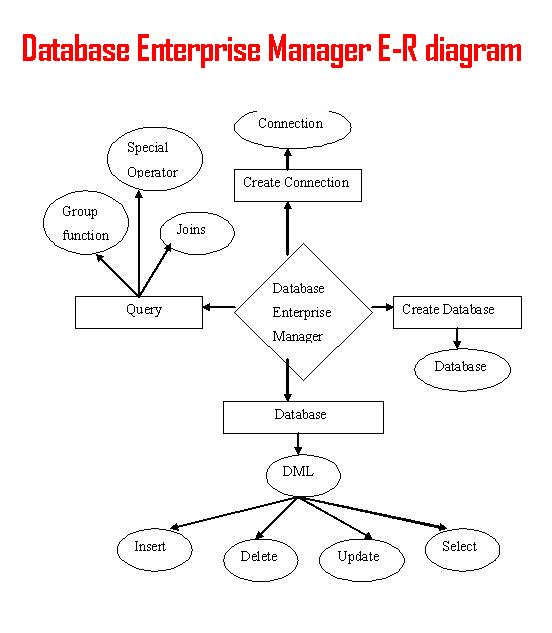
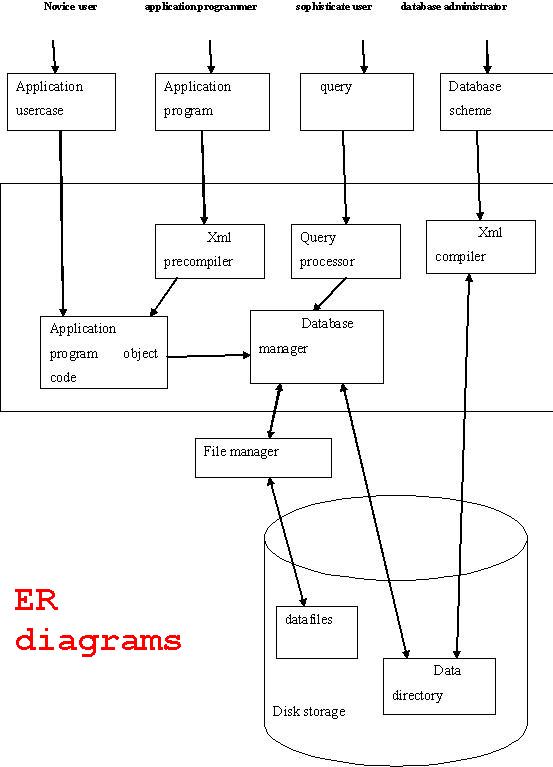
Database enterprise manager is a front end application for managing database tables. Here we provide ER diagrams , project report and project source code. This project is useful for b.tech third year students as mini project, MCA students.
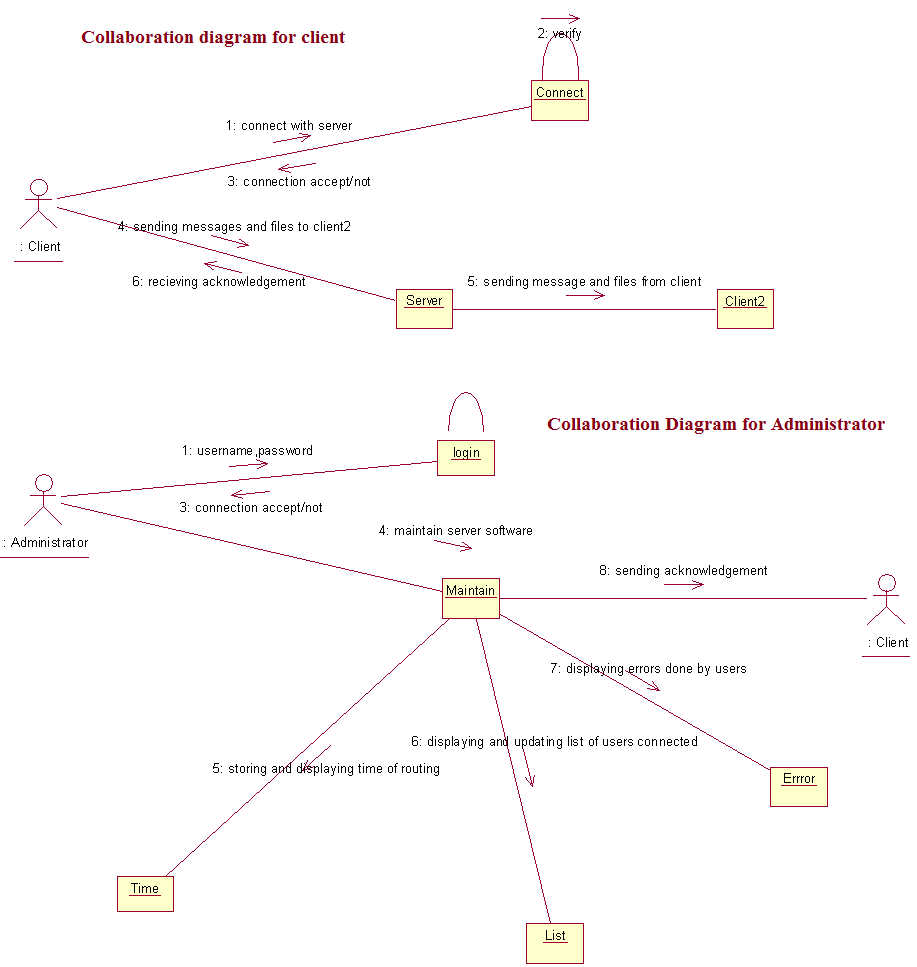
Collaboration Diagrams For Client Server Protocol Implementation MCA and M Tech Project
This Post explains about Collaboration Diagram for both client and server of this project, Mainly MCA and M tech Final year students can develop application related to this system. Java played major role to develop this project.
Download Collaboration Diagrams for MSC and MCA Major Project.
Database Enterprise Manager Final Year Project Report
Database enterprise manager project is implemented in Asp.Net web technologies and C#.Net programming language. Main aim of this project is to develop a user interface for managing SQL server functionalities. This application provides interface between low level data that is stored in database tables and organize that data using a front end graphical user interface. Using this front end users can execute queries and perform all functionalities that are executed on database.
