Abstract:
The task of securing highly confidential data is of great need in data communication, and data transfer these days, data hacking and phishing are of great vulnerable to confidential data in today’s internet world . Securing of data through password, and multilevel-password is not far enough safer for data it contains. The data these days needs a better level of security procedure which can ensure data integrity and security faster with fewer levels of process, better user interactivity and user friendly.
The security measure taken must be far enough to withstand the possible intrusions in may come across while data is transferred over a network and thereby ensuring the integrity of data to be delivered to its corresponding recipient/recipients as it is look and feel while sending, making data communication between sender and receiver safer and easier.
Sensing the above said problem on data security, the precise methodologies to safeguard data in a sound way is to make use of Algorithm encryption standards and digital signature methodology, which ensure data integrity and protection to data the optimal way.
Through rigorous analysis on level of security the data communication needs, a set of requirement for the proposed system was identified and functional specification document was prepared.
“Cipher Data Transfer and De-cipher System” is a windows application which is capable of providing better security to data, through intuitive user interface and accepted world class algorithms and methodology that provide high-end security to data, transfer of cipher data is also possible via this application.
Microsoft visual studio mend with .Net Framework, with world class reputed algorithm concepts and methodology and SMTP is used to develop this application confirming all norms, standards, and thereby fulfilling needs and requirements. Microsoft visual studio IDE is used to design the front-end application and C# concepts are used as hard-code. SMTP is implemented for data communication of cipher data between the sender and its corresponding recipients
INTRODUCTION
CDT-DS (CIPHER DATA TRANSFER AND DE-CIPHER SYSTEM)
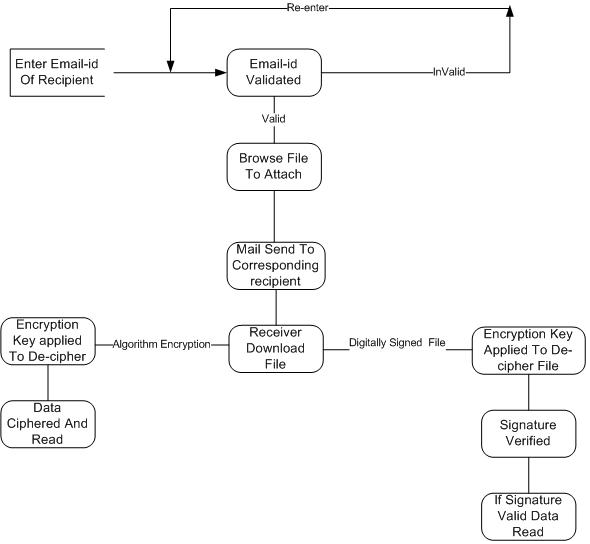
The CDT-DS is developed to provide high-end security to data and data communication in cohesion with the world-wide reputed algorithm’s Advanced Encryption Standards (AES), Data Encryption Standards (DES), and Digital Signature methodology
The CDT-DS is designed to ease the burden of data security to any authenticated user through all levels of it processing data. CDT-DS is a single roof multi-process application, where u can secure data using algorithm encryption, apply digital signature to data, and send cipher data through mail transfer application.
In early days data encryption needs symbolic codes table and other technical notation for encrypting every given data it take huge amount of time and human source and needs only technical persons, who did encryption or need person who knows about that encryption , making data security and data communication those days was indeed a frantic task to perform.
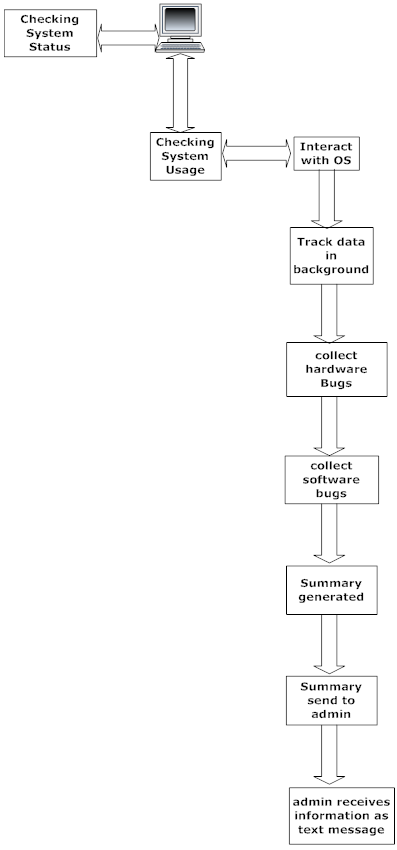
But these days data encryption is eased a lot through modern and advanced technologies, of one is facilitating the Cipher data transfer and de-cipher tools is much efficient to make all sort of data security is performed and gathered by application and forwarded to administrator mobile without time, money, and energy waste thereby saving a lot of resources.
