Appendix of Java and SQL Project:
- In security in large mediator protocols plz open source code folder and in that open the quantum.sql file.
- Copy all the all the data and follow this procedure.
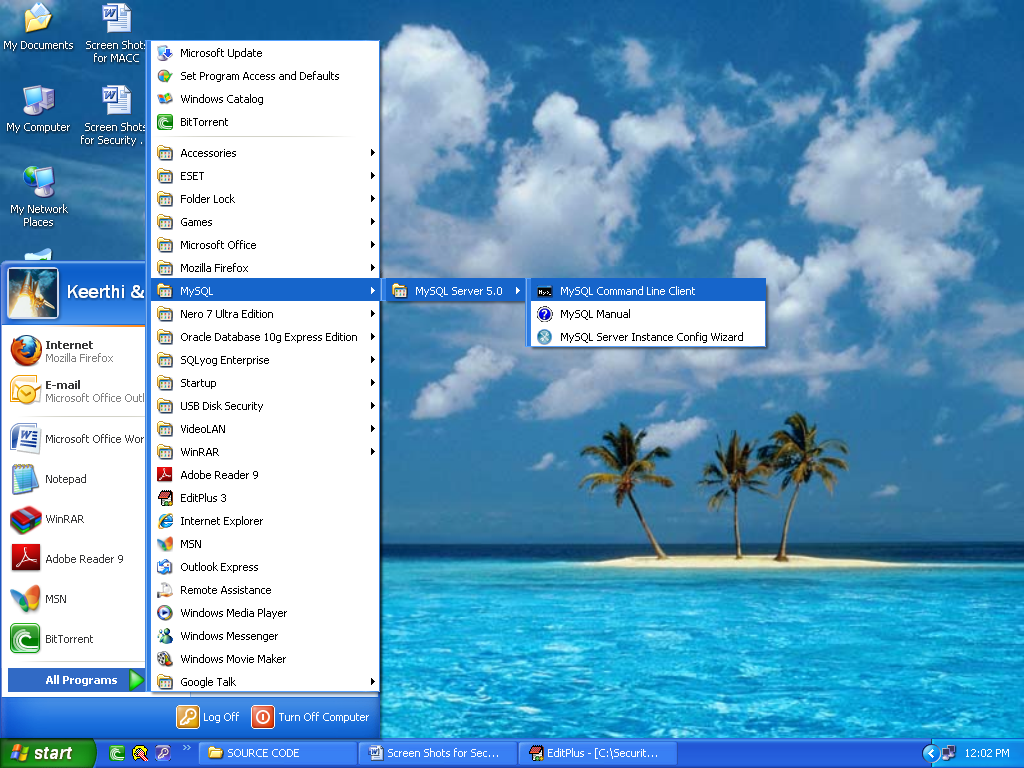
- In that open Start -> All Programs -> MySQL -> MySQL Server 5.0 -> MySql Command Client.
- This procedure is given the below page.
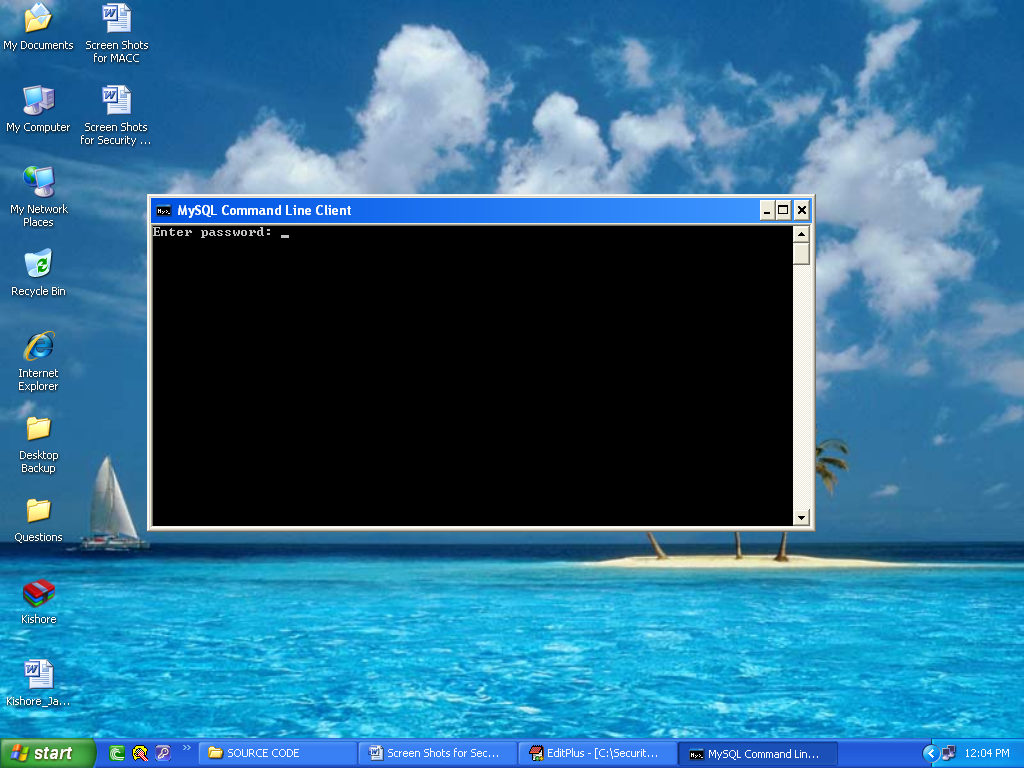
- After open the MySQL Command Line Client.
