This lacks standard interface for the low-level interaction. The characteristic affects the portability of used can be categorized as an ordinary system that can be used to detect only a known or ungeneralised set of users. The main drawback lies in the fact that the system cannot be generalized. The system acts as a subsystem of the firewall itself. The system contains the details of the intruder, which is then forwarded to the firewall.
Drawbacks
The system has no access to the data in the packets. The existing system only checks with the IP address of the arriving packets. It is possible to identify the intruder with the IP address and not with the contents of the packet. It sometimes happens that the data arrive with data that has the capability of hacking the information from the network. This is possible using certain keywords. The existing system fails to detect such intrusion. The existing system is a faster one as far as the performance is considered.
Benefits
The most important feature of the system is that the system can generalize the type of intrusion. Large amount of checking has to be done in the packets with the data stored in the adaptive model database.
Software Configuration:
FRONT END: VB.NET
BACK END: MS SQL SERVER
The output forms are: –
Intruder details display Form.
Adaptive modal display Form.
IP request Form.
Port scanning Form.
Ping Machine Form
TCP sniffing Form.
UDP sniffing Form.
All packet sniffing Form
Packet Detection Form
Data Mining Form
Active Machine Form
Instance Management Form
Instant Message Form
Reports Form.
Input forms are: –
Login Form.
Change Security Form.
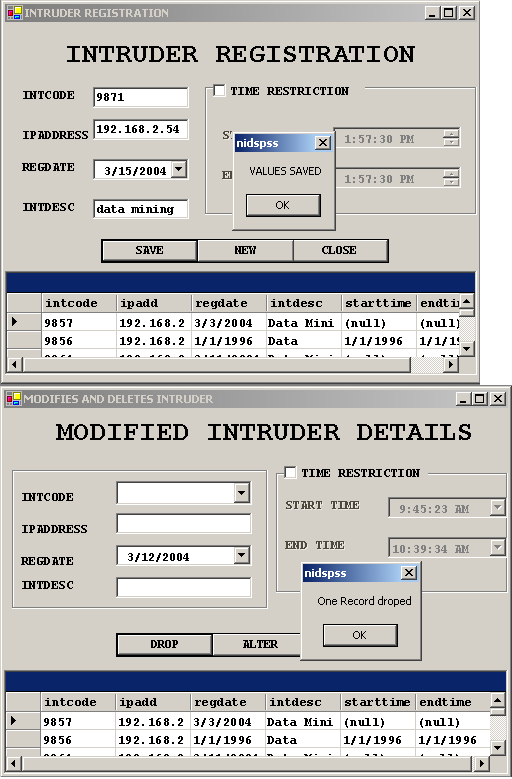
Intruder registration Form.
Intruder alteration Form.
Adaptive modal registration Form.
Adaptive modal modification Form.
Locking Form.
CONCLUSION:
The project ‘Network Intrusion Detection System’ is meant for providing security to a system by forwarding the validated packet details to the firewall.
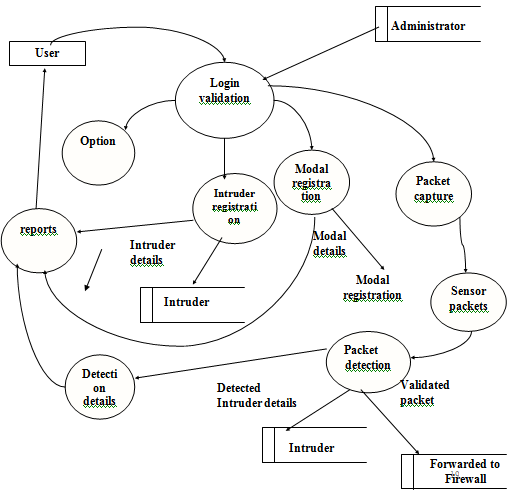
The current system has four modules.
Registration : To register intruders and data model details.
Sensor : For capturing raw data packets.
Detector : Detection of the intruder packet and forwarding packets to the firewall for blocking.
Options : Monitoring certain system details by the administrator.
The administrator, who is the only user, can monitor all the network traffic that is the packets arriving into the network filtering the protocol type that is whether the packet is TCP or UDP. The administrator can also find out which all are the intruder packets and can forward the message for blocking the packets to the firewall.
Considering the current trends and the developments the future might offer, this is a secure system with a promising bright future in the coming networking era.
TABLE STRUCTURE:
Table number : 1
Title : Administrator Login
Table Name : Login
Description : The table stores in the login user ID and the password for the authorization checking. It is used both during login and locking.
