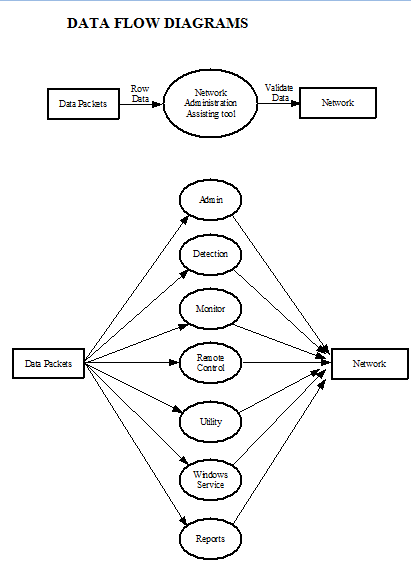
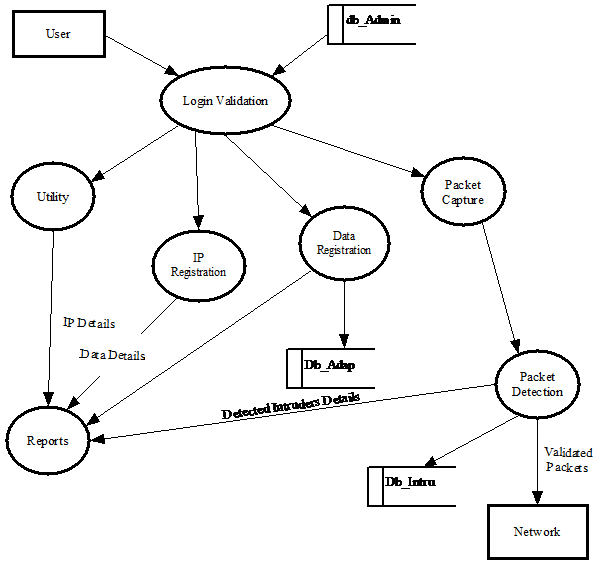
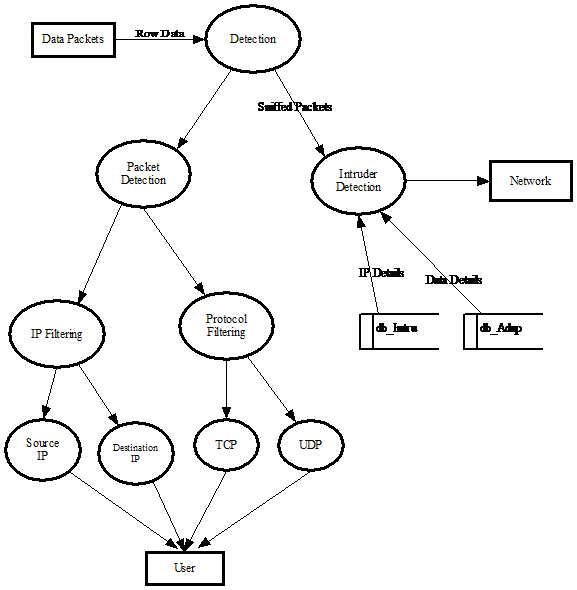
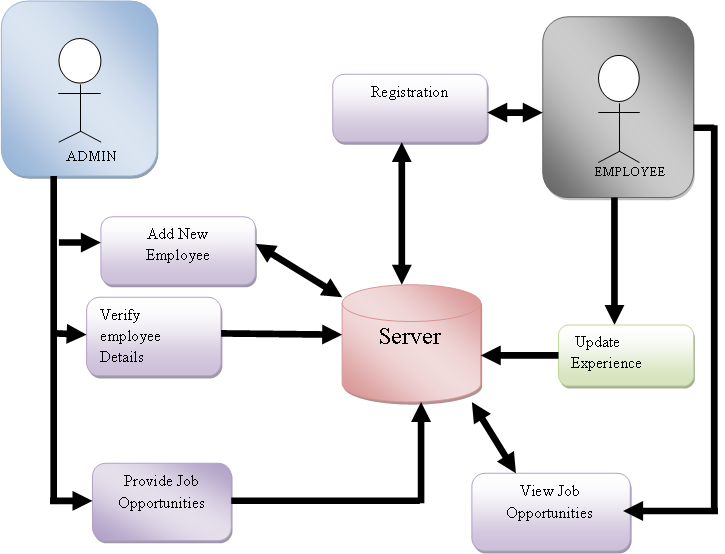
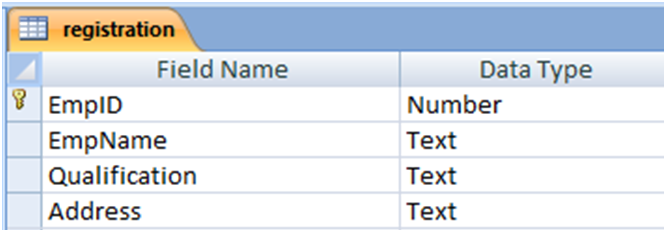
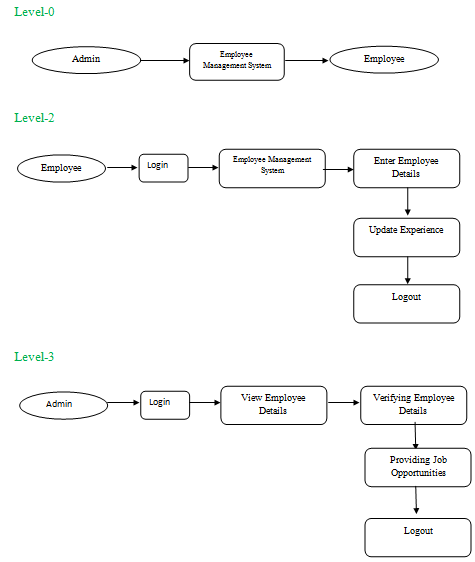
IDENTIFICATION OF NEED:
PROCESS IN EXAMINATION BEFORE THE EVOLUTION OF THE EIS SYSTEM:
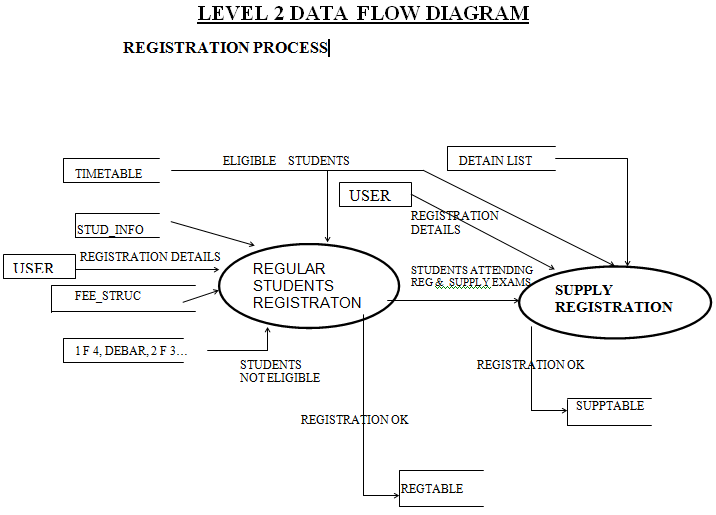
The whole process starts from registration of the candidate for the exam. Registration contains information related to students like
- Registration number
- Name
- Branch
- Year
- Exam Fee details…
After the registration is completed a list of students who have registered will be issued application forms. Filled up applications are sent to the university by the college exam cell incharges. Then after some time basing on those applications, STUDENTS details year-wise, branch-wise, regular/supply, subject-wise, are stored in the system. Students get the hall-tickets along with the details of exams they are appearing and the concerned dates.
Details of conduct of examination:
The university in Net displays the timetable of examinations and by that the students are allowed to attend the examinations basing on the schedule. STUDENT’s details date-of-exam-wise should be taken.
Seating order-Arrangement:
Seating arrangement depends on the number of students appearing for a particular exam and the capacities of the examination halls.
Based on date of exam, Branch, Subjects, Years, Regular/Supp/Transfer
=> Number of students of each exam are sorted in order.
Sorting Order:
Based on date of exam, Branch, Subjects, Years, Regular/Supp/Transfer
=> Number of students of each exam are retrieved.
Then they are sorted as explained below:
- Students attending regular exam are followed with supplementary students (if any) attending the same exam.
- Supplementary students are further sorted in increasing order based on their current year of study.
- Each batch of students (reg/supp) are in turn sorted as below :
Regular students followed by lateral entry students (if any) and
transfer candidates (if any).
In this seating arrangement we have to consider various hall capacities like
- 24
- 36
- 74
- 48 (with combination in 24)
and in this seating arrangement process students can be arranged with or without combination.
