Abstract
For requirements of high data coverage and rate challenging throughput of future wireless cellular networks, the concept of relaying is found to be a promising solution.
It can be explained in this thesis that the high data coverage rate as well as throughput can be efficiently improved in such networks by making use of digital fixed relays rather working with simple protocols, which do not sustain any penalty of capacity; this explanation is the most significant contribution of thesis. Particularly, the downlink network of non-CDMA is considered in which six digital fixed relates are located simultaneously in every cell in hexagonal arrangement.
Equipment of user is selected to obtain the conveyed signal either through one of the relays or directly from the BD (base station). Three algorithms such as SINR, distance and pathloss are studied for the process of relay selection algorithm. Benefits of diversity are also studied, when the signal is obtained in two-hops.
The proposed algorithms performance can be investigated for several variables of system comprising of cell sizes, rely locations, transmission bandwidth, propagation parameters, transmit power levels, and number of user equipments through simulations of Monte-Carlo.
It can always be shown that the outage is reduced and throughput is enhanced, without having any capacity penalty for practical range of parameters values is investigated. On the whole, it can be concluded that greater potential is included by the digital fixed relaying in offering envisioned high data coverage rate in future wireless cellular networks.
Project Results:
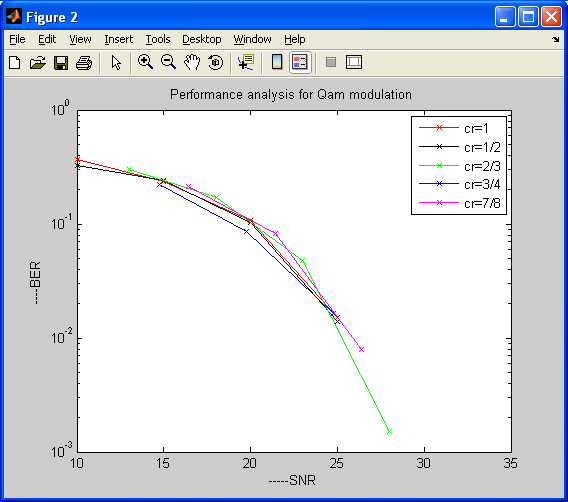
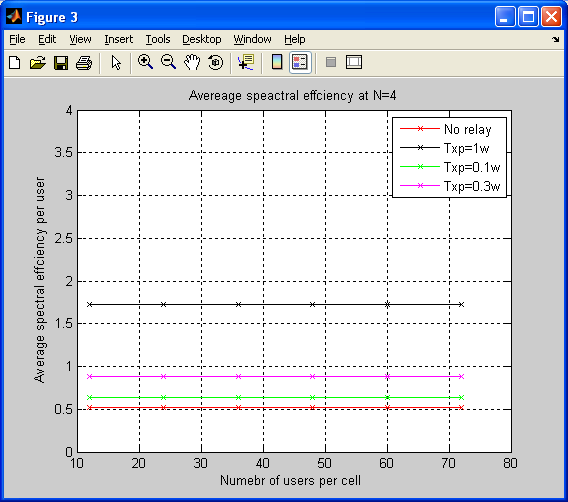
Introduction
Wireless network will go through the point to point or classical cellular networks paradigms. The approaching 4G standard LTE-Advances is the first mobile interaction standard for cellular networks which permit for the usage cooperative transmission models. The base station operation is predictable to increase rates of data an coverage importantly this is compared to existing technologies of 3G.
Cooperation communication is proposed to face Fading of multipath permitting users to spread one another ‘s message to the target. Thus every message is transmitted across multipath spread paths, spatial diversity are achieved without have the need of multipath antennas on every communication channel.
Adaptive filters includes the transformation of parameter of filters the is coefficient across time ,to adapt to transforming characteristics of signal From the 10 decades processors f digital signal had made higher advances in enhancing speed and complexity and decreases consumption of power.
The algorithms of real time adaptive filtering are swiftly become practical as well as important fro the future communications. These will be both wireless as well as wired.
The signal in the adaptive filter continues with the coefficient of adaptive filter, this will adjust themselves to desire results like recognizing of an unknown filter or canceling noise in the signal of input. There have a various types of adaptive filters but the algorithms of Recursive Least square (RLS) as well as Least Mean Squares is having higher importance.
The two main considerations are that this frames the decision of usage of algorithms of filters. The basic concern of usage of adaptive filter is competitive methods to solve that needs of the filtering. In general so many areas resolve the adaptive filter suitability this includes the four areas, they are Filter Performance, DSP requirements, Filter Consistency and Tools.
Project description
Purpose:
The main objective of the project is to examine the Adaptive filter’s performance and transmit a signal from source to target by using relay. The relay is used to increase the network coverage area.
