Literature Review:
Ad Hoc network are described as a group of wireless mobiles hosted and arranged by a temporary network with no support of any kind of centralized admin. The Ad Hoc networks are different from other wireless LAN’s because of the nonexistence of any infrastructure . When referring to infrastructure it is like access points. In this case all nodes perform transferring from destination, router, source and then towards more additional hop packets if required to go to the final destination by help of multi hops.
The absence of pre-planning is the most significant feature of the ad hoc networks. The network topology is identified after the use of network. So in order to “set – up” the network several messages are used and different parameters should be exchanged. In Ad Hoc networks there is extreme subsistence of different other nodes with the information and position or their neighbors and printing facility provided or offering by the network along with local maps, files etc are some examples of the network parameters.
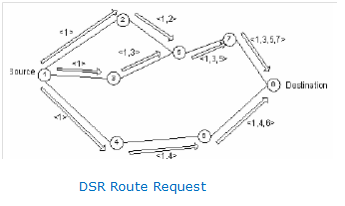
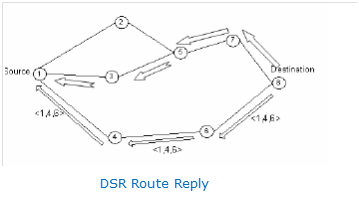
The Dynamic Source Routing(DSR) protocol, various solutions for energy or power management as well as overhead reduction are observed. The DSR protocol is defined as a simple and very efficient protocol.
Management of energy is considered as a very necessary requirement for effective process of battery powered MANETS. For ad-hoc networks an extensible on-demand management of power that adjusts to traffic loads is suggested by Robin Kravats. For on-demand minimum energy protocol essential characteristics has been recognized and methods for their implementation have been proposed by Sheetal Kumar Doshi. Simulation software has been utilized in the work described by Jorge Nuevo.
Iterative algorithms have been introduced by Gill Zussman for energy efficient routing. The issue have been originated for any cast routing where the aim is to increase the battery lifetime unless the battery exhausts. A method is being provided by Nicolaos B.Karayiannis etal, which depends on a limited entropy routing algorithm for the purpose of consumption of energy, which were extended through the use of information of entropy’s theoretic concept in order to increasingly decrease the uncertainty related by a deterministic annealing process with the help of route discovery (GETSY S SARA, 2009).
The ad-hoc network’s energy efficient all-to-all as well as one-to-all broadcast operations are being provided by Stephanie Lindsey. Presenting energy efficient routes is considered to be the major challenging. An idea id being provided in order to decrease the active energy of communication needed to receive or transmit packets or consume energy through the support of idle nodes. In order to minimize the node’s demand by means of little remaining energy and to permit them to take part in longer network, the battery levels present calculations that are integrated into routing metrics has been represented. In order to increase the mobile ad-hoc network’s life duration, the protocol of ESDSR (energy saving dynamic source routing) is established. In ad-hoc networks, in order to increase the routing algorithm’s energy efficiency, a distributed power control that is suggested by Pierpaolo Bergamo et al is provided as a means. In relation to DSR, an on demand routing protocol known as DST and a table-driven protocol known as BESR were initiated. Numbers of routing protocols which also consists of protocols that are intended especially for networks of mobile ad-hoc, and conventional protocols like distance vector and link state that are employed for dynamic networking are introduced by Samir R Dasetal.
Three routing protocols such as AODV, DSR, and DSDV are compared for ad-hoc networks. Three different sensible scenarios are measured and it is also observed that reactive protocols such as DSR and AODV act much better when compared to DSDV protocol. During higher traffic loads, AODV priced better when compared to DSR, whereas at moderate traffic load, DSR when compared to AODV performed better.
Previous Chapter -> Aims and Objectives of the Project
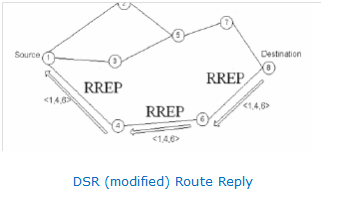
Next Chapter -> Modified DSR
Full Project Report -> Incorporating Energy maps to measure and compare the coherence time and spreading period across mobile wireless networks