This system is used to make security professional aware of packets entering and leaving the monitored network. It is used to sniff out the network packets. It helps to increase packet throughput as inspecting every packet can slow traffic considerably. It is an essential tool that compliments any security suite such as firewall and a good antivirus.
Large amount of checking has to be done in the packets with the data stored in the adaptive model. The system uses up LAN bandwidth. It has double the total network bandwidth requirements from any LAN. The system is more adaptable to cross platform environments.
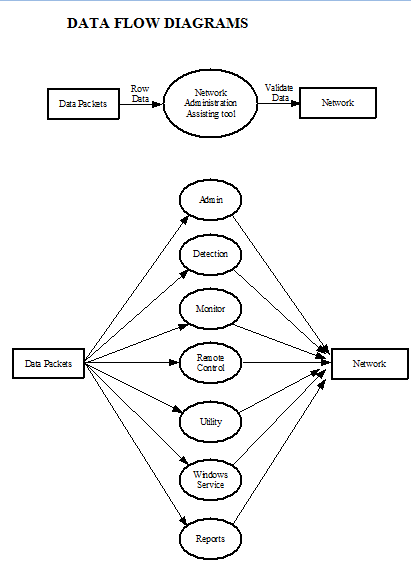
The important modules of the system are:
- Admin
- Detection
- Monitor
- Remote Control
- Utility
- Recovery Service
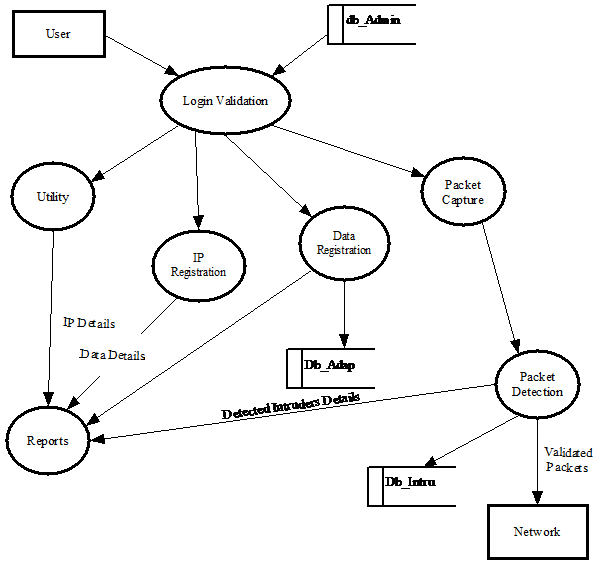
Admin: Administrator registers the intruder’s known IP addresses and the harmful data.
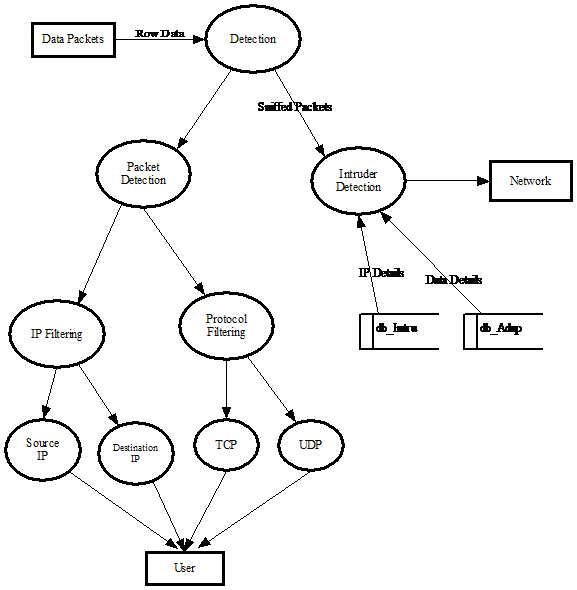
Detection: Packets are detected comparing the IP address and data table.
Monitor: Pinging and shortest path is found.
Remote Control: Shut down, Restart and log off activities are done.
Utility: Change password, locking the application in server system and Sending messages is done.
Recovery service: Backups of the data running in client machine is maintained.
INTRODUCTION
NETWORK ADMINISTRATOR ASSISTING TOOL
The project named “Network Administrator Assisting Tool” is a system that not only detects the intruders by IP address; it detects the system with its contents also. It is used to sniff out the network packets. It helps to increase packet throughput as inspecting every packet can slow traffic considerably.
Large amount of checking has to be done in the packets with the data stored in the adaptive model. The system uses up LAN bandwidth. It has double the total network bandwidth requirements from any LAN. The system is more adaptable to cross platform environments.
