The Secured MAODV Ad hoc network communications devices can be Laptops, PDAs, Pocket PCs etc. Ad hoc networks are used for data transfer, sharing of information between students in a classroom, during disaster relief for disasters like earthquake, floods, soldiers in a battlefield and so on.
The passing of information in these networks happens through network packets being routed in the network. This routing in ad hoc networks is trivial, and happens in two ways – proactive, which is a table driven routing and reactive, where routing takes place on-demand. Ad hoc On Demand Distance Vector(AODV) Routing protocol, one of the reactive routing protocols,and hard state protocol has become popular in the past few years. The multicast version of the AODV or MAODV which is used for routing to a selected group of nodes within the AODV network group is being enhanced in this project to provide more secure routing in this project.
There is a lack of centralized network management functionally in ad hoc networks. These networks tend to be vulnerable to a number of security attacks in the form of data loss, privacy issues, interference eavesdropping, session hijacking and so on. Also countermeasures are not embedded, so external mechanisms are used. Authentication access control, encryption& digital signatures, biometrics verification are some preventive measures. Countermeasures beyond the prevention line are intrusion detection system, cooperation enforcement mechanisms etc. in one network. Here misuse and anomalies are detected and selfish node behavior is reduced.
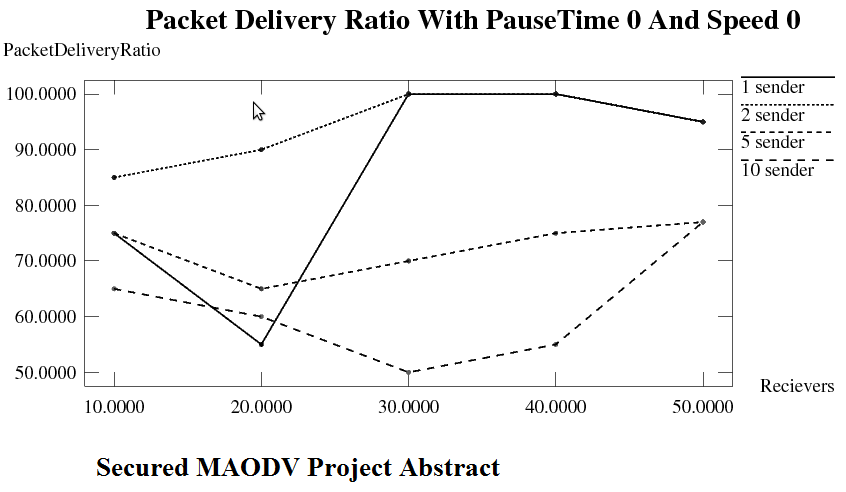
This work improvises the security of MAODV. An authentication frame work for MAODV and countermeasures that prevent the impact of the attacks are dealt with. There are four main attacks that are being considered, they are rushing attack, jellyfish attack, neighbour attack and blackhole attack. The nodes that are malicious and found to be involved in these attacks are marked as misbehaving nodes and their role in the network is minimised or removed depending on the location. The implementation is in the form of simulation using NS2. The original MAODV Project Source code and the improvised version are compared based on latency, number of attackers and packet delivery ratio with an emphasis on how security has improved.
CONTENTS
- List of Figures
- INTRODUCTION
- MANETs
- MAODV
- MOTIVATION
- LITERATURE SURVEY
- METHODOLOGY OF SOLUTION
- Why Simulation
- Why NS-2
- Software and hardware requirements
- Simulation Environment
- Simulation Results
- Statistical Results
- Graphical Representation of results
- THE PSEUDO CODE
- CONCLUSION AND FUTURE WORK
- REFERENCES
Software Requirements of Secured MAODV
- GNU/Linux based OS (Debian)
- Bash shell
- Ns-allinone-2.34(includes ns, nam and xgraph)
- Gnome C, C++ compiler and other C++ utilities
- Various Tcl/Tk libraries
- Perl and Python builds
Hardware Requirements of Secured MAODV
- Intel Pentium based Microprocessor with min. speed of 800 MHz
- RAM – 256 MB or higher
- 20 GB hard disk space
- 32 bit graphics supported VGA