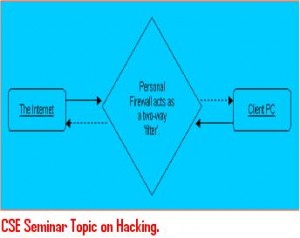
Java card seminar topic explains about developing a simple hardware and software application which is used for running any type of java projects using a simple sim card sized chip. This microprocessor chip contains integrated circuit inside it with some memory to store information. Developers who work on smart cards can stick to java card and run all applications which are developed in java and check applications in run time environment. Hardware applications which use small microprocessor memory can use these java cards. Developing java cards can improve java software programming usage in smart cards.
Java card seminar topic explains about developing a simple hardware and software application which is used for running any type of java projects using a simple sim card sized chip. This microprocessor chip contains integrated circuit inside it with some memory to store information. Developers who work on smart cards can stick to java card and run all applications which are developed in java and check applications in run time environment. Hardware applications which use small microprocessor memory can use these java cards. Developing java cards can improve java software programming usage in smart cards.
Java card technology helps developers to develop, test and deploy applications in a secured way. Developing applications in this model can reduce cost, increase efficiency and improve customer satisfaction. One of the best uses of this card is to integrate applications in to mobile, standard or enterprise editions without any work.
Integrated circuit is used for developing java card which will increase its use in personal security. This card can be used in the application where secure access and information security is important. This card can be used as portable device which can carry secure information like medical history, credit card number or electronic cash balances with high level of security.
download Seminar Report and paper presentation on Java Card Technical Seminar Report.