Authentication:
If a message conveyed by the authenticity is received by the sender, then it is indicated that sender identity is assured. That means assurance for the sender identity is provided by authenticity. The authenticity requirement is converted into two more requirements on the key of secure multicast.
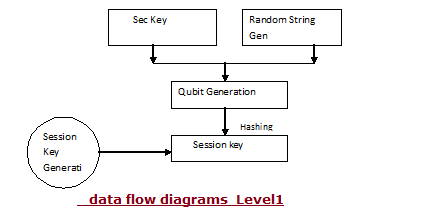
The flow of the application is briefly described using the data flow diagrams represented below: Level1
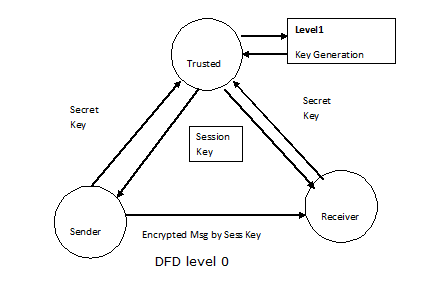
Level 0
Fig: DFD level 0
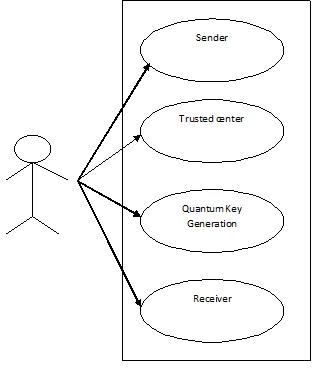
The sample use case diagrams to the application are as follows:
Fig: Use case view of the application
Fig: class diagram of the application
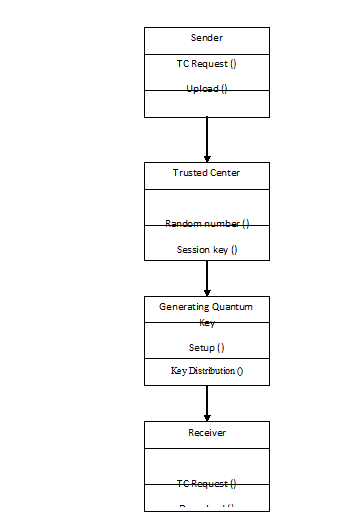
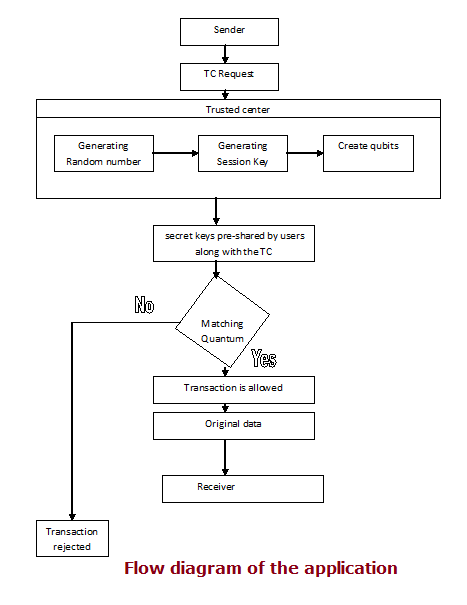
The flow diagram of the entire application is represented below:
Fig: Flow diagram of the application
This Paper is written & submitted by Vamshidhar A.