Certificates Generation
For the process of authentication and key exchange we will be using digital certificates that have been generated by the Certificate Authority (CA). In our application we will be generating certificates using “Windows Server 2003” and the certificates generated by CA will be in a “.pfx” format, which is not supported by our application being generated on a Java platform which can only understands “.jks” format. For this reason after generation of the certificate in “.pfx” format we will be converting it in to “.jks” format using java’s command line tool I; e “key tool”.
In this section we are going to see the certificate generation and the extraction of public and private key pairs using “key tool”.
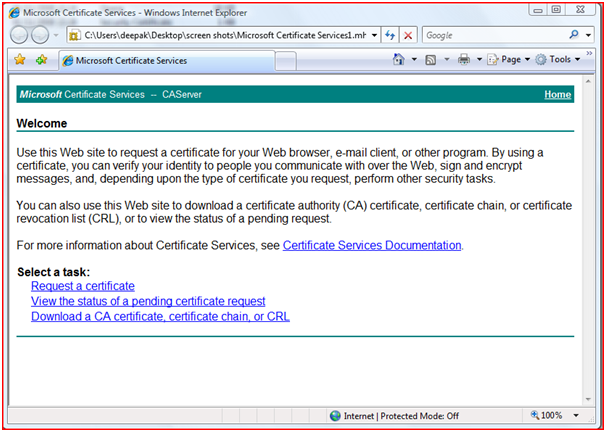
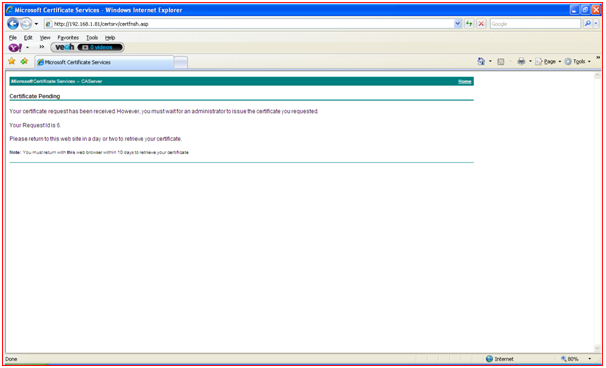
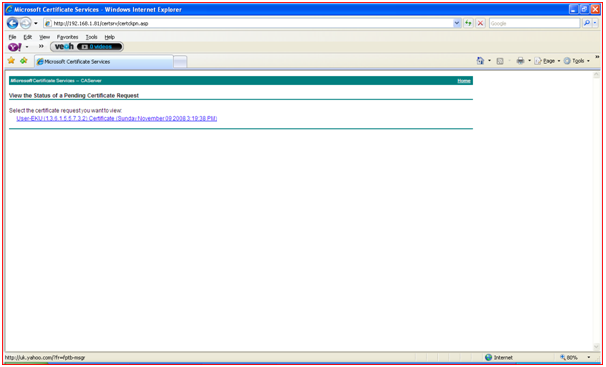
- Below screenshots shows the step-by-step request of certificate from the client system.