Aim:
The proposed system can be used to attain information relating to network. It can be used to retrieve the information regarding the current systems in the network, the ports in use, locking the system etc. The system is first fed in with the currently available intruders and the kind of data that are to be kept out of network. Information once is stored into the system is used to check the data packets. The IP addresses that are registered are forwarded to the firewall once found among the packets. The case is different with the adaptive modal. The unwanted type of data that are stored in the adaptive modal database is compared with the data that is passing through the network. On finding any packet that contains any of the contents of the adaptive modal database they are registered as intruders and the information is stored in the database.
SOFTWARE SPECIFICATION
Platform: Windows 2000/XP
GUI Tool: API
Environment: C#.NET
Database: Microsoft® SQL Server™ 2000
SYSTEM STUDY
DETAILED STUDY
The most important feature of the system is that the system can generalize the type of intrusion. Large amount of checking has to be done in the packets with the data stored in the adaptive model database.
Features
- The system proposed can be used to attain information relating to the network
- It can be used to retrieve the information about the current systems in the network, the ports in use, locking the system etc.
- The proposed system can be used to get the shortest path for the packet from source to destination.
- The system is used to monitor currently active machines in the network and with that admin can logoff, shutdown or restart the system from the server machine.
- The system can take the backups from the client machine and restore it back to the client machine.
- The system is first fed in with the currently available intruders and the kind of commands that are to be kept out of the network. Information once is stored into the system is used to check the data packets. The IP addresses that are registered are forwarded to the firewall once found among the packets.
- The case is different with the adaptive modal. The unwanted type of data that are stored in the adaptive modal database is compared with the data that is passing through the network. On finding any packet that contains any of the contents of the adaptive modal database they are registered as intruders and the information is stored in the database.
EXISTING SYSTEM
Drawbacks of existing system
- The existing system does not provide proper security over the network.
- It needs manual processes to stop the intruder.
- Administrator has to be in front of the system all the time.
- Since the existing system does not have any details about the hosts, an unauthorized access cannot be detected easily.
- The intruder cannot be found at appropriate time and blocked.
- The existing system does not use any shortest path algorithm, so that it takes a large amount of time to transfer data packets from one host to another.
- Cannot ensure whether the packet has been send are received at the destination.
- The server application can be used by an unauthorized user as the existing system does not provide the facility of locking the application.
- It does not provide activities such as shut down, log off and restart.
PROPOSED SYSTEM
The project named “Network Administrator Assisting Tool” is done by using C#.NET as a Frontend and SQL Server as a Backend. This system compliments any security suite such as firewall and antivirus. The system not only detects the intruders by IP address; it detects the system with its contents also. The system checks the database for the already registered intruders. If found intruding, they are forwarded to the firewall for blocking. The firewall is responsible for the blocking of the packets.
The proposed system can be used to attain information relating to network. It can be used to retrieve the information regarding the current systems in the network, the ports in use, locking the system etc. The system is first fed in with the currently available intruders and the kind of data that are to be kept out of network. Information once is stored into the system is used to check the data packets.
The IP addresses that are registered are forwarded to the firewall once found among the packets. The case is different with the adaptive modal. The unwanted type of data that are stored in the adaptive modal database is compared with the data that is passing through the network. On finding any packet that contains any of the contents of the adaptive modal database they are registered as intruders and the information is stored in the database.
Benefits of proposed system:
- User friendly
- Ease of access
- Fast retrievals
- Single point system administration and maintenance
- Added security to system
- Can be implemented in network
- Easy to mention an IP address.
DATABASE DESIGN
The database design is a must for any application developed especially more for the data store projects. Since the chatting method involves storing the message in the table and produced to the sender and receiver, proper handling of the table is a must.
In the project, login table is designed to be unique in accepting the username and the length of the username and password should be greater than zero.
The complete listing of the tables and their fields are provided in the annexure under the title ‘Table Structure’.
