Intrusion detection in Wireless Sensor Network Java Project is for computer science final year students.This project main idea is to trace moving objects which will be useful in fields like military and aviation.This application can be useful in battle field in order to find out moving objects.
Data transfer is done using wireless sensor network. This application is implemented using two sensor detection models :single sensing and multiple sensing detection. This project will show advantages of multiple heterogeneous wireless networks.
Existing System:
1) In present existing system single sensing detection is used where only one object is detected for a single time in wireless sensor network.
2) Our Previous work was according to homogeneous and heterogeneous single sensor in wireless sensor network
1) In Heterogeneous wireless sensor ,Intruder detected anywhere in the network.
2) We are detecting the intruder in multiple sensor heterogeneous wireless sensor network.
Modules:
1) Constructing Sensor Network
2) Packet Creation
3) Find authorized and un authorized port
4) Constructing Inter-Domain Packet Filters
5) Receiving the valid packet
Modules Descriptions:
Module-1:
In this module, we are going to connect the network .Each node is connected the neighboring node and it is independently deployed in network area. And also deploy the each port no is authorized in a node.
Module-2:
In this module, browse and select the source file. And selected data is converted into fixed size of packets. And the packet is send from source to detector.
Module-3:
The intrusion detection is defined as a mechanism for a WSN to detect the existence of inappropriate, incorrect, or anomalous moving attackers.
In this module check whether the path is authorized or unauthorized. If path is authorized the packet is send to valid destination. Otherwise the packet will be deleted. According port no only we are going to find the path is authorized or Unauthorized.
Module-4:
If the packet is received from other than the port no it will be filtered and discarded. This filter only removes the unauthorized packets and authorized packets send to destination.
Module-5:
In this module, after filtering the invalid packets all the valid Packets will reach the destination.
CONCLUSION.
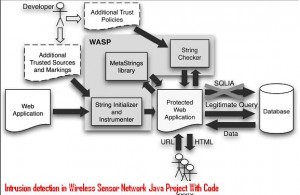
This paper presented a novel highly automated approach for protecting Web applications from SQLIAs. Our approach consists of
1) Identifying trusted data sources and marking data coming from these sources as trusted,
2) Using dynamic tainting to track trusted data at runtime, and
3) Allowing only trusted data to form the semantically relevant parts of queries such as SQL keywords and operators.
Unlike previous approaches based on dynamic tainting, our technique is based on positive tainting, which explicitly identifies trusted (rather than untrusted) data in a program. This way, we eliminate the problem of false negatives that may result from the incomplete identification of all untrusted data sources.
False positives, although possible in some cases, can typically be easily eliminated during testing. Our approach also provides practical advantages over the many existing techniques whose application requires customized and complex runtime environments: It is defined at the application level, requires no modification of the runtime system, and imposes a low execution overhead.
download Project Report,Code and paper presentation of CSE Intrusion detection in Wireless Sensor Network Java Project .

Can i get the complete source code for hacker detection in heterogeneous wireless sensor network in java
can u please provide entire source code please