Constraint : The user ID is the primary key.
| Field name | Type | Length | Description |
| Username | Varchar | 25 | User Identification |
| Password | Varchar | 25 | User Password |
Table Number : 2
Title : Intruder Registration Details
Table name : Intruder
Description : The details of already known intruders
Constraints : The int code is the primary key, IP address not null.
| Field Name | Type | Length | Description |
| Intcode | Numeric | 9 | Intruder Code |
| Ipaddress | Varchar | 25 | Ip Address |
| Intdesc | Varchar | 25 | Intruder Description |
| Regdate | DateTime | 8 | Registration Date |
| Starttime | DateTime | 8 | Start Time |
| Endtime | DateTime | 8 | End Time |
Table number : 3
Title : Adaptive Model Table
Table name : Modal
Description : The Adaptive model is created and stored
Constraints : The modcode is the primary key
| Field name | Type | Length | Description |
| Modcode | Numeric | 9 | Model Code |
| Regdate | DateTime | 8 | Registration date |
| Pattern | Varchar | 200 | Model Pattern |
Table Number : 4
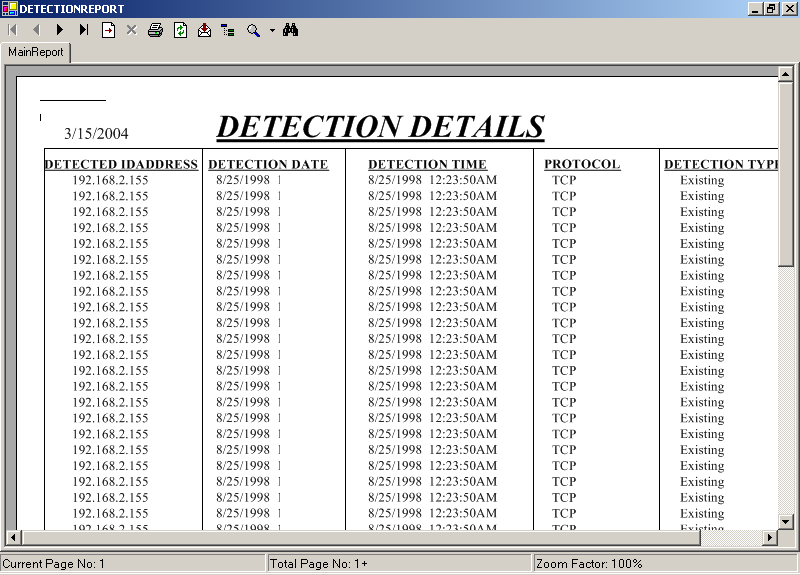
Title : The Intrusion block details
Table name : Detection
Description : The packets detected of intrusion are stored here.
Constraints : The Detipaddr is the primary key
| Field name | Type | Length | Description |
| Detipaddr | Varchar | 25 | Detected IP Address |
| Detdate | DateTime | 8 | Detection Date |
| Dettime | DateTime | 8 | Detection Time |
| Protocol | Varchar | 10 | Protocol |
| Dettype | Varchar | 25 | Detection Type |

Thanks 🙂
Hi,
I am not sure, how you could capture the packets into the database. I would love some more information on thiss. Its an awesome project.
please, i want to you to help me in completion of my project, the system i am developing is Intrusion Detection System or any other related system that is perfectly detected. please, with the used of java or c#. please, urgently.
Please…I want to hear from you to get the code and more assistance…please. I am waiting to hear your feedback.
Hello Sir,
I need this project code with report pls mail me link to Download this code… This is last year and i need this project coz this is unique.. I am a noob i dont know coding. Please sir its request..
Send me this project pleasssss…..
i need this project..
i dnt knw the coding so plz send me this project…plzzzz
mmmm you guys are good in coding I must admit. now sos
I need a vb.net intrusion detection code
please
Send me Source Code project pleasssss….. <3
i need the coding
can i have the coding in either c++,vb or java?
May I please the source code
hello, its an amazing project. i need ur assistance in completimg my project which is similar to yours. can you please provide ur source code..
Good day sir, please I would like to have a copy of this project for my defense. Don’t know if u can send me d download link.thanks
may i please have the code for this… it’s quite important
can i get a source code and algorithms for this project its really good man
Can i get the code and algorithms
I too need coding . Could you please provide me?
i want this source code. please send the link
hello sir, its an amazing project. i need ur assistance in completimg my project which is similar to yours. could you please provide ur source code and algorithm ?
Can I get the source code