Results and Analysis
The detailed implementation procedure followed in developing the proposed camouflaging worm Final Year Project application is given in the previous chapter and the explanation to the key class used in developing the code is explained and the actual results achieved are given in this chapter. All the screens achieved are explained against the evaluation of the proposed concept of C-worm detection is presented in this chapter. Detailed explanation to all the screens and the process followed to detect the C-worms is given in this chapter with reference to the aims and objectives of the this project identified and given in the introduction chapter of this project and is as given below
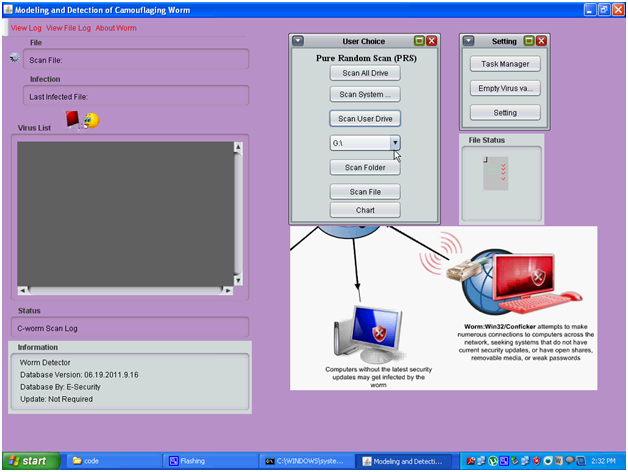
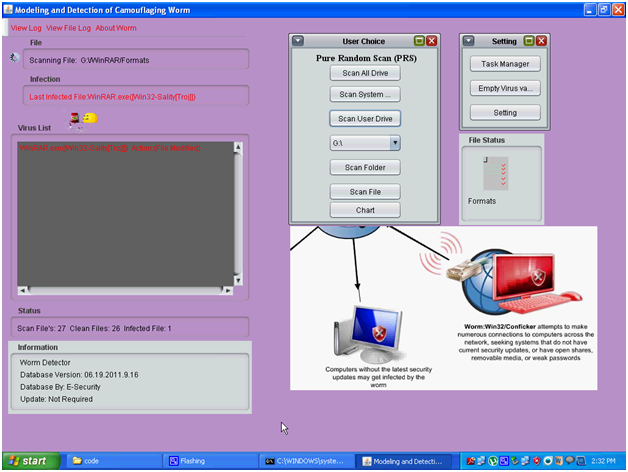
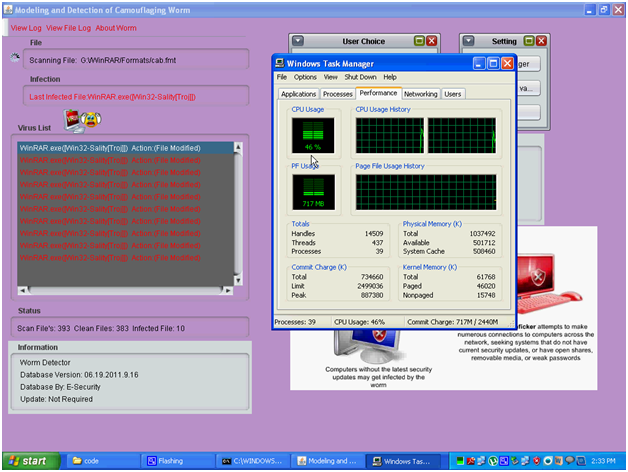
Above is the screen capture of the complete functionality of the application and from the above screen it can be observed that the entire windows created and user options are provided in this screen. There are mainly three components in this window and they are Pure Random Scan (PRS) , task manager and the virus list components and the actual design and implementation procedure followed are explained in the previous chapters of this project. Users are provided with some options like scanning all the drives, scan the user drive, scanning the desired files and folders and this option can be selected by the users and the corresponding buttons used are given in the above screenshot.
