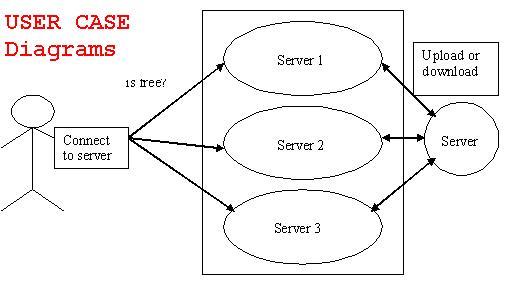
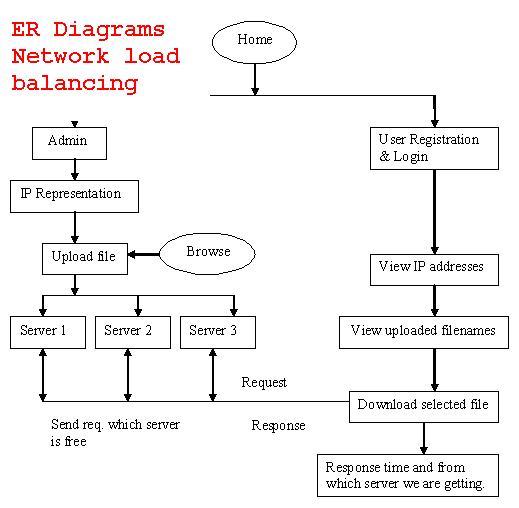
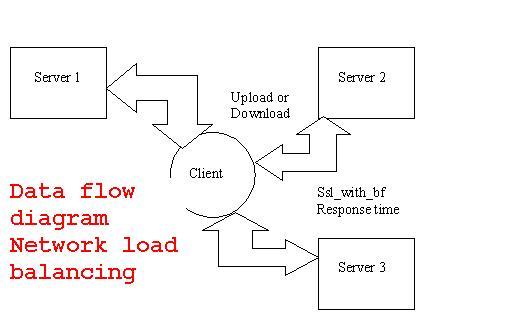
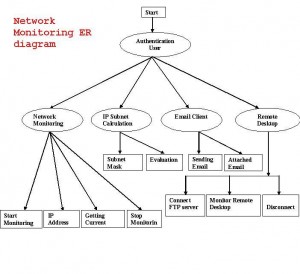
The project “Network Load Balancing” is designed using Microsoft Visual Studio.Net 2008 as front end and Microsoft SQL Server 2005 as back end which works in .Net framework version 2.0. The coding language used is VB .Net.
Many distributed real-time applications, such as audio- and video-conferencing, require the network to construct a multicast path (tree) from a sender to multiple receivers. Furthermore, real-time applications have Quality-of-Service (QoS) requirements (e.g. bandwidth). The objective of the routing protocol is to build a tree that is both feasible (i.e. satisfies the requested QoS) and least costly.
The cost of a tree depends on the costs of its links. The cost of a link should reflect the effect of allocating resources to the new connection on existing and future connections. Many studies have proposed multicast algorithms to construct low-cost QoS-constrained trees.
However, these studies assume that some cost is given for each link, and they do not examine the effect of the link cost function. In this paper, we examine the effect of various link cost functions on the performance of two classes of multicast routing algorithms under both uniform and skewed real-time workload.
We also investigate the impact of inaccurate network state information. Our simulation results show that when network state information is accurate (most up-to-date) at each router, the choice of the link cost function only has a negligible effect, if any, on the routing performance.
More interestingly, we find that, a link cost function that is more sensitive to load performs better when link state information is relatively accurate, while when link state information is more stale, a link cost function that is less sensitive to load performs better. This is more pronounced under higher load and when multicast groups are denser.