INTRODUCTION
GENERAL: Office correspondence and auto questionnaire java based project are developed as per the requirements of the mechanical department.
OFFICE CORRESPONDENCE
Mechanical department deals with the different type of letters. The letters which are received by the mechanical department are incoming letters and the letters which are sending through the department are the outgoing letters.
The different types of letters received and sent by the mechanical department are as follows:
- Local letters
- Headquarters letters
- Others

LOCAL LETTERS
The letters received from and send to other departments of Vijayawada division are termed as local letters.
INCOMING LOCAL LETTERS
The letters received from other departments of Vijayawada division are termed as incoming local letters.
OUTGOING LOCAL LETTERS
The letters sent to other departments of Vijayawada division are termed as outgoing local letters.
HEADQUARTER LETTERS
Secundrabad division is headquarters of the Vijayawada division. So the letters received from and send to Secunderabad division are termed as headquarters letters.
INCOMING HEAD QUARTER LETTERS
The letters received from Secunderabad division are termed as incoming head quarter Letter.
OUTGOING HEAD QUARTER LETTERS
The letters sent to Secunderabad division are termed as outgoing headquarters Letters.
OTHERS
The letters received from and send to the divisions other than Vijayawada and Secunderabad are termed as other letters.
INCOMING OTHER LETTERS
The letters received from the divisions other than Vijayawada and Secunderabad are termed as incoming other letters.
OUTGOING OTHER LETTERS
The letters sent to the divisions other than Vijayawada and Secunderabad are termed as outgoing other letters.
If the reply for the above letters is to be given immediately then those letters are marked as demi official letters.
So different types of demi official letters can be
- Incoming Local demi official letter
- Outgoing Local demi official letter
- Incoming Head quarters demi official letters
- Outgoing Head quarters demi official letters
- Incoming Other demi official letters
- Outgoing Other demi official letters
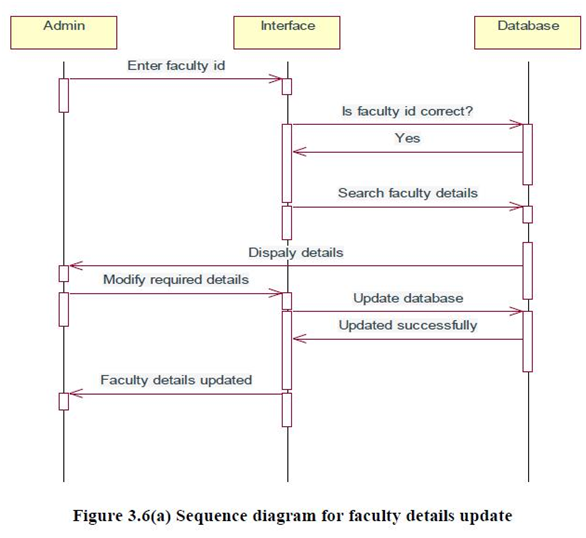
All the incoming letters are received by the chief office superintendent and are marked to different sections of the mechanical department with the authorized signature of the senior divisional mechanical engineer. Then the respective task is performed by section accordingly to the letter which is received by it and sends the reply to the chief office superintendent. Then the chief office superintendent with authorized signature of the senior divisional mechanical engineer sends the letter as an outgoing letter.
The mechanical department consists of seven sections.
- Contract/tenders
- Carriage & wagon staff
- General/pass
- Rolling stock
- Stores
- Budget
- Power
AUTO QUESTIONNAIRE
The test to avail the promotion is conducted for the employees of the Vijayawada division. The question bank offered to the employees for preparation comprises of the following type of questions.
- Long answers
- Short answers
- Fill in the blanks
- Multiple choices
- Expansions
STATEMENT OF THE PROBLEM
OFFICE CORRESPONDENCE
To maintain the details of different types of letters, to show the status of the letter and also to generate the reports.
AUTO QUESTIONNAIRE
To maintain the questions and to generate the questions randomly when appropriate type of question is selected.