- Plz type the password as tiger and press enter.
- After we type following commands whether the Msql database is exist or not.
- MySQL > show databases;
- If MySQL database is exists the we type following command.
- MySQL > use mysql.
- After paste the all the data exist on Quantum1.sql file.
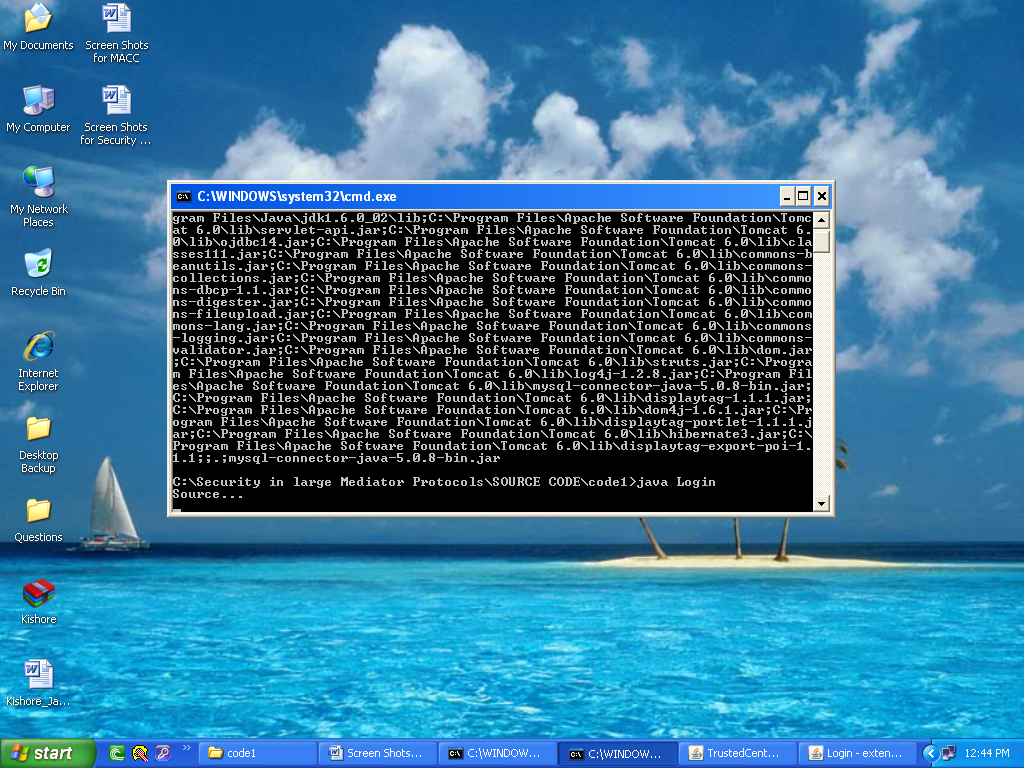
After open the code1 folder in that open the Tcen.bat and user.bat files.
If we double click on Tcen.bat file the following page was displays.
This is Trusted Center Page.
Also Double click on user.bat file.
