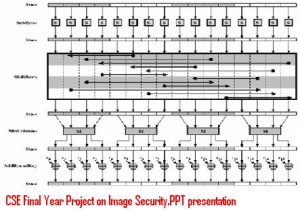
 Cryptography and Network Security Seminar Topic is for M.Tech computer science students. This seminar topic explains about secure data transferring between two nodes by encrypting text message at one end with a cipher code and decrypting same message with same code which was used for encrypting.
Cryptography and Network Security Seminar Topic is for M.Tech computer science students. This seminar topic explains about secure data transferring between two nodes by encrypting text message at one end with a cipher code and decrypting same message with same code which was used for encrypting.
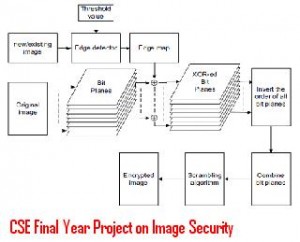
There is lot of scope for developing a application for implementing encryption algorithm for secure data transfer. This new cryptography application uses classic encryption techniques as mentioned below.Image encryption concept can be seen in Image Security seminar topic.
- User X will encrypt text information and send it to Y through internet.
- If we consider Z as a hacker who will try to decrypt text information but lack of crypto text it cannot be possible.
- When User Y receives text information he will decrypt using a key that was used while encrypting.
Requirement for secure conventional encryption.
► There must be a Secured encryption key.
► Key used for encryption must be with sender and receiver.
Conclusion.
After studying cryptography and security system we come to know that following ways:
Both are using to provide security of particular data.
By using the key that provided by the user can be decoded if some has the particular key of that data.
download paper presentation of CSE Cryptography and Network Security Seminar Topic.