Project Title: NETWORK TRAFFIC ROUTING OVER NURAL NETWORK
Abstract: For routing the information over the network, a number of routing techniques are available. To transfer the data efficiently acroos the network, a rotuing algorithm which is the best should be selected. No discussion was done on the selection of best routing algorithm and for the given subnet configuration, making a choice of best routing algorithm is only defined by the entire problem.
Calculating the efficiency of routing algorithm which the user selects and deciding the best one among them is the main aim of the project.
Efficiency of Subnet:
The folowing formula can be used for calculating the efficiency of any routing algorithm
Efficiency= i / n
where i is the efficiency of router and n is the number of routers in the subnet
Main aim: The NETWORK TRAFFIC ROUTING OVER NURAL NETWORK has the following objectives:
- There should be a proper display of topology of the desired subnet with the designated routers to it and the appropriate links along with proper computer images.
- Congestion table should be should be displayed with appropriate congestion links.
- Statistics of any router like efficiency, average size of the packet should be displayed as per the requirement.
- When ever the congestion table is clicked, statistics like propagation delay of the link, buffers filled are displayed.
- When ever the router is crashed, a provision should be provided where the router crash is handled.
- When ever a link is down, there should be proper handle of that and thus enhancing the routing even if a link is down.
- The statistics for the router and the link are to be calculated for every 500 m sec.
- Congestion table should be re constructed.
- A speed controller should be provided for routing.
Both the quantitative and qualitative methods can be used to measure the performace of the network routing over different topologies. Statistical analysis of the data transfer can be estimated with these methods
Software Requirements:
Two desktop systems with printer with windows xp operating system
– Internet connection
– Java JDK software
LIST OF CONTENTS
- Introduction
- Literature Review
2.1 Research problem
2.2 Research methods
2.3 Project purpose
2.4 Project scope
2.5 Project outline
2.6 Project definition
2.7 Existing system and problems
2.8 Proposed system
- Analysis
3.1 Network topologies
3.1.1 Bus topology
3.1.2 Ring topology
3.1.3 Star topology
3.1.4 Tree topology
3.1.5 Mesh topology
3.2 Routing
3.2.1 Unicast routing
3.2.2 Broadcast routing
3.2.3 Multicast routing
3.2.4 Anycast routing
3.3 Routing table
3.3.1 Network route
3.3.2 Host route
3.3.3 Default route
3.3.4 Static routing
3.3.5 Dynamic routing
3.4 Router
3.4.1 Control plane
3.4.2 Forwarding plane
3.5 Packet
3.5.1 Packet framing
3.5.2 User data
3.6 Routing protocols
3.7 Factors to decide best path
3.7.1 Path length
3.7.2 Reliability
3.7.3 Delay
3.7.4 Band width
3.7.5 Load
3.7.6 Communication cost
3.8 Choices in routing
3.8.1 Static and dynamic routing
3.8.2 Single path verses multiple path
3.8.3 Flat verses hierarchical
3.8.4 Router intelligent and host intelligent
3.8.5 Inter domain and intra domain
3.8.6 Centralised verses de-centralised
3.9 Routing algorithms
3.9.1 Flooding
3.9.2 Hot potato routing
3.9.3 Source routing
3.9.4 Distance vector
3.10 Routing information protocol
3.11 Link state algorithm
3.12 Subnet efficiency
- Design
4.1 Design goals
4.2 Router
4.3 Link
4.4 Routing algorithm
4.5 Names and objectives
4.5.1 Brief
4.6 Client application overview
4.7 Network communication design
4.8 Server application overview
- Implementation
5.1 Structure of the server application
5.2 Structure of the client application
5.3 Software requirements
5.4 Java tools
5.5 User guide
5.6 Operating
- Testing and evaluation
6.1 Online response
6.2 Stress testing
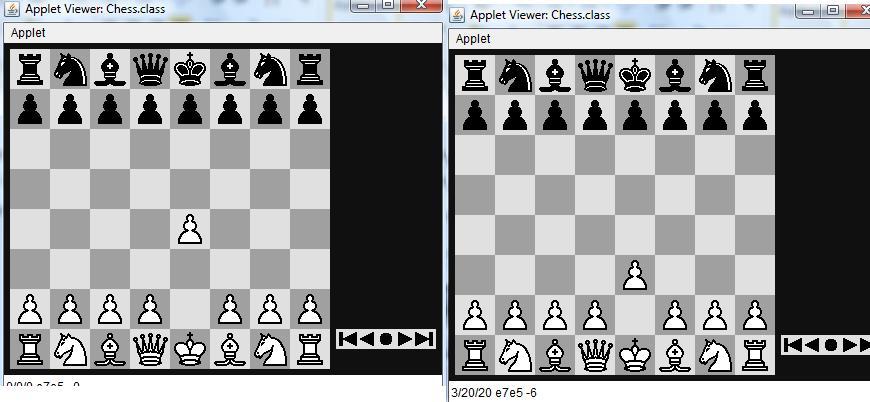
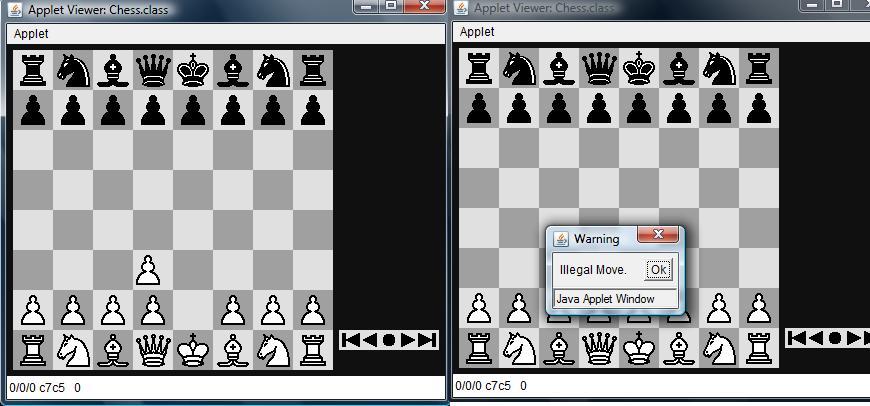
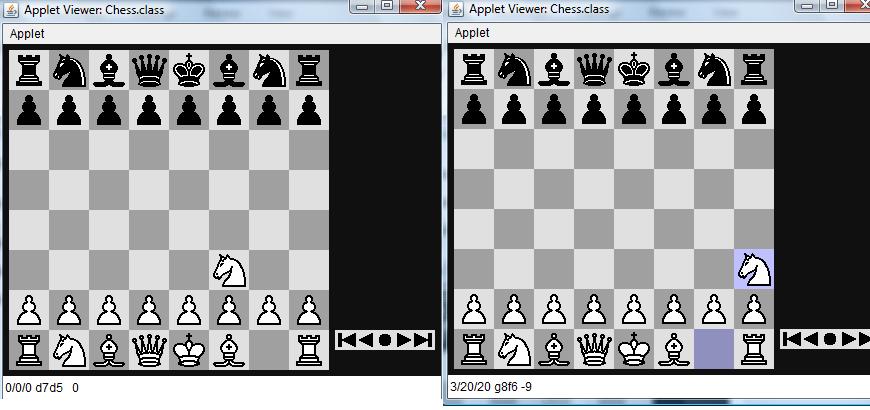
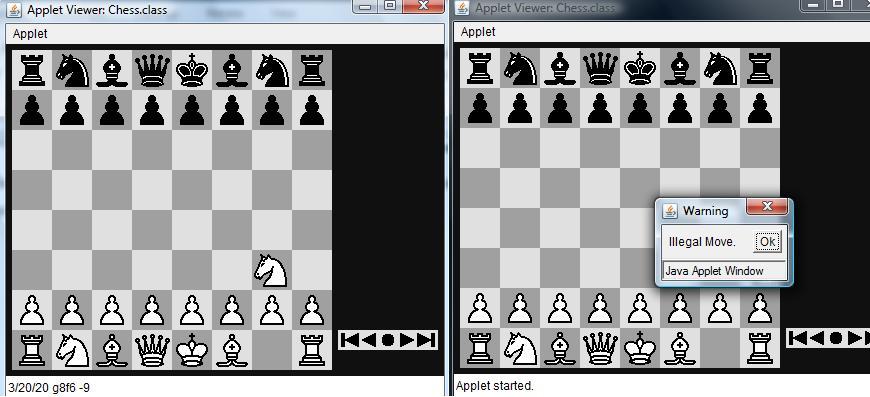
6.3 Sample outputs
- Conclusion
- Future scope
- References