Database requires large amount of space for storing data and data should be moved from hard disk to main memory. Main functionality of this application is to provide better performance in storing raw data. Database manger must translate DML language to low level file system commands for every operation from adding, deleting, modifying …etc performed from interface.
Data flow is explained in ER diagrams and software development life cycle diagrams.
This application is implemented in four modules establishing connection, creating database, database manipulation, query processing.
Here we provide entire project report for free download. Students can also download database enterprise manager project source code from Database Enterprise Manager Project Source code
Download Database Enterprise Manager Project Report.
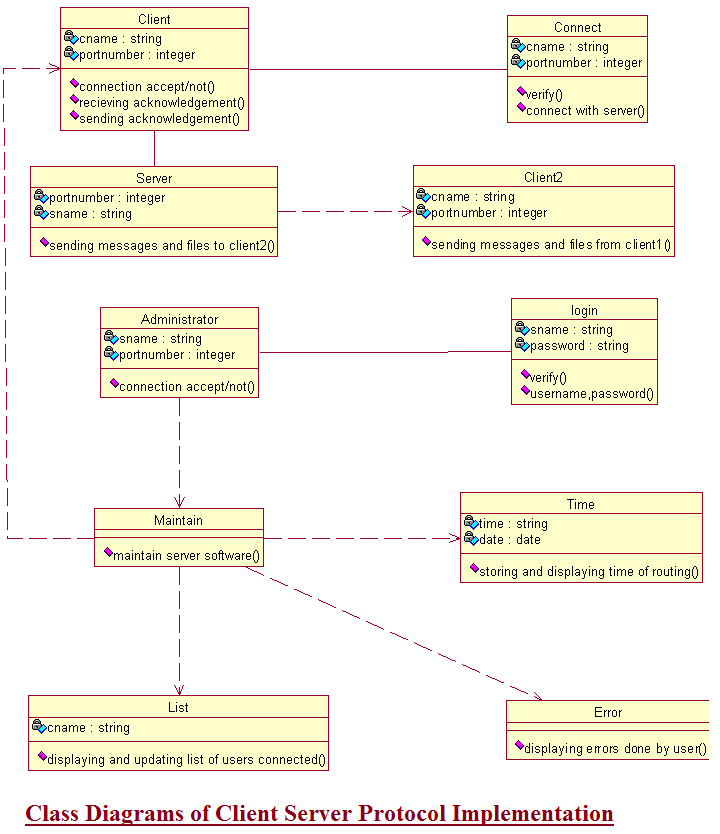
Class Diagrams for Client Server Protocol Implementation B Tech and BE Project
The main aim of this project is to provide best & efficient client server application between users and administrators. This system works well with Java programming where we have used Transmission Control Protocol (TCP) and Internet Protocol (IP) to implement this application. The below image explains about class diagram of the system where receiver info and sender info placed in high priority.
