The mapping or binding of IP addresses to host names became a major problem in the rapidly growing Internet and the higher level binding effort went through different stages of development up to the currently used Domain Name System (DNS) Java project.
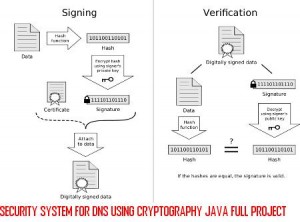
The DNS Security is designed by CSE Final year students using java programming to provide security by combining the concept of both the Digital Signature and Asymmetric key (Public key) Cryptography. Here the Public key is send instead of Private key.
The DNS security uses Message Digest Algorithm to compress the Message(text file) and PRNG(Pseudo Random Number Generator) Algorithm for generating Public and Private key. The message combines with the Private key to form a Signature using DSA Algorithm, which is send along with the Public key.
The receiver uses the Public key and DSA Algorithm to form a Signature. If this Signature matches with the Signature of the message received, the message is Decrypted and read else discarded.
The DNS as an Internet standard to solve the issues of scalability surrounding the hosts.txt file. Since then, the widespread use of the DNS and its ability to resolve host names into IP addresses for both users and applications alike in a timely and fairly reliable manner, makes it a critical component of the Internet.
The distributed management of the DNS and support for redundancy of DNS zones across multiple servers promotes its robust characteristics. However, the original DNS protocol specifications did not include security. Without security, the DNS is vulnerable to attacks stemming from cache poisoning techniques, client flooding, dynamic update vulnerabilities, information leakage, and compromise of a DNS server’s authoritative files.
In order to add security to the DNS to address these threats, the IETF added security extensions to the DNS, collectively known as DNSSEC. DNSSEC provides authentication and integrity to the DNS. With the exception of information leakage, these extensions address the majority of problems that make such attacks possible. Cache poisoning and client flooding attacks are mitigated with the addition of data origin authentication for RRSets as signatures are computed on the RRSets to provide proof of authenticity.
Dynamic update vulnerabilities are mitigated with the addition of transaction and request authentication, providing the necessary assurance to DNS servers that the update is authentic. Even the threat from compromise of the DNS server’s authoritative files is almost eliminated as the SIG RR are created using a zone’s private key that is kept off-line as to assure key’s integrity which in turn protects the zone file from tampering. Keeping a copy of the zone’s master file off-line when the SIGs are generated takes that assurance one step further.
DNSSEC can not provide protection against threats from information leakage. This is more of an issue of controlling access, which is beyond the scope of coverage for DNSSEC. Adequate protection against information leakage is already provided through such things as split DNS configuration.
Conclusion.
DNSSEC demonstrates some promising capability to protect the Internet infrastructure from DNS based attacks. DNSSEC has some fairly complicated issues surrounding its development, configuration, and management. Although the discussion of these issues is beyond the scope of this survey, they are documented in RFC 2535 and RFC 2541 and give some interesting insight into the inner design and functions of DNSSEC.
In addition to keep the scope of this paper down, many topics such as secure zone transfer have been omitted but are part of the specifications in RFC 2535. The first official release of a DNSSEC implementation is available in BIND version 8.1.2.

I hope other users think your post right here as helpful as I have. I run a blog personally and would be more than happy for you or the visitors on your site to check out. Please go ahead and browse through my website like I have with yours and leave a remark or two if you discover anything interesting. Thanks again.
can you please tell me how to execute this project on netbeans .
you immediate reply will be highly appreciated
this project is fully not running there are some files missing. even source.BAT exe file is not included & we dont getting flow of this project
im so worried abt this 🙁 🙁
i want uml diagrams for this project and also resend the how to execute the project and all screen shots for this project…. thnk you
Mr trettin i need to understand flow of this project can u plz contact me on my mail id balmossigohan@yahoo.co.in & divya u too …
this project is not fully running. Plz upload the .exe files of this project
pls tell me how to run this project . i need to understand this project
Hey..!!! Its such a nice project….
I want to know how do you create the Password, Req and Server batch files.
Could you please tell me on my email id which i had mention here.
Hey..!!! Its such a nice project….
I want to know how do you create the Password, Req and Server batch files.
Could you please tell me on my email id rudraksh3011@gmail.com
can you please tell what is n value and exponent value??
Plz developer help me with the values of exponent value and n value??
i want uml diagrams for this project nad can u tell me the flow of the project.
best report
i am having some problem in executing program is anyone can help me plz…. mail me priay0verma@ymail.com
Are you able to run the project?
pjeet.0733@gmail.com
iam having some problem in executing the program…..and i want the use case diagram,class diagram,interaction diagram…..know about the program flow….also send complete snapshots of this project…….mail me at ishaq.siddique@gmail.com
I recently downloaded this project as it is quite appealing. I tried executing it quite a lot of time now but the destination node never gets any encrypted message, seems like there is a file or piece of code missing.
I really need your help now sir. please contact me through my mail id: dynamikvoid@gmail.com
That project is nice but
I have some problem for executing the program and also some files are missing that project .please send to me the flow of that project and give the snapshot of the executing that’s project on that mail
sainathw123@gmail.com
Are you able to run the project?
pjeet.0733@gmail.com
I am not able to run the project as some files are missing .Please send me all files at pjeet.0733@gmail.com
This project is giving java.lang.NullPointer.Ecxception error while running and it is not the full project.
I want complete source code
ppt and documentation of the
project.and also I need how to run the project.please send it.
some files are missing in this project kindly please send whole project.
sir pls send source code on DNS security systm using crypto on java , pls sir help me….
I recently downloaded this project as i liked the idea. I tried executing it quite a lot of time bt it always shows “The destination may be switched OFF”,”restart the server”, seems like there is a file or piece of code missing.
Please help me out as soon as possible.
Please tell me how to download this project
how download this project
Please send me the project.
Can I have the source code with the complete documentation of the project
Can i have the source code a d documentation for this project
Hello sir Will really appreciate if I get the source code for the program
can you send me the source code for this project
Can i have a source code and full documentation for this project
Can i get the source code ?
pls send source code
Can l get the source code please
sir can i get the source of this project