Trends in Telecom seminar topic explain about how communication technology has increased its growth in daily life in terms of voice, data transfer, interne in different networks.
Trends in Telecom seminar topic explain about how communication technology has increased its growth in daily life in terms of voice, data transfer, interne in different networks.
With the increase of usage of technology many fields like media, advertising and shopping are taking advantage of these technology and inventing new activities. All these sectors are developing cross plat form products and improving their business. Banking is one of the field where technology is mostly used few years back banking usage was not computerized but now every transactions or any type of operation can be performed through online process and now mobile banking is increasing fastly.
These are the list of fields in which technology is playing important role.
Online-Banking, Online- Shopping.
VOIP services for voice communication.
Internet connections across the world.
Online voice chatting, online video chatting, Satellite communication.
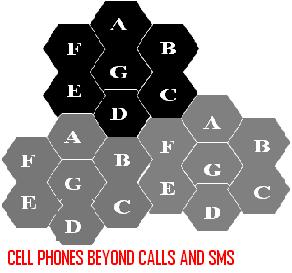
Telecommunication technology has created a new trend in every one’s life. As the usage is increasing new technologies are developing to provide needs to customers one among them are cell technology. In this method same bandwidth is used in different locations without overlapping, which will increase customers. A area is divided into multiple hexagonal cells. In recent times internet on mobiles are creating lot of business like developing apps, online application and usage of internet with new technologies like 2g and 3g are creating lot of scope for future development.
download Seminar Report and paper presentation on Trends in Telecom Technical seminar Topic.