EXISTING SYSTEM
OFFICE CORRESPONDENCE
In the existing system, the details of the letter are being maintained manually by entering different types of letters in different books. To know the present status of the letter, it is very difficult in the existing system because one has to verify all the entries in that particular book. So it is time-consuming.
AUTO QUESTIONNAIRE
In the existing system, question paper is set manually by selecting the type of questions from the printed question bank. It is very difficult and time-consuming to set question paper manually because when selecting a question one has to verify whether it was previously given or not. One has totally the maximum marks for which paper was given and marks allotted for each question and he should also consider the choices for each type of question.
PROPOSED SYSTEM
OFFICE CORRESPONDENCE
The proposed System is a web-based application. It maintains details of all the letters within the mechanical department. The present system shows the pending letters and reports.
AUTO QUESTIONNAIRE
In the proposed system the question paper is set automatically by selecting random questions when an appropriate number of question type is selected.
OBJECTIVES OF STUDY
OFFICE CORRESPONDENCE
- Automating the manual work.
- To generate the status of the letter
- reminder provision for pending letters
AUTO QUESTIONNAIRE
- To generate the question paper quickly from the available database.
REQUIREMENT ANALYSIS
FUNCTIONAL REQUIREMENTS
OFFICE CORRESPONDENCE
- The user can add the details of all the letters into the database and view the pending letters.
- The authorized user can edit the details of the letters and delete the letters from the database.
AUTO QUESTIONNAIRE
- The authorized person can add, delete and update the questions in the database.
SYSTEM DESIGN SPECIFICATION
SOFTWARE REQUIREMENTS
Operating system: Windows XP professional
Programming Language: JAVA
Web Technology : J2EE (JDBC, Servlets, JSP, HTML)
Browser: Internet Explorer
Web application server: Apache Tomcat
Model Design: Rational rose
IDE: Net Beans 6.7.1
Data Base: Oracle 10g, MS Access.
HARDWARE REQUIREMENTS
Processor: Intel p4
RAM: 256MB RAM
Hard disk: 20GB or more
Required Software’s:
- Oracle 9i
- Java
- Netbeans 6.7.1
- Mozilla Firefox
Instructions to Deploy:
1. Install the required software’s
2. Open Netbeans and open the project from source code
3. Configure database connections from DBConn package of Source Packages under the root PPO & Technical
4. Right click on CreateTab.java under Test Packages under the root PPO & Technical and click on run
5. Right click on root and click on run
Note: In case of reference problems right click on root and click on resolve reference problems, and select the library files.
Output Screens:
- Homepage in office correspondence
- Selection of letter type in office correspondence
- Reports generation using a serial number in office correspondence
- Report generation using by date in office correspondence
- Report generation using between dates in office correspondence
- Report generation using marked in office correspondence
- Report generation using received from in office correspondence
- Report generation using send to in office correspondence
- Report generation using general in office correspondence
- Report generation using remainders in office correspondence
- Pending letters in office correspondence
- Editing of the letter in office correspondence
- Login page for deleting the letter in office correspondence
- Letter deleted successfully in office correspondence
- Login page in the auto questionnaire
- Operations on question bank in the auto questionnaire
- View of multiple choice questions in the database
- Default question paper in the auto questionnaire
- Question generator in the auto questionnaire
- window to open or cancel generated question paper in the auto questionnaire
- Generated question paper opened in MS word in the auto questionnaire
CONCLUSION
The primary goal of this project is to reduce the work which is being done manually. By maintaining the details of all the letters in the database we view the letters based on different fields such as serial number, marked to, date and so on. The letters which are pending can be viewed easily and the remainder is generated. Editing and deleting the details of letters is also possible.
The question paper is being generated by selecting the questions randomly from the database. We need to mention the maximum marks and the type of question. Creation of our own template is also possible. This system is very user-friendly.
SCOPE
The application i.e., office correspondence which we developed is a standalone one i.e., within the department we can use. The letters are received in paper format and then they are saving them in the database. Due to this time gets wasted. If we develop a web-based application the letters received by the department are sent through emails then a lot of time gets saved.
Download Office Correspondence and Auto Questionnaire Java Project Code