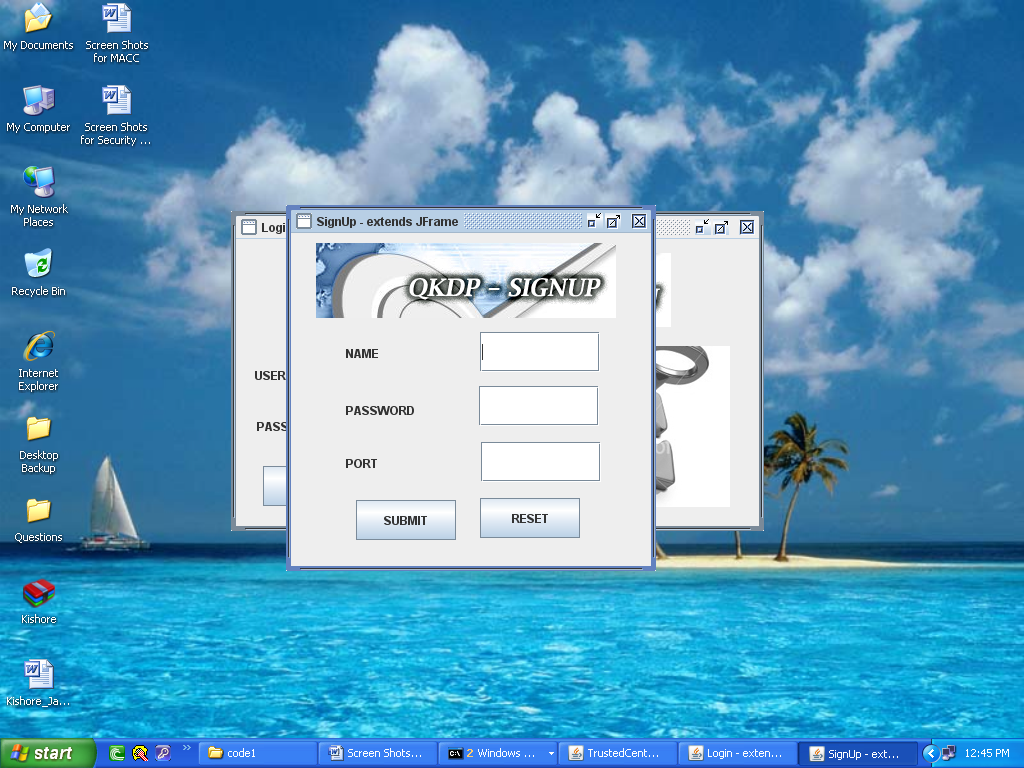
If U New User Plz click on signup button.
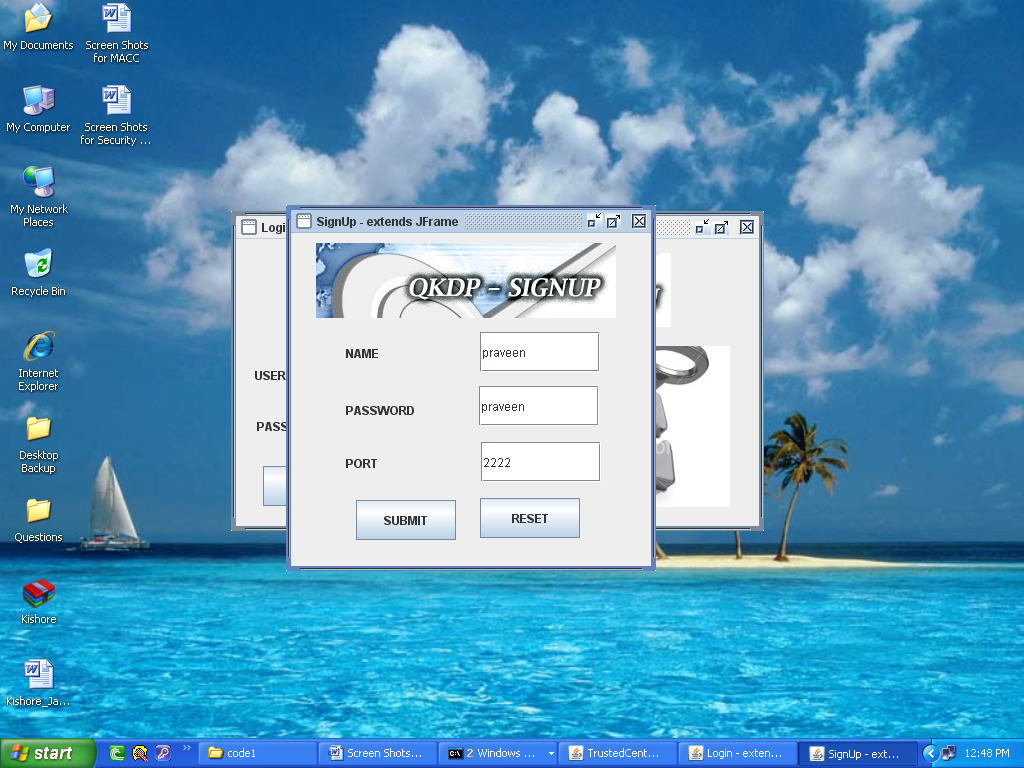
If u enter the all details after a secret key is generated on server with respect to the user and that key is user to send files to destination. In the signup we give the destination port number and sender name and password.
- After we give the details plz click on submit. In this screen the server generates secret key with respect to the user.
- After we login to the system as follows.
- After the give details plz click on sign in. If correct user the follow page was displays.
- In that we give the destination port number and choose file and click on send.
- If u click on send button it will ask the secret key. We give the secret key and click ok.
- Click on ok then the server verifies the all details and ask for conformation in each request that is as follows.
- Click on ok. After the details are stored on the trusted center and the server generates the session key and key value as follows.
- After we the follow page also generated.
- In that we give senders name and click open.
- Click on Open it will ask the secret key for conformation.
- Click on ok then the server verifies the all details and ask for conformation in each request that is as follows.
- Finally the trusted center sents the message to Destination by check the all session keys.
This Paper is written & submitted by Vamshidhar A.