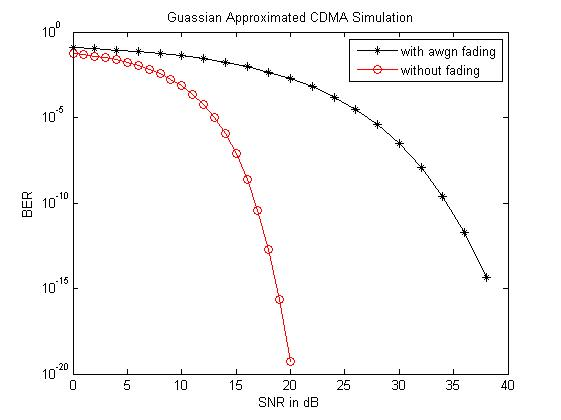
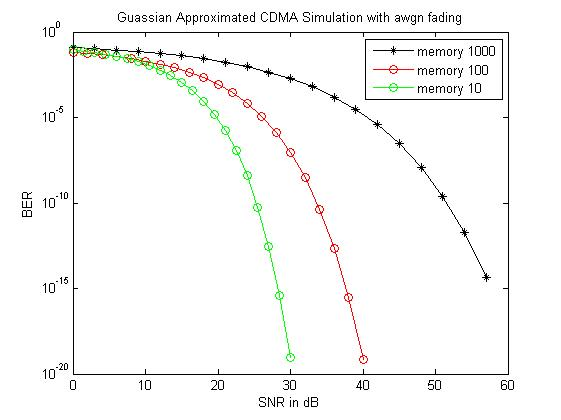
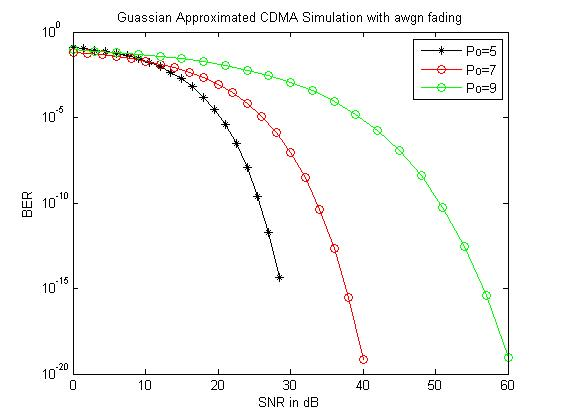
The below figure is project overview and it is model of entire system. The main aim is to compare the performance of the Gaussian signals, the signal passed directly to the target and transmit signal by using the relays of the filters, and in this it mainly prefers single detector and single user.
Scope:
The project mainly explains about the adaptive algorithms effect at Hop or relay and this compare the Recursive Least Square algorithm and Least Mean Square algorithm. Developing coding and algorithms this implements the code in software of MATLAB and examines the performance.
Problem definition:
Performance of future cellular networks depends on the adaptive algorithms implemented across them. The forthcoming 4G standard LTE- Advanced is the first mobile communication standard for cellular networks that allows for the use of cooperative transmission schemes.
The relaying and base station cooperation is expected to enhance data rates and coverage significantly as compared to existing 3G technologies. Adaptive Filtering involves the changing of the filter Parameters i.e. coefficient over time, to adapt to changing signal characteristics.
Over the past three decades, digital signal processors have made great advances in increasing speed and complexity, and reducing power consumption. As a result, real- time adaptive filtering algorithms are quickly becoming practical and essential for the future of communications, both wired and wireless communications.
There are different types of Adaptive filters but Least Mean Squares (LMS) and Recursive Least Squares (RLS) algorithms are of major Importance. The two main considerations frame the decision to use the filter and the filter algorithm to use. The primary concern of using an adaptive filter is a cost – competitive approach to solving your filtering needs.
Project Code:
%%% simulation of the first algorithm for N=4;
clear all;clc
R=2;
Ps=10; %% 10 watt
Pn=1.3;
N=4;
prel=[10^-5 0.1 0.3 1];
%%%%%%%%%%% Distance based algorithm %%%%%%%%%%%%%%%%%
for i=1:length(prel)
PI1=6*prel(i)*1/R;
S(i)=Ps/(Pn+PI1);
end
figure,
plot(prel,N./S,'rx-');hold on;
ylim([0 4]);grid on;
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%% path loss algorithm %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
for i=1:length(prel)
B(i)=10*log10(Ps/prel(i));
PI1=(N)*prel(i)*1/R
if abs(Ps-B(i))~=0
P(i)=min([PI1 abs(Ps-B(i))]);
else
P(i)=PI1;
end
end
plot(prel,P,'bx-');hold on;
ylim([0 4]);grid on;
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
for i=1:length(prel)
PI1=6*prel(i)*1/R;
S(i)=Ps/(Pn+PI1);
bs=Ps*1/R;
Sr(i)=max(S(i),bs);
end
plot(prel,N./Sr,'kx-');hold on;
ylim([0 4]);grid on;
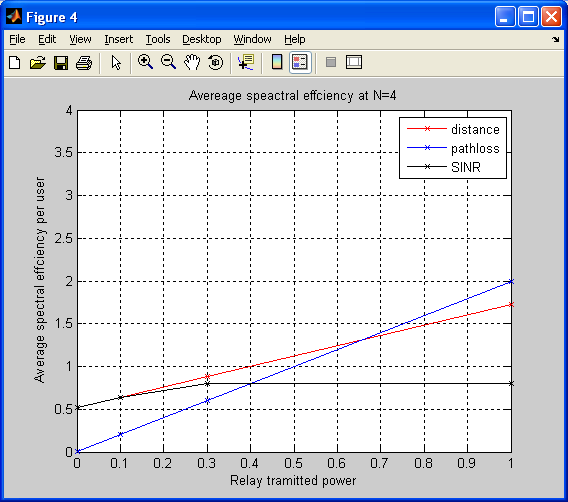
title('Avereage speactral effciency at N=4');
xlabel('Relay tramitted power')
ylabel('Average spectral effciency per user');
legend('distance','pathloss','SINR')
Aims & Objectives
Aims: To analyze the performance of future cellular networks in terms of Adaptive algorithms using MATLAB simulation.
Objectives: Following are the research objectives of the project
- To analyse the concept of Future cellular networks and the role of Adaptive algorithms.
- To prepare the literature review on the existing performance evaluation techniques across cellular networks and their limitations.
- To design Adaptive algorithm that can be used to analyse the performance of future cellular networks.
- To compare the performance of a Gaussian signal i.e. the signal transmitted directly to the destination and the signal transmitted using the Adaptive Filters at the relay
To simulate the proposed system in MATLAB and document the observations