PURPOSE OF THE PROJECT
Intra Network Sniffer is a tool designed for the purpose of searching for files and folders which are shared over a Local Area Network. It is particularly useful in organizations where a lot of folders are shared on individual systems.
Here’s how the application works. We need to specify an IP range. The tool searches for live hosts. It then determines the list of folders shared by each system and looks for files (according to a keyword that we specify).
PROBLEM IN EXISTING SYSTEM
In the existing system, workgroup list won’t populate or is incomplete. Says network resources are unavailable or cites permission problem. The system doesn’t understand sharing files among all range of system IP address. There is no interface designed to search the files on a specific LAN. High-level views of the system network activity are not provided by the existing system. In applications ranging from financial institutions to manufacturing facilities, network engineers will find Serial test easy to work with but loaded with features.
SOLUTION OF THESE PROBLEMS
In the proposed system workgroup will be populated in the interface completely, by using this workgroup the only administrator will know the architecture of the LAN. The proposed system is a passive and easy-to-use network monitor that helps network personnel understand what is occurring on their communications LANs.
By observing the workgroup range administrator will arrange the IP address range in the proposed system. A high-level view of the system network activity is provided in this proposed system. A good user interface will provide the administrator to watch the network sharing files among the LAN. Whenever a file is transferring between a range of IP addresses, the administrator can watch the file content on its own file mode.
Software Requirements:
- WINDOWS OS
- Visual Studio .Net
- Internet Information Server
- Visual Studio .Net Framework (Minimal for Deployment)
- Microsoft Visual C# .Net
PROPOSED SYSTEM
In the proposed system workgroup will be populated in the interface completely, by using this workgroup the only administrator will know the architecture of the LAN. The proposed system is a passive and easy-to-use network monitor that helps network personnel understand what is occurring on their communications LANs.
By observing the workgroup range administrator will arrange the IP address range in the proposed system. High-level view of the system network activity is provided in this proposed system. A good user interface will provide the administrator to watch the network sharing files among the LAN. Whenever a file is transferring between a range of IP addresses, the administrator can watch the file content on its own file mode.
UML Diagrams:
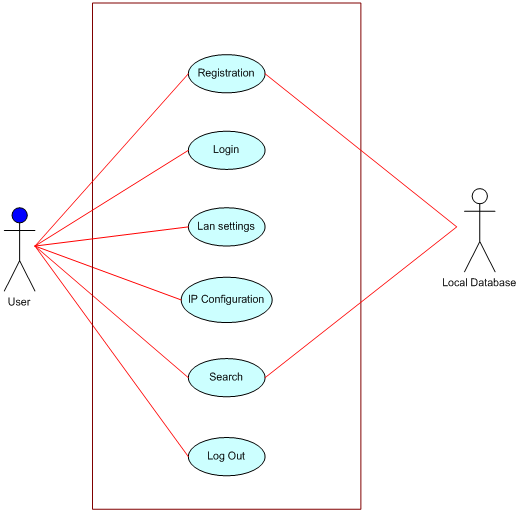
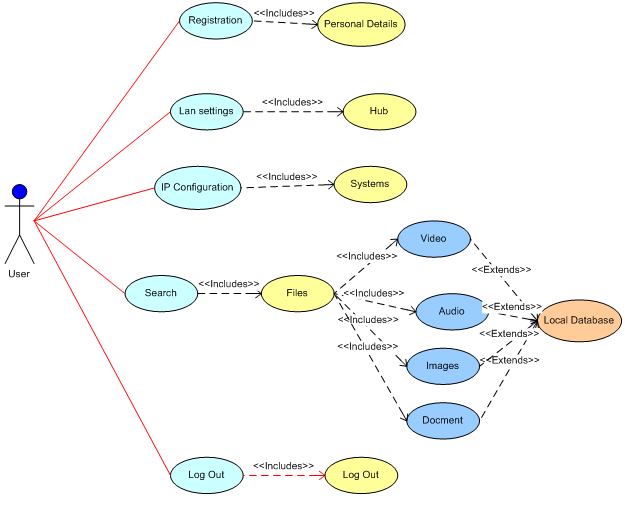
Use case Diagram:
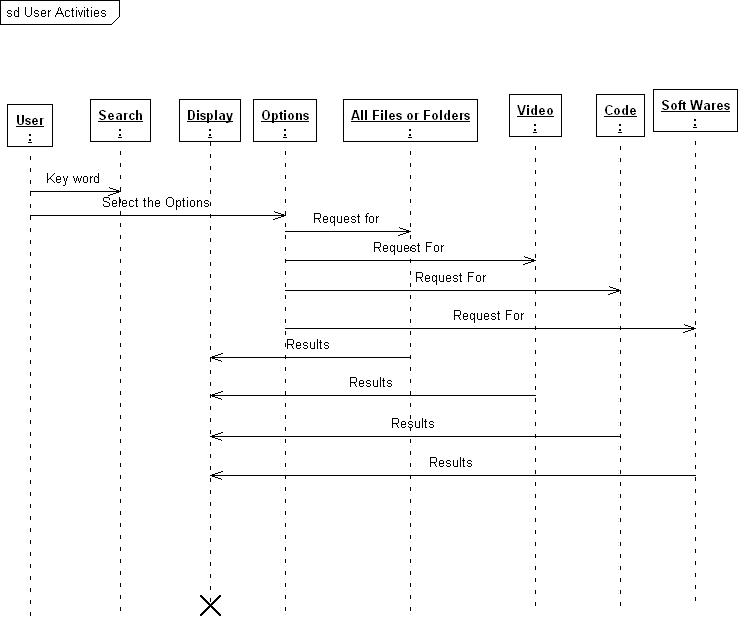
Sequence Diagram:
INPUT AND OUTPUT
The major inputs and outputs and major functions of the system follow:
Inputs:
• Specify the IP address range
• Select the File or Folder Type
• Give any keyword for searches like file name or extension
• Open the file in different file modes.
Outputs:
• The search starts for the given IP address range
• Catch the file depends on the file type
• The selected file will be opened depends on the file mode.
PROCESS MODEL USED WITH JUSTIFICATION
In this system, two types of process modules are developed.
• Text Module
• File Module
Text Module
Text module is the method in which the image is uploaded in the required path and then text to be hidden is given in the textbox and a retrieval key is given in the module to retrieve the information from the image while the extraction occurs.
File Module
File module is the method in which the whole file is extracted from a local disk and it is sent to another location by hiding the file and it is extracted to a required location with help of the key.
Project Execution Process:
- Home Page Before Execution
- Select a Bit Map Image
- Add a string for Key
- Type Secret Message and Hide the Message
- Save the Hide Message in another Image
- Extract the Secret Message Using Image (Uploading Image for Message Extracting)
- Press Extract Button for Retrieving Secret Code
- Finally, Secret Code Received