Users are also provided with an option to create the chart as discussed in the previous chapters and this chart can be used to track the detection time and detection rate of the C-worms. A separate settings window is also created to view few key settings to be done to the scan process and these includes the aspects like Task manager, empty the virus files and this operation is used to delete the infected files and a separate settings button is also provided to update the settings of the C-worm scan process. The status of the files being scanned are also displayed to the users across this window and a separate text area is provided to track the number of infected files and the corresponding details like the actual folder and directory of the file along with the impact on the corresponding file due to the affect of the C-worm and the respective screenshots are as given below
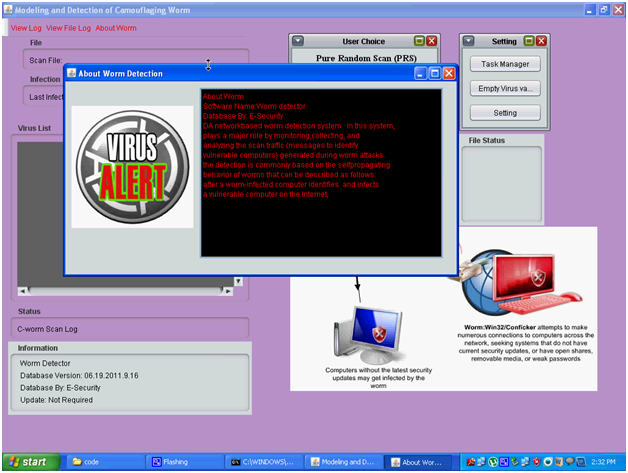
Above screen shows the technical specification of the C-worm and this option is provided at the left top corner of the actual home window. Once the users click on this option, a separate window is opened and the required technical specification and description of the worm is displayed to the users as shown in the above screen.
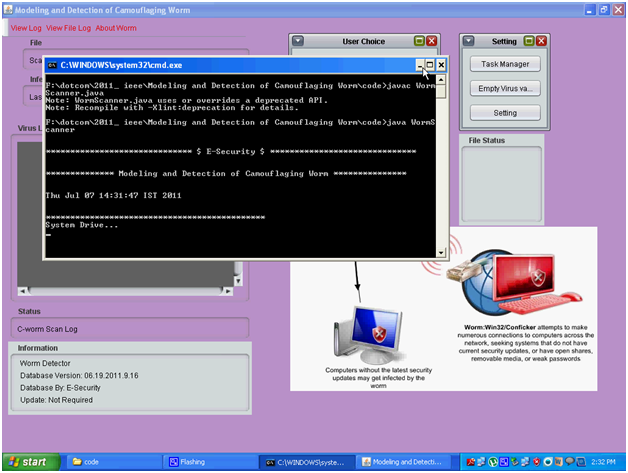
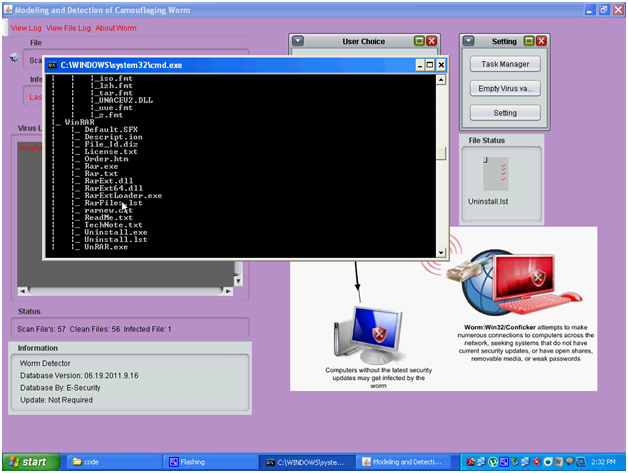
Above screen is displayed to the end users when they chose the desired drive or folder to scan the files and a separate command prompt window is opened to show the background process being run across the application. A widow is opened and shows the status of the current drive being scanned as shown in the above screen.
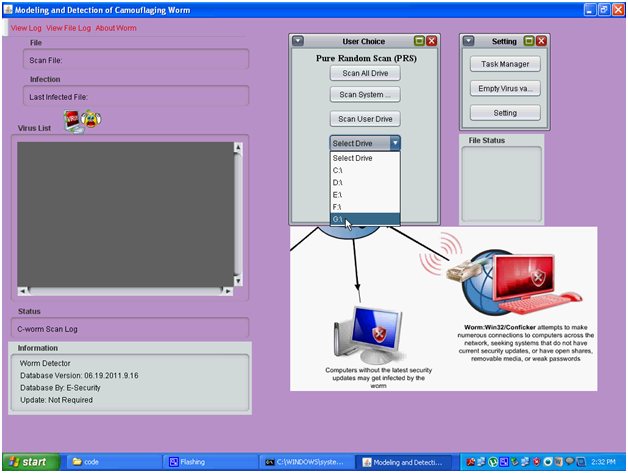
From the above screen it is clear that the user can select the desired drive from the drop down list provided to the users and they can select one of the drives available to proceed with the C-worm scan. Similarly the users can also choose the few options available like the scan all the drives, scan the complete system and scan the user drive based on this opinion the actual scanning process is initiated and is as shown in the above screenshot.