Figure 26: Requesting Certificate Step 1
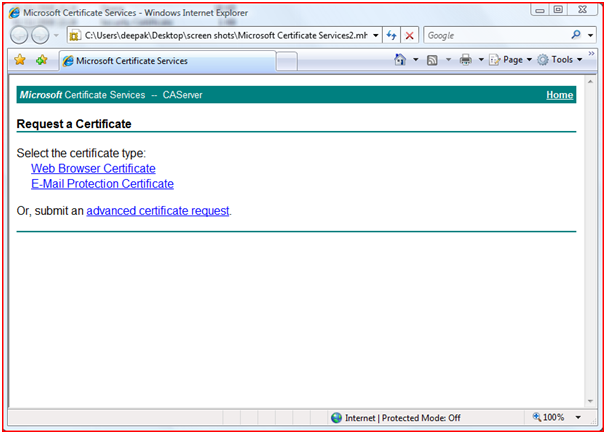
Figure 27: Requesting Certificate Step 2
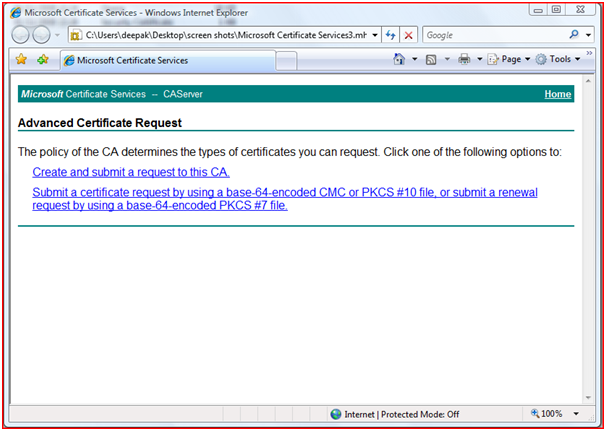
Figure 28: Requesting Certificate Step 3
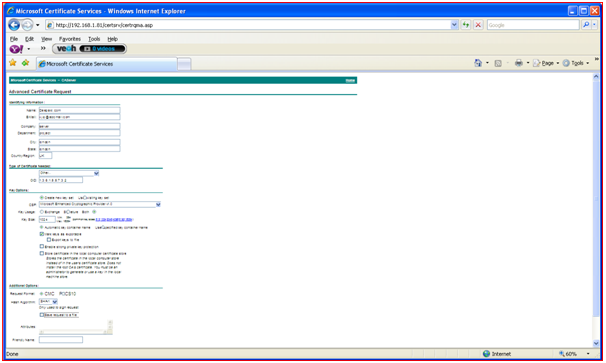
Figure 29: Requesting Certificate Step 4
Figure 30: Requesting Certificate Step 5
Figure 31: Requesting Certificate Step 6
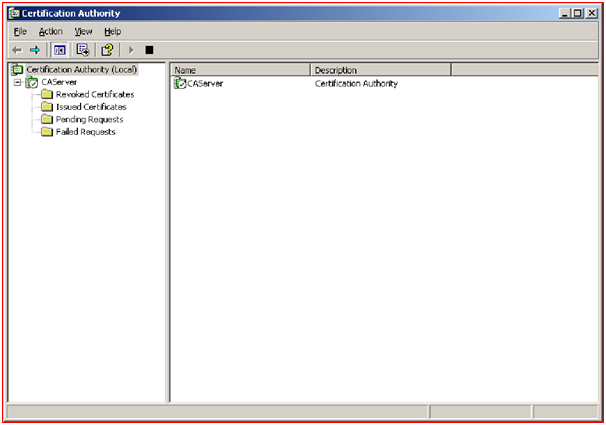
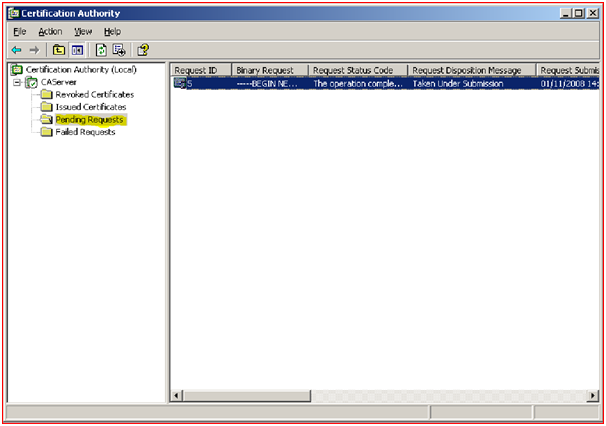
- When once the request has been sent to the Server, administrator of the network has to accept the request by observing the details send by the client. In the Server side it will maintain the details of the following certificates.
- Revoked Certificates.
- Issued Certificates.
- Pending Certificates.
- Failed Certificates.
Server will maintain the details of the Revoked Certificates and the details for the revocation for the future purpose.
Figure 32: Issuing Certificate
Figure 33: Showing Pending Certificates
Figure 34: Showing Issued Certificates
Conversion of Certificates:
The certificates that have been downloaded from the certificate authority will be in the “.pfx” format, which our Java application cannot understand and hence we need to convert this into “.JKS” format using command line Java key tool. From these converted JKS file key pair will be generated for both server and client.
This Project Paper is written & submitted by Deepak V.