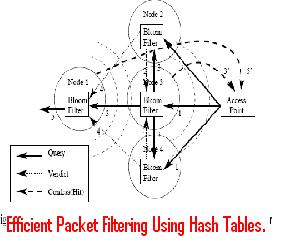
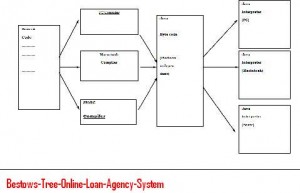
Mining Frequent Patterns Java project is the most efficient one. Its function is to mine the transactional data which describes the behavior of the transaction. In an online business or in an online shopping the customers can purchase items together. 
Frequent patterns are patterns such as item sets, sub sequences or substructures that appear in a data set frequently. Many efficient algorithms were developed based on the data structure and the processing scheme. The mining of most efficient algorithms such as Apriori and FP Growth was implemented here.
Project Details:
In this paper, we propose the efficient algorithms (Apriori and FP Growth) used to mine the frequent patterns. Frequent patterns are patterns such as item sets, subsequences or substructures that appear in a data set frequently. From the transactional database, we can examine the behavior of the products purchased by the customers.
For example, a set of items Mobile and SIM card that appear frequently as well as together in a transaction set is a frequent item set. Subsequences mean if a customer buys a Mobile he must also buy a SIM card and then head phone etc.
From the history of the database, these transactions are happening sequentially is called sequential patterns. The Substructure refers to different structural forms such as sub graphs, sub trees which may be used along with item sets or sequences.
Many of the algorithms were developed for mining the frequent items. In this paper, we propose the efficient algorithms (Apriori and FP Growth) used to mine the frequent patterns. The Apriori algorithm generates a candidate set during each pass. It reduces the data set by discarding the infrequent item sets that do not meet the minimum threshold from the candidate sets.
To avoid the generation of candidate set which is expensive the FP Growth algorithm is used to mine the database. The FP Growth does not generate the candidate set instead it generates an optimized data set that is FP tree from the dataset.
The FP tree is mined to construct a conditional database. FP mining processes use the divide and conquer strategy, so the data set shrinks and gives us quite small conditional frequent pattern base. From this database, the frequent patterns are generated.
Conclusion:
A traditional system based on the manual calculation and dynamic counting method. We propose the efficient algorithms used to mine the frequent patterns. We have proposed the implementation of efficient algorithms to find frequent patterns.
The Apriori algorithm scans the dataset repeatedly whereas the FP growth avoids the costly candidate set procedure and generates the highly condensed database called as FP tree. Implementation of this project shows that the FP Growth method is efficient for mining frequent patterns and it is an order of magnitude faster than Apriori algorithm.