It then compares the trees and the differences are identified. Only those parts of the page where changes occurred are loaded.
CONCLUSION
The application “A web browser for AJAX approach with asynchronous communication” developed by us has made the best possible efforts to satisfy the requirements for a browser. The browser can update partially a web page that is not adopted Ajaxtechnique. Because the browser communicates asynchronously with web servers, the partial update of a web page is possible while user continue to operate the web page.
Due to some limitations, we have developed our browser with Ajax approach only for the static pages that is for the HTML pages present in the local system. When a local HTML page is selected by either giving the path in address bar of browser or by selecting through file menu, the file is displayed in the browser. When the Ajax Refresh button is clicked, the page is updated partially by going through all the modules given in the abstract.