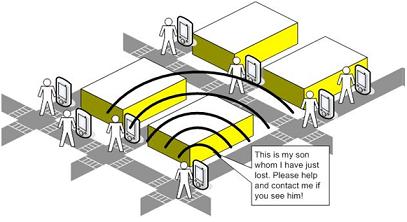
Mesh Networking Seminar Report covers in depth information on this topic here we explain about basic out line of the topic.This topic explains about concept of networking in which each node needs to capture its data but also they disseminate their own data. They are depended on the other nodes and then they send the data in to the network. They are designed with the help of routing or flooding. When we send message on the network then message travel on the path by jumping from one node to others nodes and in this way they reach the destination.
The connection we create must be continuous and they must be connected to each other. Mesh Network is something like MANET, or ad hoc networks. To resolve the problem of continuous network we have to use self-healing based algorithms. It does not allow to break even single node and it make the connection reliable. These types of networks are used in the wireless networks.
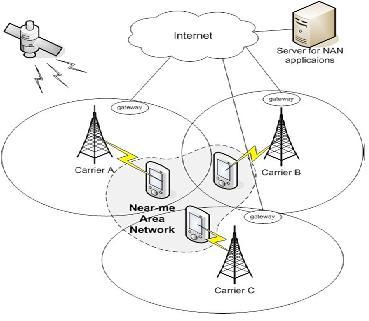
A mesh Networking Example:
Different Types of Network in Wireless Mesh Network:
Zigbee: it is the high level communication that uses very low power. They are based on the IEEE standard that used radio signals for communication. They are used in different applications. They are developed for personal networks. They can be used in the light switches, meters, or home appliances that will operate on your message send by from cell phone. They are not expensive like other WPANs such as Bluetooth. They are developed for short range communication. They can send data at the speed of 250 kbps.
Wi-Max: they are also the wireless networks. They are wireless broadband networks that work like telecom operators. They send signals using high towers. It is also called 4G. They send the data at the speed of 75Mbits per sec.
Wi-Fi: they are wireless network that are limited to the building or college campus. They can be used in the mobile and the Laptops for internet connection. they can also be used in the other device that have Wi-Fi feature.
This Mesh Networking Seminar Report is submitted by computer science students. Students can also find paper presentation on this topic.
Content in Mesh Networking Seminar Report:
Types of mesh Networks
Mesh Network exmaple
Download Mesh Networking Seminar Report.