Abstract:
Generally, we send many pictures to our friend’s relatives and others. The photos that may contain personal information so keeping them to at most secure is the important thing. So in this project, we implement the idea of encrypting and decrypting the image using BLOWFISH algorithm.
Encryption Process:
Data image as a plaintext and the encryption key are two inputs of the encryption process. In this case, original image data bit stream is divided into the length of the block of Blowfish algorithm.
Decryption Process:
The encrypted image is divided into the same block length of Blowfish algorithm from top to bottom. The first block is entered to the decryption function and the same encryption key is used to decrypt the image but the application of subkeys is reversed. The process of decryption is continued with other blocks of the image from top to bottom
The Single Module Present in the application is
User:
In this application user will register and log in with the username and password, after logging in the user will upload the image which is to be encrypted and then after encrypting the user will get a secret key to the user registered email id using the key and encrypted image
Existing System:
The existing system for this project the text information is encrypted by ASCII values or any special characters. In the existing system, didn’t use the safely sent the encrypted information into the mail. The hackers easily access that information. The encrypted text is didn’t restrict any secret key. So that information easily decrypted. Two common drawbacks of the visual cryptography scheme (VCS) are the large pixel expansion of each shared image and the small contrast of the recovered secret image
Proposed System:
Blowfish to be a publicly available cryptographic algorithm with the potential to replace DES. Blowfish is a 64-bit symmetric block cipher that uses a variable-length key from 32 to 448-bits (14 bytes). The algorithm was developed to encrypt 64-bits of plaintext into 64-bits of ciphertext efficiently and securely. The operations selected for the algorithm were table lookup, modulus, addition and bitwise exclusive-or to minimize the time required to encrypt and decrypt data on 32-bit processors
Screens:
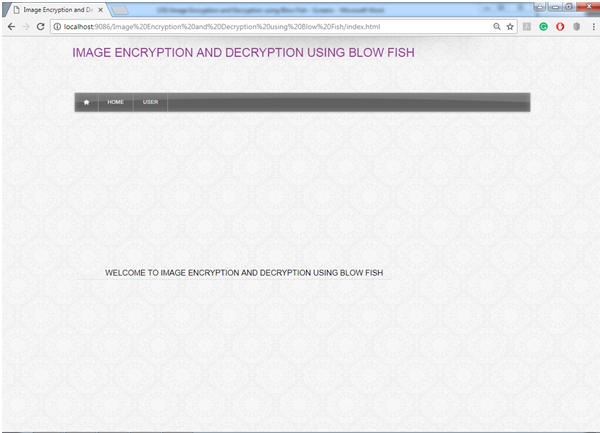
Fig: Home Page
This page shows the default view of the Image Encryption and Decryption application and showing the number of modules present in it.
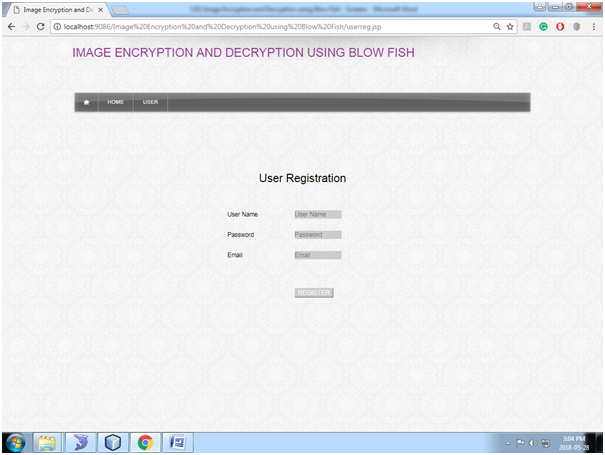
Fig: User Registration
In this page, new users will register the Image Encryption and Decryption application by entering all necessary details.