From the above screen it is clear that the status of the fie being scanned is shown in the separate text area. The percentage of the scan operation is shown in the desired text area and is as shown in the above screen and the corresponding status of the scan is done is also shown in the above screenshot.
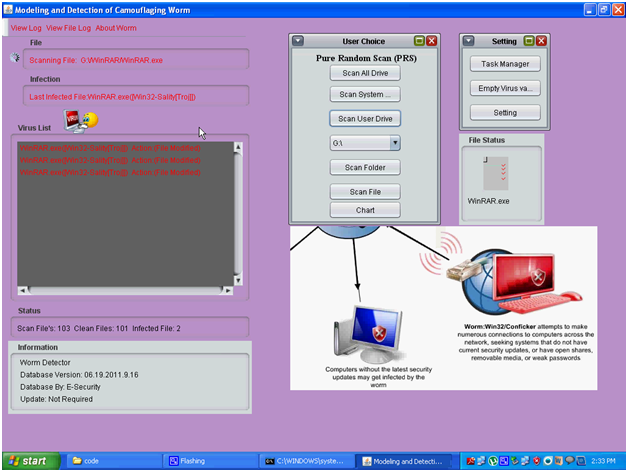
From the above screen it can be observed that the status of the current file being scanned is displayed in the virus list text area and also the columns like File and Infected file are also displayed to the user against the scan operation as shown in the above screen. The virus database is updated against scanning operation and the level of impact of on the files is also tracked and is shown in the above screen.
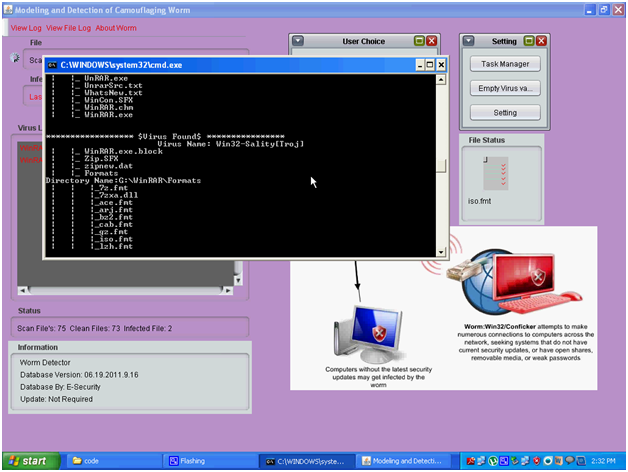
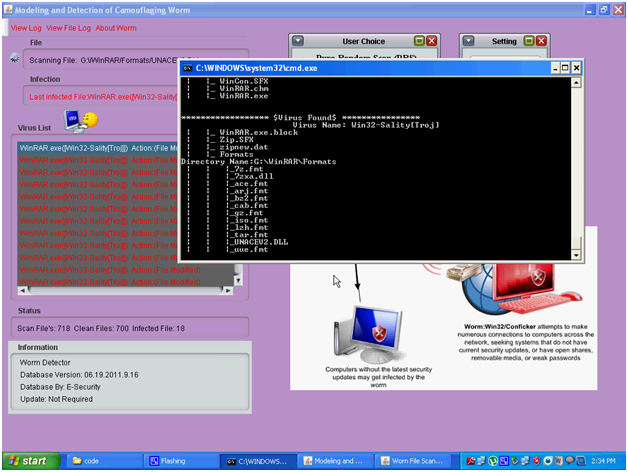
Above screen shows the actual list of files being scanned and a separate command prompt is opened. All the extensions of the files are shown in the above screen and the process being followed to scan the files is also shown in the above screen and the corresponding files being scanned is shown in the File status window on the right side of the window. The files are scanned based on the extension of the files being visited and if any malicious activity is found across the scanning process, immediately the same file is update to the virus database and also the log files maintained across the application as discussed in the previous section.
When any virus or worm is found across the scan process, the above screen is displayed to the end users with the exact details of the virus and the level of infection done to the corresponding file selected during the scanning process.