Download The B Tech and BE Project Paper Presentation and Seminar Report of the Client Server Protocol Implementation System.
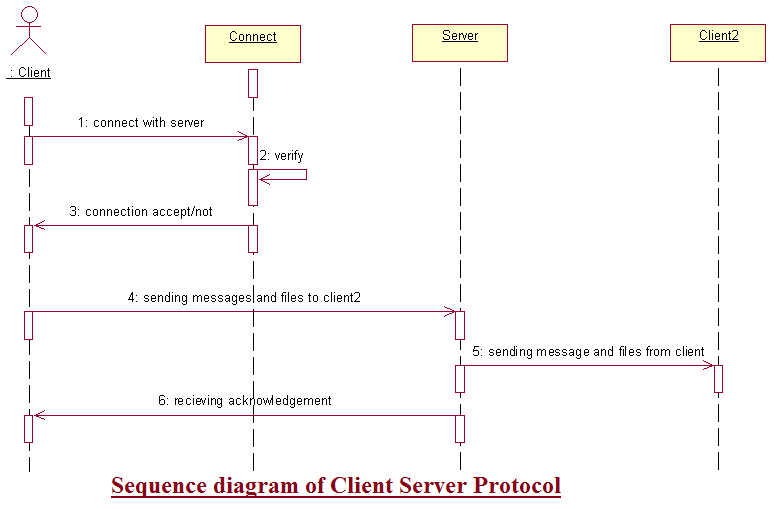
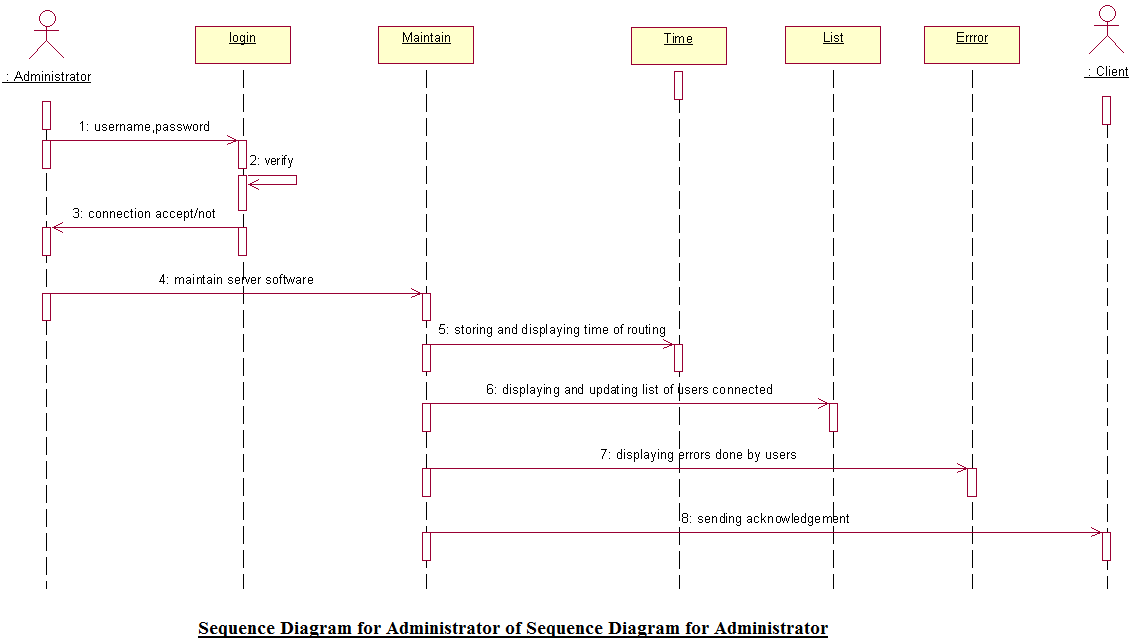
Sequence Diagrams of Client Server Protocol J2EE Project
This post give us introduction about Sequence Diagrams of this final year student Client Server application. Find the below diagrams to understand the total project.