Combination of students can be made in a hall only when the subjects to which they are appearing are different.
Depending on sets allotment we have to check for seating conditions like:
No two members of same year and same set and same branch should sit adjacent (side by side or across) to each other.
Sets Allotment:
Question paper set allotment will be done for the sorted students with the starting set number mentioned by the JNTU.
Manually the set numbers are represented corresponding to their register number in the seating arrangement form. All the above data is fed into Excel sheet.
Nominals and Additional Sheet Forms:
After the seating arrangement nominal rolls and additional sheet forms will be generated for the respective exam halls from seating arrangement database .
In nominal form we have the columns:
- Register number with corresponding register number
- Set number
- Signature
In additional sheet form we have the columns:
- Register Number
- Main sheet no. of student
- Number of additional sheets taken
- Signature
These nominal rolls and additional sheet forms provide further fields
like : number of students in that hall, number of students present and number of students absent.
The filled-up information in Nominal rolls will be manually verified by the invigilators and the chief superintend. Finally this information is again updated in absentees statements which is a D-FORM.
D-Form:
In D-form students list of a particular branch/exam are grouped according to set allotment done and this list is further sorted in order as per seating arrangement.
The absentees for that exam in that list are obtained from nominal rolls and corresponding register numbers are manually rounded.
Total number of students registered, number of students present in each set are further details provided by D-Form.
RISKS INVOLVED IN EXISTING SYSTEM:
Present system is time consuming and involves lot of paper work.
The risks involved in present system are due to its manual effort of collecting required data and summarizing them for report generartion.
Some of the risks involved in present system are:
- Student can register only when he/she is eligible for that.
Ex: If the student has attendance less than required percentage then he is
not eligible to register.
Many conditions like these are being checked manually before
registration, which is time consuming and error prone.
- In allotting sets, if a mistake is done at a point, then this becomes cumulative and this may result in adverse consequences.
- By mistake, in D-Form if a student present is marked as absent, confusion occurs in evaluation process.
- If there is any need to retrieve any details, it may seem to be difficult to search manually.
There are many other risks involved that can be easily tackled by computerizing present system.
PRELIMINARY INVESTIGATION:
PROPOSED SYSTEM
Examination Information System [EIS] is the computerized system. Which will automate all the process that is going on in the present system. The main aims for going to computerized system is
- Fast processing
- Less paper work
- Robust
- Adaptable
- Intuitive
- Easy retrieval
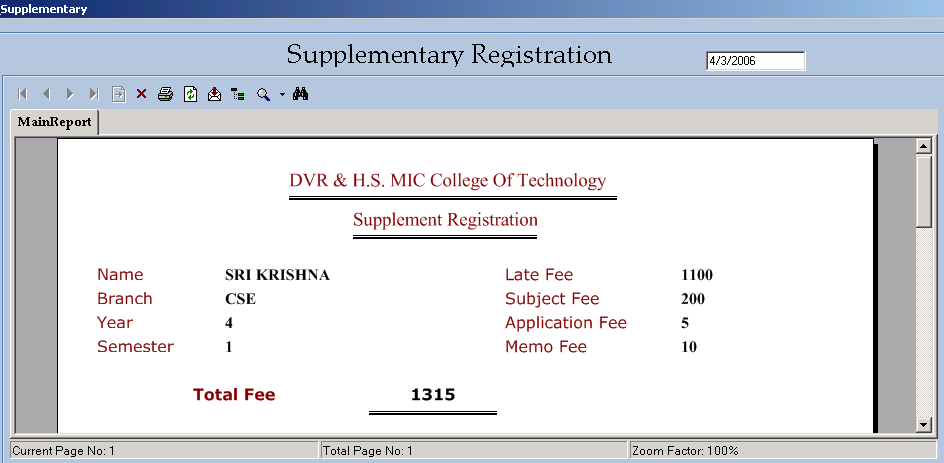
Registration:
This process starts from Registration process and in this registration we fill the details of the candidate like:
- Name of the student
- Register number
- B-tech or M.C.A
- Year of study
- Regular / supplement
Just before getting registered the student is checked against enrollment database, attendance database, debar list,1f4 and many other databases.
Thus only the eligible students can register.
Based on the entered criteria, fees gets automatically calculated and fees slip gets generated. If there are any changes made in fee structure by JNTU, due to the flexibility provided they can be easily reflected back in fee calculation.
