INTRODUCTION:
The purpose of this document is to define scope and requirements of an application to detect anomalies in the expense approval system hosted on the Intranet of a leading business house.
Increasing volumes of the expense claims due to wide operations required controls so that the unscrupulous employees don’t get a chance to forge claims and get away with undue claim re-imbursements.
IT team proposed a tool based on Benford’s law to scan the past approved expense claims and detect potential frauds for further manual investigation using the said distribution.
This document is the primary input to the development team to architect a solution for this project.
System Users:
The pre-audit team and the approving managers (supervisors) of expense claim will benefit from using Fraudulent Expenses Detection System, DETECT.
Assumptions
1 . The application will be hosted on the intranet server as part of the expense claim framework. The users will access the application from Audit menu in
the application.
2 . The transaction data of expense claims for at least 6 months shall be uploaded into the system from the backend in CSV format. To simplify the
scope of this project, it can be assumed that each claim has fields viz. (a) claim id, (b) date, (c) employee’s name, (d) supervisor’s name, and (e)
claimed amount. In real life, such data will reside in multiple tables.
3 . Since DETECT is expected to use Intranet’s authentication, for the purpose of this project, entering user name will take you to the user’s DETECT
screen. You may create sample users directly from the backend database
REQUIREMENTS:
DETECT allows the pre-audit team to run this application for a transaction period.
Basic System Operation
The following steps outline the basic system operation in context of the end-user:
Detect Fraudulent Expense
1 . The system displays list of recently uploaded CSV files. User selects the desired CSV file and clicks on “detect” button.
2 . System alerts if the selected CSV has data for less than 6 months and aborts further execution; otherwise it proceeds to scanning process outlined in step #3.
3 . DETECT scans through all the expense claims from the CSV file. It reads each claim amount and generates a Benford’s frequency distribution.
4 . The system displays the Frequency distribution generated by the application along with the Benford’s distribution and its percentage deviation from Benford’s distribution.
5 . The rows that have more that 5% deviation from the Benford’s distribution are highlighted in Yellow color.
6 . The auditor can flag the Yellow color rows to generate the list of transactions that require validation by the Supervisor. For each flagged transaction, the system automatically builds a supervisor wise index of all such claims.
Investigate Flagged Expense Claims
1 . The system shall notify the supervisors of respective claims that are shortlisted by the application.
2 . The list of all flagged transactions to be reviewed by a supervisor are displayed to him/her by DETECT.
3 . The supervisor clicks on the Claim id to access the complete record. The claim record opens up displaying employee name, type of expense, date,
description and amount.
4 . The supervisor can either mark a claim as “valid” or “false claim”. DETECT removes the valid claims from the index.
False Claims
1 . The pre-audit user can view the claims marked as False Claim by the supervisors.
2 . Action on such claims is taken outside the system.
A user-friendly interface needs to be developed to ensure smooth usage of the system.
About Benford’s Law
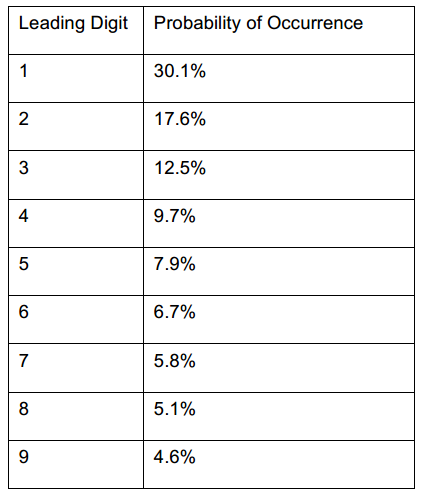
Benford’s law, also known as the first-digit law, it says that in lists of numbers from many real-life sources of data, the leading digit is distributed in a specific, nonuniform way.
The standard Benford’s Distribution is outlined on the next page.
Auditors use this law to find patterns in data where there is a possibility of a fraud.
Such data is taken up for further investigation. Learn more about Benford’s law at http://mathworld.wolfram.com/BenfordsLaw.html URL.
DEVELOPMENT ENVIRONMENT
DETECT will be developed as a web application using Java/JSP and DB2 database. Eclipse will be used as the IDE for the same. You may consider using a
JavaScript framework like Prototype/ Scriptaculous/jQuery. JSON specifications can be found at http://www.json.org/ URL.