APPLICATION TESTING
Application testing is done within the same network using two systems, which are connected to the network. This is done by using ethereal tool known as wireshark (http://www.wireshark.org/download.html) which captures the packets over the network.
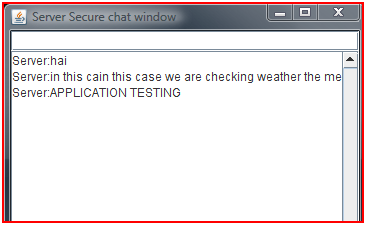
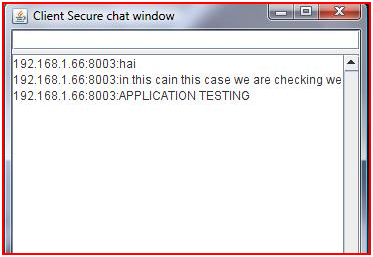
Test Case1:- In this case we are checking weather the messages are transferred from the correct source, completely inspite of the length of the message. This is shown in the screenshots below, where Server (192.168.1.66.8003) and client (192.168.1.69) are executed on two different systems. Which shows the Integrity one of the main aim of our application.
Figure : Integrity at Server Side
Figure : Integrity At Client Side
With the following screenshots shown above it is shown that the messages have been transferred completely with out any eavesdropping.
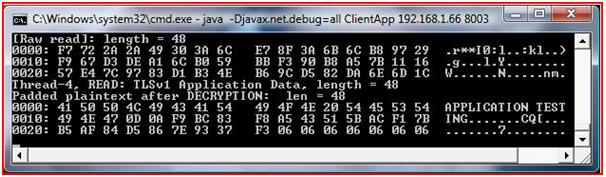
Test Case 2:- In this case we will test the Encryption/Decryption of the application using ethereal tool (wireshark) which captures the network layer packets. We will be testing this case for the message that has been sent in the previous case.
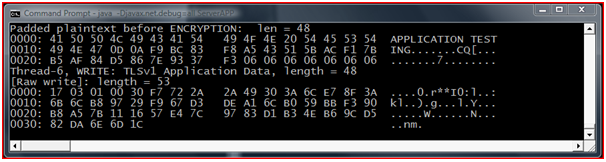
Figure : Test Case 2 Server Side
In this screenshot it is showing the server side message been encrypted and written on Thread 6 for transferring over a network.
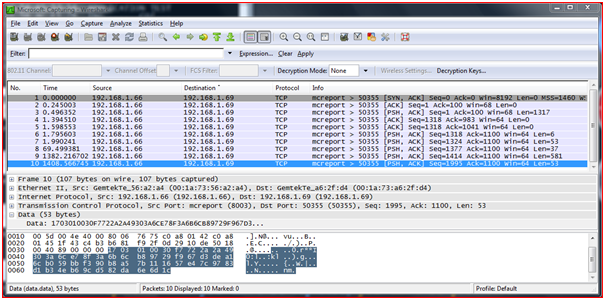
Figure : Ethereal Testing In Wire Shark
In the above screen it is the ethereal tool showing the encrypted data I;e transferring over the network and the source(IP and Port num) and destination (IP and Port num).
Figure : Test Case 2 Client Side
This is the client side message showing the encrypted message being read from the socket and decrypted message same as the Server side.
Test Case 3:- Final test case which is the most important part of our application is providing Authentication. In our application we are providing authentication with the help of certificates. These certificates containing the Server/Client key pair are imported and stored in a key store with a password, in case of giving wrong passwords by the intruder the application can not be executed as the authentication fails.
This Project Paper is written & submitted by Deepak V.