The fee structure will be different for regular and supplementary. As per present fee structure, if regular he/she should pay the total amount of Rs.815 and if it is supplement he/she should pay the amount of Rs.200 for every subject and this should be verified against previous marks database.
Sets Allotment:
We allot sets for the students with the starting set number mentioned by the JNTU people and programatically the sets will be allocated to the sorted students and forms will be generated accordingly.
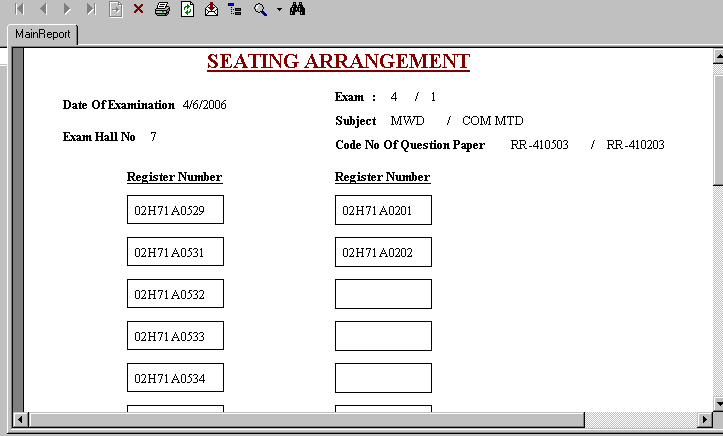
Seating Arrangement:
After completion of set allotment we get into seating arrangement. The seating arrangement consists of with/without combination of students we have to check for conditions like no two members of same year and branch should sit side by side.
There are varieties of seating arrangements:
- 24
- 36
- 74
- 48 (WITH COMBINATION)
By mistake, if the user chooses the same subject students for combination in the same hall, then the process restricts the user by giving a meaningful message.
Depending on number of students we categorize them in that particular room selected and we will store the placing of the students in base database that will be useful for automatically generating two forms namely,
- Nominal Rolls
- Additional sheet forms
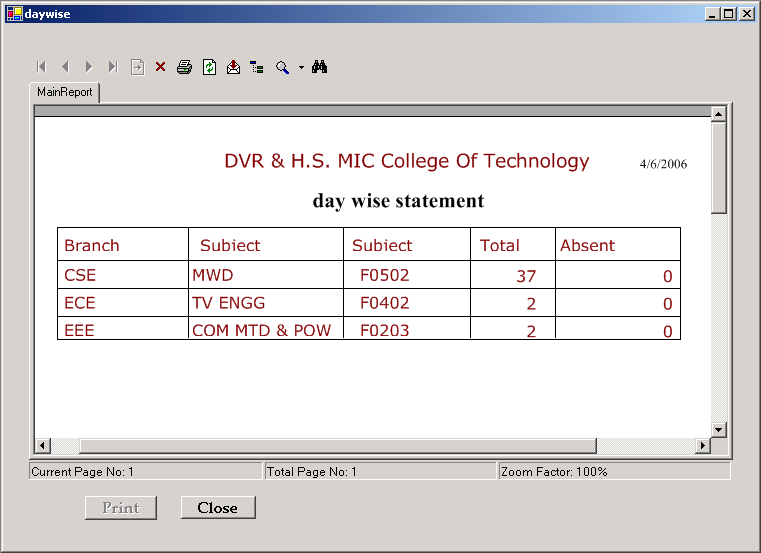
D-Form:
D-form gives the whole details or status of the class, and the absentees will be marked with red color automatically by checking register numbers against absentees database.
Total students are grouped automatically based on set allotment database
and then the calculations like no. of students present, absent per set are done and reflected back in report.
This D-form will be sent to JNTU examination cell to inform status of the student.
FORMS

REPORTS:
CONCLUSION:
The Student Enrollment System is aimed to automate examination system of a college. The total system, which was planned and designed to develop is vast in nature and functionality. The system is user friendly and intuitive and can be used even by novice users.
Though there was much that can be developed apart from what has been attempted, there were number of occasions on which new thoughts about various aspects of the project have been projected by the observers of the project, the duration of the project was considered to be a limiting factor for curtailing further previews and implementations.
The hope is that the project will be a major commercial product when the gaps leftover in the development are filled and a full-fledged project is built from the analysis and design that has been done during the project.