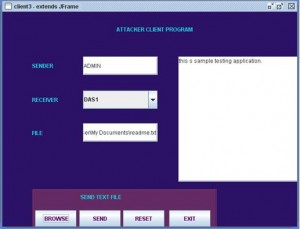
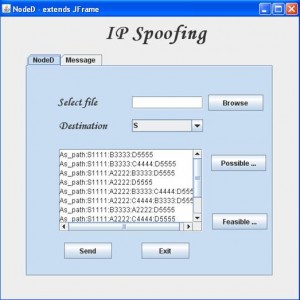
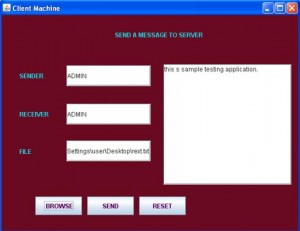
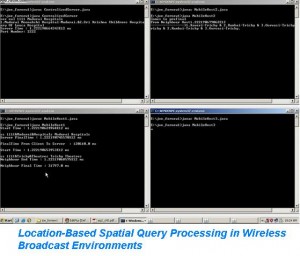
A known example related to the Skype, security breach can now easily tracked the infrastructure provided (Source: Leyden, J “Say Hello to the Skype Trojan”. published on Oct 18, 2005).
Problem Description: The detection and rectification of the security breach in the windows Skype users have been completed.
Chances of an incorrect file transfers can exist if the Skype URL malfunctions due to break in required parameters, either by the system’s vulnerability or by an attack on the original source code of the web page. This could also occur due to the end user error. Impact on the Skype software before 2.5 can be effective based on the attack that could be fatal. Hence it’s always preferred that the Skype is directly installed from the Skype URL which will help ensuring there are regular updates and monitoring (p.456-498). In case of a windows xp or professional operating system, certification is signed and authenticated by “VeriSign class 3 codes Signing 2009 CA”.
Along with the installation of the software, the end user will also receive a bulletin for security purposes, helps in removing a possible breach. Given below are arrays of base vectors that have a correct reflection, pre-assigned by VeriSign:
| Access Vector (AV) | Remote |
| Access Complexity (AC) | Low |
| Authentication(Au) | Not Applicable |
| Confidentiality Impact (C) | Partial |
| Integrity(I) | None |
| Availability Impact(A) | None |
| Impact Bias(B) | Confidentiality |