Existing System:
- Due to wireless nature, the malicious nodes can easily gain access with the wireless links
- Once the malicious node gain the access, they can interrupt the data communication
- The malicious nodes can overhear / overwrite / manipulate / drop the packets
- These malicious nodes degrades the network performance.
Proposed System:
- In order to detect malicious nodes, we have proposed an ID-based light-weight cryptographic protocol using authentication technique.
- This is light-weight mechanism, which means no complex calculations are required.
- The proposed technique works on the cryptographic one-way hash function and doesn’t include any cryptographic high computation operations like pairing as well as exponentiation.
- In this method, some random nodes are assumed as Temporary servers.
- Each node in the network possess an unique ID
- The sender node generates a key pair and send the data to Temporary server.
- This server verifies the sender authenticity and transmit the data to receiver.
- If the authenticity is not valid, then the sender node would be marked as MALICIOUS .
Enhancement:
- In order to segregate attackers from participating in network activities in future, we are proposing a CERTIFICATE REVOCATION method.
- According to this, the network is divided into different clusters and CH nodes are elected.
- These CH nodes keep maintaining of the Certificates / keys of each its member nodes.
- if any node found as MALICIOUS, then the node’s certificate would be immediately revoked.
- without a valid certificate / keys, the malicious nodes cannot communicate with the network in future.
Simulation Results:
A cluster-based certificate revocation scheme is able to revoke malicious nodes certificate quickly on the basis of only one vote from the neighbor. In this system, CA maintains two different lists, warning list and black list, to keep track on the malicious nodes so as such nodes cannot take part in certificate revocation.
Graphs:
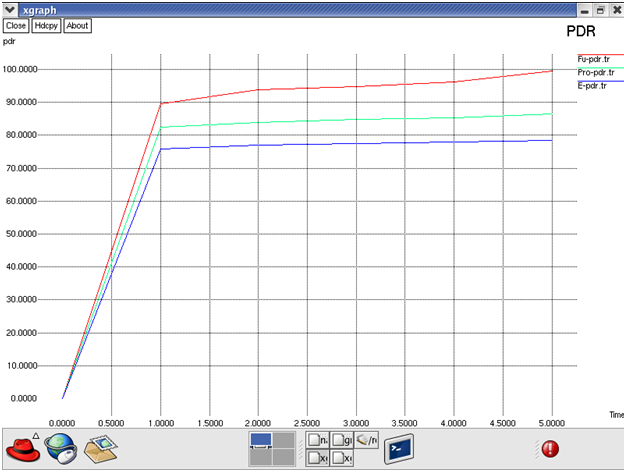
Fig: PDR
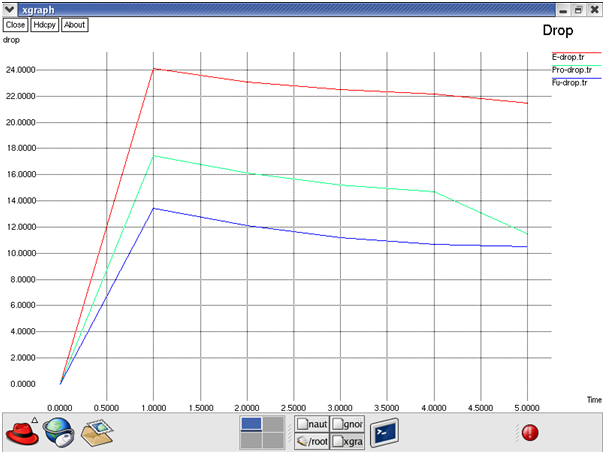
Fig: Drop
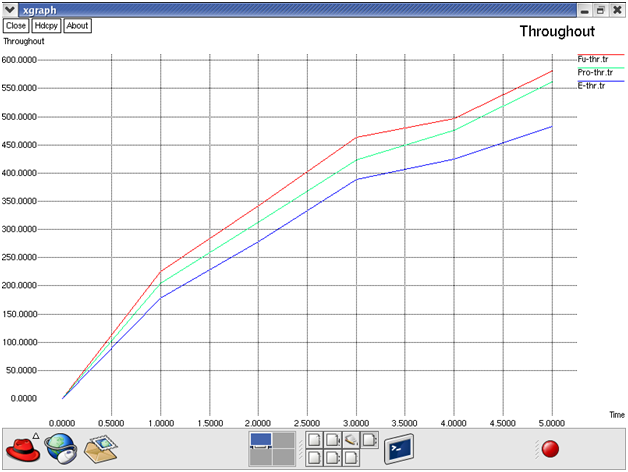
Fig: Throughout
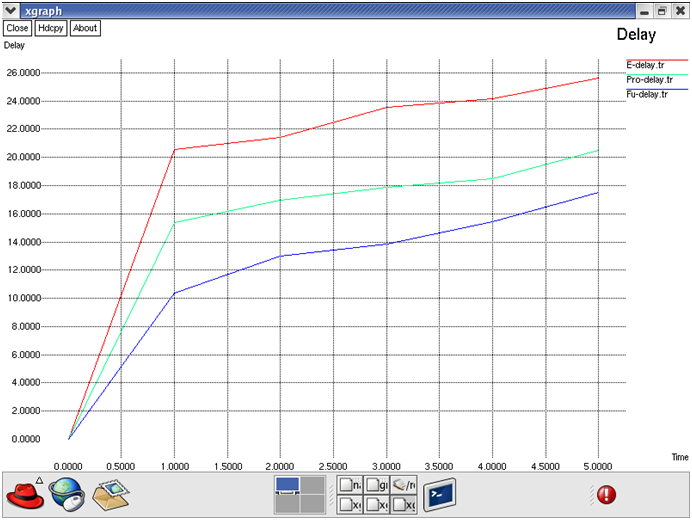
Fig: Delay
Hardware Requirements:
System: Pentium IV 2.4 GHz.
Hard Disk: 50 GB.
Floppy Drive: 1.44 Mb.
Monitor: 18 VGA Color.
Mouse: Logitech.
Ram: 2048 Mb.
Software Requirements:
Operating system: Ubuntu 14.04/Red Hat Linux9/Linux Mint
Coding Language: otcl, c++
Tool: Ns-2.34/Ns-2.35
Download This Improving Robustness in AD-HOC Network by Detecting Malicious Node NS2 project Code