Download Sequence Diagrams of Administrator and Client of Client Server Protocol J2EE Project.
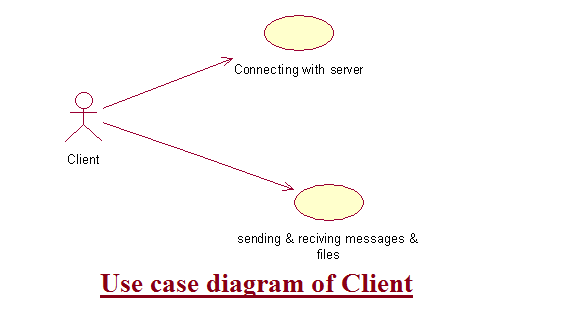
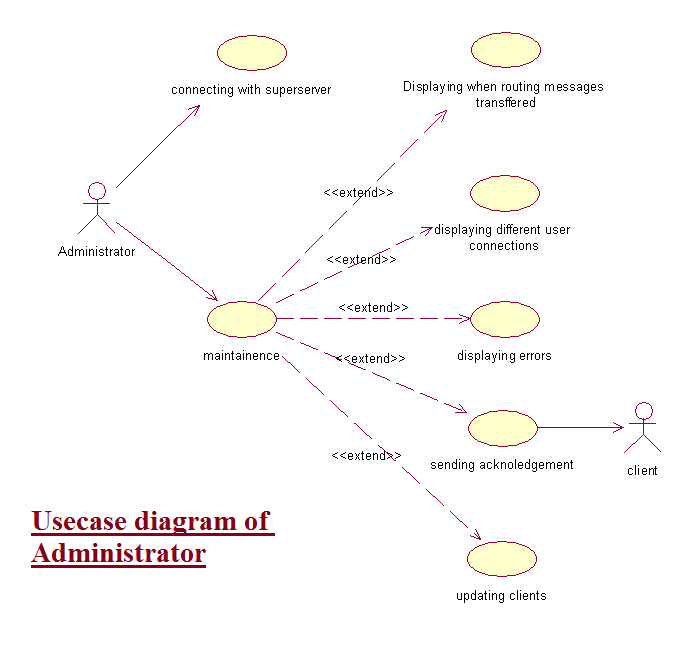
Client Server Protocol UML Diagrams & Project Report
This article provides full details about Unified Modeling Language (UML) Diagrams of the Client Server Protocol web application. Freshers and Engineering students can use this project for their reference. Find the below added UML Diagrams and Use case diagram of Client and Manager.
Download Client Server Protocol B Tech, BE UML Diagrams & Project Report with full Documentation.
Online Course Portal Project in Java
Online course portal project is developed in java platform. Main aim of this project is to implement a web based portal with education information which will be useful for college students. Using these web portal students from different parts of the world can share knowledge by updating to the queries posted by other students and uploading course related material to website. Online education is one o f the fast growing filed on web where users can directly solve problems by visiting website without any help from teachers. This system had increased scope of online education and online courses. Along with online courses this web site can be updated with other information like job updates, online exam details , upcoming events , government job , guidelines for higher education.
In existing system only way for course learning is by going to school and take lessons from lectures. In this system there are few issues quality of education may not be good in every college and payment for courses. This process is not a efficient method in present trend as web is providing new sources of better education.
In proposed system users can learn from web portal where high quality faculty will help students for improving knowledge. This system will reduce cost for education and improve standard of education.
Computer science students can find more related project with project reports and source code form this site for free download.
Download Online Course Portal Project in Java with source code.
Testing in Mobile AD-HOC Networks Report
TESTING is one of the tools it plays big role in the market now a days.Testingactually mainly classified in to 2 types.
- System testing
- Software testing.
System testing: This software having drawbacks of broad-costing protocols and accurate results failure etc. This testing is developed in the simulated model to overcome drawbacks with existing of logical network broadcast state.
The software testing is based on mobility management and set management in a environment of mobile. This broad cast protocols is based on self-pruning in MANET.This mobility management main theme is to join Transmissionsbetween the Nodes. This mobility of nodes adds another dimension of complexity in the mutual interface. These Broadcast protocols are based on the self -pruning which helps in MANETS.
