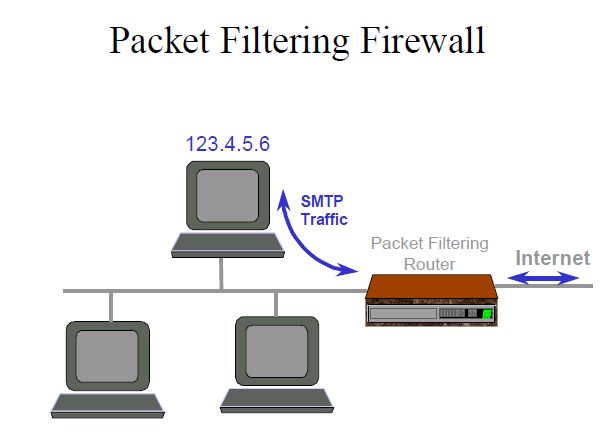
The most important and essential component of a firewall system are the Packet filter routers, and these are represented as the first among the defence because there are number of deficiencies and they are discussed as follows:
a) The configuration of these packet filtering routers is difficult because there is a huge rule set that is to be followed file configuring and specifically when the services from the applications are available, the accuracy and consistency in the set of rules cannot be estimated because there is no automatic approach for verifying the rules that whether they are implemented properly in the security policy or not. In addition to this if the logging of calls is not supported by the routers then it is not possible to have an idea about the packets that are not allowed apparently that are passing through the rules are not.
b) In an organization if some users among the employees have need specially for accessing the internet then their systems are added with new rules according to the requirement. This addition of new rules to the existing system makes the rule set more difficult to manage and so it becomes a complicated issue. Moreover, as the user is given permission to access the system it is considered as the wrong level of granularity. Here only the packets are verified but the users of the system are not authenticated.
c) The TCP filtering or UDP filtering are not permitted by some of the routers that are mostly basic, and therefore implementing specific security polices is very difficult and sometimes impossible also.
d) The packets between various ISO protocols that are running through the IP or TCP layers cannot be filtered. The process how ISO applications like X.400 and X.500 can run across the IP or TCP is specified by the RFC 1006. Conversely the RFC 1006 service will sit on the 102 port and so the ISO applications X.400 and X.500 are connected to port 102.
e) Hence at last it is concluded that the packet filtering routers are not very much secure, because there is no inspection of the content in the packet and there is a chance for the passing of any malicious content through transferring of these packets. For example the packets may contain viruses, delete commands that unauthorized. Then finally no proper authentication is provided for the sender of the packets.
These deficiencies can be addressed and avoided by inspecting the content in the packets when it is forwarded from the sender to the receiver. Therefore checkpoint provides a state-full packet inspection module which is done at the application level firewalls.