ABSTRACT:
Data security is the main concern in different types of applications from data storing in clouds to sending messages using chat. In order to provide security for data in the cloud, there are many types of techniques which are already been proposed like AES, DES, and RSA but in existing methods, most of the time only a single type of encryption was used either AES, OR DES, OR RSA based on user requirement but in this system main problem is each encryption is done using encryption keys if these keys are exposed in any case entire data is lost so we need an effective method which can provide more security so in this project hybrid cryptography is used where existing encryption methods are used but three methods will be used.
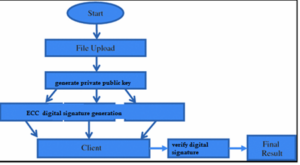
When the user uploads data will split into three parts the first part will be encrypted using AES, the second part will be encrypted using DES, the third part will be encrypted using RSA and these three encrypted files will be stored in the cloud and keys used for AES, DES, and RSA are stored in the image using LSB steganography when users want to download total data from cloud-first keys should be retrieved from the image and these keys are used for decrypting data again by using AES, DES and RSA and final data is combined and stored in the file. This method provides more security for data.
OBJECTIVE:
Data security is the main issue in cloud data management there is a chance of developing effective methods like hybrid cryptography for improving security. In this project, AES, DES, and RSA are used along with LSB.
INTRODUCTION:
The cloud is playing important role in data management and is another type of service that provides a secure way of data handling and remote data accessing where users from anywhere can use the cloud for data access. As the cloud is a third-party application where data uploaded by users must provide security features to reduce risks from data attacks in order to do that encryption techniques here are used like AES, DES, and RSA.
EXISTING SYSTEM:
In the existing system, the cloud is used to use any one of the encryption techniques and key verification is done using the identity of the user. Based on application requirements different encryption techniques are used.
DISADVANTAGES:
Only single encryption techniques are used and if keys are not managed effectively there are chances of leakage of keys.
PROPOSED SYSTEM:
In order to improve security for cloud data compared to existing techniques where keys are shared security between users new hybrid cryptography technique is proposed where three types of encryption are used AES, DES, and RSA, and the LSB steganography technique is used for secure key sharing.
ADVANTAGES:
Data is split into three parts and each part is encrypted using one encryption technique and keys are shared securely by embedding in the image.
SOFTWARE REQUIREMENTS:
- Operating system: Windows 7.
- Coding Language: python
- Tool: anaconda, visual studio code
- Database: SQL lite