Above screen shows the virus list text area and all the infected files are tracked in this area. Key details like exact file name, the folder where the file is existing and the action performed by the C-worm on the corresponding file is displayed across the text area as shown in the above screen. The current infected file is also shown at the infection area as shown in the above screen and once the values are listed in the virus list area, the same are updated to the scan log file and the corresponding screenshots are shown below
The task manager operations are shown in the above screen and the performance of the CPU against the scanning operations are tracked using the settings window that was created in the main window of the application. Few usage of the CPU like CPU usage and Page file usage history are tracked in this section and the corresponding screenshot is as shown above.
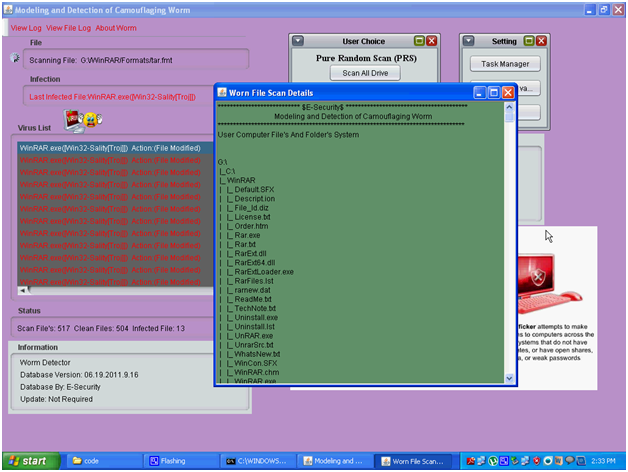
The worm file scan details are shown in a separate window and are as shown in the above screenshot. Current files being scanned and the corresponding directory are shown in this particular window. All the files in the user directory are displayed and the level of files and directories scanned till the point of time are shown to the end user as shown in the above screen.
Above screen shows the command prompt level of the infected files and these details includes all the folders and directories also and is shown in the above screen. A separate batch file is created to view these details and these values are actually tracked from the scan log files as discussed in the previous section.
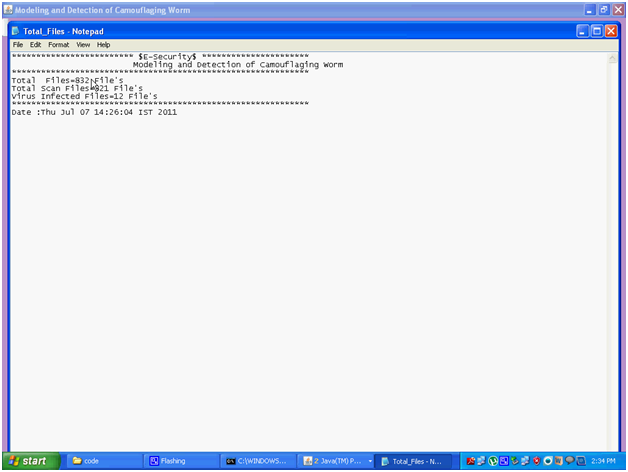
Above the actual log file created after the scan process has completed and the log file is created in the notepad and the corresponding screenshot is as shown above. These details include total file scanned, total file infected and the corresponding date and time details are displayed and is as shown below
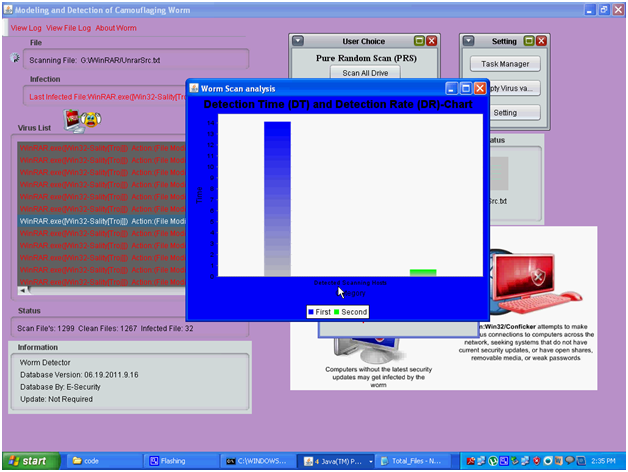
The actual analysis of the scan progress in the form of chart is as shown in the above screen and the corresponding graph generated is shown in the below screenshot


Hi,
I’m a student and I wanted to know which software was used in the “Results and Analysis of camouflaging worm Final Year Project” Project. I have read the description given on this page. Please let me know if there is a way I can get some more details on this project. Thank you.
Regards,
Sohil
Please send me the source code of this project.
hi,
Please send me the source code of this project.