Admin
Table Name : Admin
Purpose : Maintain Host In formations and Login Details
Table Structure :
| Field | Data Type | Length | Description | Key |
| Hip | Var char | 20 | Host IP | Primary |
| Hname | Var char | 20 | Host Name | |
| Passwd | Var char | 29 | Pass word | |
| Ltime | Date/Time | 10 | Login Time | |
| Ldate | Date/Time | 10 | Login date |
Adaptive Model
Table Name : Adaptive model
Purpose : Maintain Packet Informations
Table Structure :
| Field | Data Type | Length | Description | Key |
| Hip | Var char | 20 | Host IP | Foreign |
| Tdata | Var char | 20 | Type of data | |
| Size | Numeric | 10 | Size of data |
Intruder Registration
Table Name : Intruder Registration
Purpose : Maintain Intruder Information
Table Structure :
| Field | Data Type | Length | Description | Key |
| Iip | Var char | 20 | Intruder IP | Primary |
| Rtime | Date/Time | 10 | Reg Time | |
| Rdate | Date/Time | 10 | Reg Date | |
| Tdata | Var char | 20 | Type of data |
Intruder Blocking
Table Name : Intruder Blocking
Purpose : Maintain Intruder Blocking Informations
Table Structure :
| Field | Data Type | Length | Description | Key |
| Iip | Var char | 20 | Intruder IP | Foreign |
| state | Boolean | 10 | State |
Backup Process
Table Name : Backup
Purpose : Maintain Backup data
Table Structure :
| Field | Data Type | Length | Description | Key |
| Hip | Var char | 20 | Host IP | Foreign |
| Dip | Var char | 20 | Dest IP | |
| Tdata | Var char | 20 | Type of data |
Remoting
Table Name : Remote
Purpose : Maintain Remote Process Information
Table Structure :
| Field | Data Type | Length | Description | Key |
| Hip | Var char | 20 | Host IP | Foreign |
| hname | Var char | 20 | Host name | |
| actionp | Var char | 20 | Action perf | |
| actiont | Date/Time | 10 | Action time | |
| actiond | Date/Time | 10 | Action date |
Monitoring
Table Name : Monitor Table
Purpose : Maintain Ping, Port scanning and Route Tracing
Information
Table Structure :
| Field | Data Type | Length | Description | Key |
| Hip | Var char | 20 | Host IP | Foreign |
| Dip | Var char | 20 | Dest IP | |
| Ctime | Date/Time | 10 | Conn time | |
| Cdate | Date/Time | 10 | Conn date | |
| Spath | Numeric | 10 | Shortest path | |
| Portno | Numeric | 10 | Port number | Primary |
CODE DESIGN
The code design should be such that with less amount of coding we can achieve more results. The speed of the system will be more if the coding is less. Whether the data in the system is usable and readable by the system is depending on the coding.
In the project, the coding is being done such that proper validations are made to get the perfect input. No error inputs are accepted. In addition care is taken such that the data integrity and referential integrity is not violated in the database.
Checking the username and password, non-acceptance of duplicate username is made properly.
In addition, coding is designed such that concurrency avoidance of accessing the database, limited user access to the table is made perfect. The coding is designed such that the consumer can view only his complaints.
OUTPUT DESIGN
Output Forms are,
- Intruder Details Display Form.
- Adaptive Modal Display Form.
- IP Request Form.
- Port Scanning Form.
- Ping Machine Form.
- TCP Sniffing Form.
- UDP Sniffing Form.
- All Packet Sniffing Form.
- Packet Detection Form.
- Data Mining Form.
- Active Machine Form.
- Instance Management Form.
- Instant Message Form.
- Report Form.
SYSTEM DEVELOPMENTS
The important modules of the system are:
- Admin
- Detection
- Monitor
- Remote Control
- Utility
- Recovery Service
Admin
In this module administrator registers the intruder’s known IP addresses and the harmful data. The full control for the system is in admin and in this module administrator can update the IP as well as the modal data of the intruder.
Detection
This module detects the packets and it schedules the packets as TCP and UDP packets. Then it checks the data packets and the IP address. If any intruder or harmful data is there the system detects it.
Monitor
It lists all the processes and the error that is occurring and stores it in the database. Pinging is done and shortest path is found.
Remote Control
In this module, Administrator can find out all the active machines in the network. Administrator can then perform remote control activities such as shut down, Restart and log off according to the need.
Utility
Administrator can do the utilities like change password, lock the application in server system, and sending messages to the network.
Recovery service
Administrator can take backups of data, which are running in the client machine. Whenever the data is needed the data can be recovered and also can schedule the time.
CONCLUSION
The Remote Monitoring System project can be thus found to be useful in various applications in both home use as well as office use to detect unnoticed malpractices in our system. Thus it makes the user to be careful about the improper usage of his system thus enabling him to take appropriate actions to stop them. Hence he can have a control over his system even in his absence. Hence it provides a level of security to the administrator’s PC. Remote Monitoring System is a powerful monitoring and surveillance tool that is useful on all platforms. This project helps us in a networking environment to monitor and spy all the system in the network connection without knowing the user.


Can u upload source code.
Please i need this project with its source code
please healp me
Pls I want source code