SOFTWARE TESTING:
After completion of the written coding software must be tested to many errors as possible before delivery the project to the client and the customers.Your goal is to design number of series test cases that have whatever errors there you are able find out that errors. We have a good guidance for designing tests also. Those are 1) Exercise the terminological of software components and 2) Exercise the input and outputdomains of the program to uncover errors in the function.
Software testing is the process of confirming the functional corrections of software by running it.
Software testing mainly performed of tworeasons .That are
1) Defect detection
2) Reliability estimation.
Testing software to detect the detections this main problem of applying software shall suggest all the things. In both of the cases the mechanism is correct to often impossible to develop.That’s why software testing process is highly dependent of different pieces.
Software is now a day’s physical process of where inputs are received by products. Mostly physical systems fails in a fixed ways.by contrasts, this type of software’s fails in many ways.The main key of software testing is trying to find out the myriad of failure modes. For all the programmes and it is main place for test many of the syntactic features of the written codes as possible are called white box of software testing techniques.Functional testing is a testing process that is Just like blocked box. It is main aim is to examine the overall functions of the products.
Final stage of the testing is system testing,in this type of testing to examine the whole computer system.
Test cases are also two types.
1) Defect detection
2)Reliability estimation.
Download Testing in Mobile AD-HOC Networks Report .
Internal Mark Assessment System in VB Project Report
The biggest challenge of a school office authority is to manage each and every student detail and their marks effectively and efficiently, often cases occur of changes in marks, pass list, name changes, data losses etc. In the existing scenario each student’s marks are separately entered by their teachers first in a sheet of paper and then later an office staff copies the mark into a register. It is extremely tedious to search data from this registers and usually mark registers are kept separate from student registers, moreover there are every chance of entering wrong marks of the student. To overcome all the cons and disadvantages of the existing system, the proposed software is developed to make the entry and the retrieval of student data much easier.
The proposed software will have following module features:
Master Module: Various master details such as batch, subject, course, subject, designation etc. can be saved, updated or removed. These entries are important as it is the base for other modules.
Staff Module: The complete details of each staff is added or edited in this module. The allocation of subject to each staff can be provided
Student Module: Complete details of the students such as name, address, course, batch etc. can be added in the student entry form. The admin can also enter grades obtained by students in internal exams per subject. The student attendance can also be noted in other forms
Report Module: Various reports can be generated such as Grade reports per batch, attendance report between dates, staff allocation report etc.
The wholesome computerization of the data will ensure that the data loss is kept to a minimum and the details can be searched pretty easily. The reports can be generated instantly by inputting certain data and a print and export option would be also provided.
Download Internal Mark Assessment System in VB Project Report .
Privacy Preserving Data mining (PDDP) Seminar Report
Whenever there is some sensational data released by government or corporates often we see lot of controversy happening around. Some people complain of invading their privacy and demand to remove offensive content from the data declaration. Imagine the trauma a HIV patient goes through when it is revealed in front of the world that he is infected or more recently the negative effect of social media where anyone from anywhere can post offensive and provocative content. All such uncontrolled data publishing should be screened and monitored so that privacy of an individual or an institution is preserved. Privacy preserving data publishing ensures that privacy is preserved while the data gets revealed or shared; it is done using some techniques and methods according to corresponding situation and scenarios.
Approaches in PPDP:
Micro Data Publishing: Includes public census for government records, the details such as name, DOB, job profiles etc. are taken from members of a family. The disclosure of most of this data would be minimal.
Data Anonymization: There is a huge amount of risks associated with the disclosure of sensitive data, it must be anonymized before publishing. All explicit and quasi identifiers are replaced with mellowed down and inconsistent data.
The data publishing process includes various persons such as
- The individual from whom data is collected
- The collection agent
- The adversary
- The end user who uses the data
The components taken care while publishing the data are sanitization mechanism, privacy criterion and utility metric. Disclosures can be both positive and negative and each is denoted by separate anonymization algorithms. Then there is also uninformative principle in which additional info are added by the adversary. PDPP also includes algorithms and analysis methods like k-Anonymity, I-Diversity, Closeness, utility analysis, anonymization techniques, distance measures and other experiments. Each technique adapts different methods to preserve data privacy.
Download Privacy Preserving Data mining (PDDP) Seminar Report .