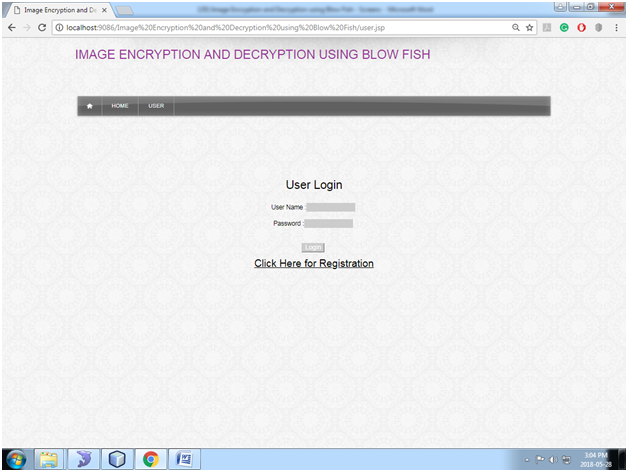
Fig: User Login
In this page, the user will log in by giving username and password.
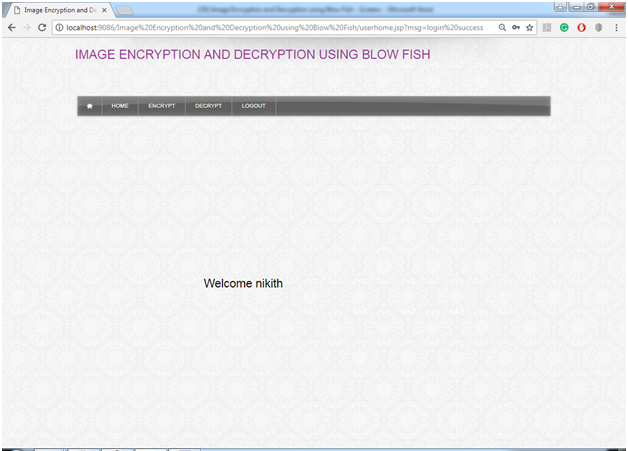
Fig: User Home
This page shows after the successful login and showing the basic functionalities that user can perform in this Image Encryption and Decryption application.
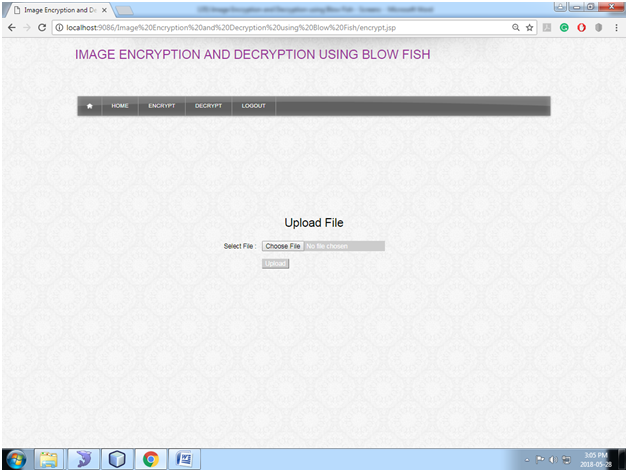
Fig: Encrypt Image
In this page, the user will upload the normal image to encrypt the image.
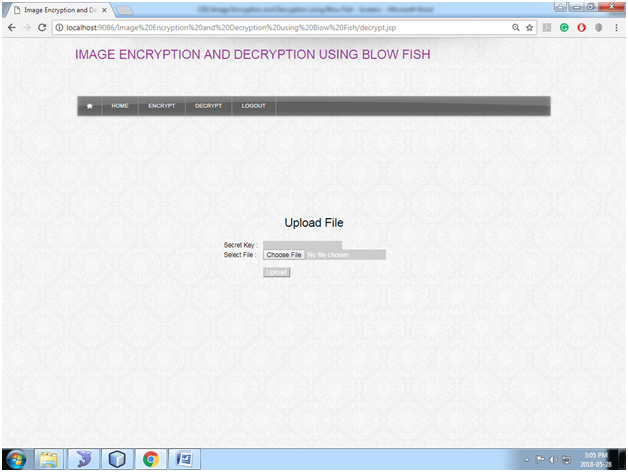
Fig: decrypt Image
In this page, the user needs to upload the encrypted image and secret key which is sent to user mail id.
Software Requirements:
JDK 1.8, NetBeans 8.0.2, MySQL5.5, SQLYog

send me the source code please
Where can i get the source code
where i can get the source code
please send me the source code
can i get the source code
Can we get the source code we will pay you for that according to your rates.
How can I get the source code?
can i get the source code
can i get the source code,please?
can i get the source code please
Can I get the source code , PLEASE!!!!!!!