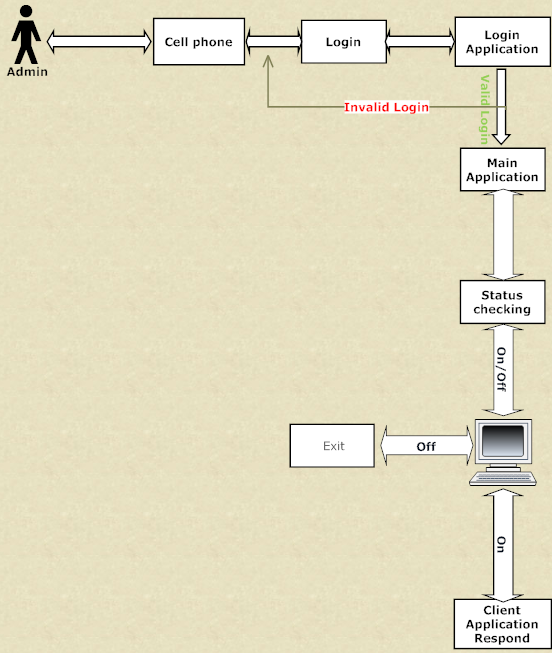
This Cipher Data Transfer and De-Cipher System application aims at assisting the administrator who wants to gather information of clients system in a subtle way, with the help of Operating System protocol in client’s pc, this omnibus process is done in milieu when the OS is in idle state interacting with the system files to generate reports.
This collection process needs authenticated access from administrator side, upon valid authentication the information is generated and sent to mobile. This application also supports all Operating System, making the functionality of this tool much more efficient, across different platform.
SOFTWARE ENVIRONMENT:
Operating System : Windows, Linux (.Net Framework needed)
Basic needs : IIS, .Net Framework, Browser,
Internet Tools : Anti-Virus (Optional)
Advantages:
- The Cipher Data Transfer and De-Cipher System application is highly control based, easy to use.
- The application has a user friendly GUI interface.
- The application is robust in terms of data size.
- Mailing confidential data is possible using the mailer tool.
- It has encryption and digital signature for data security.
Disadvantages:
- If data is big and vast, it takes time to encrypt.
Application:
This Cipher Data Transfer and De-Cipher System Application is useful for organization who wants to preserve their data confidentially, Where data is treated more as an investment, where data securing is all the business, this application has all features of preserving the data as it is before securing. It has digital signature for data integrity, it has algorithm for encryption, it has mail sending tool to forward data.
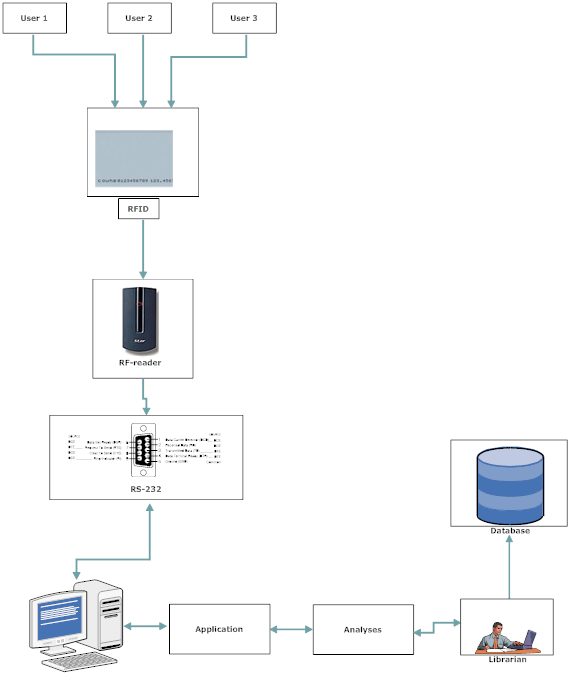
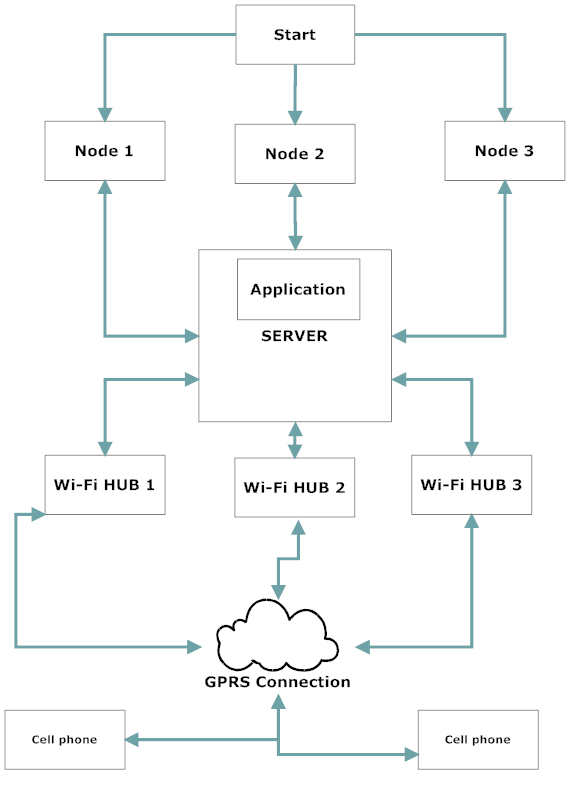
Block diagram
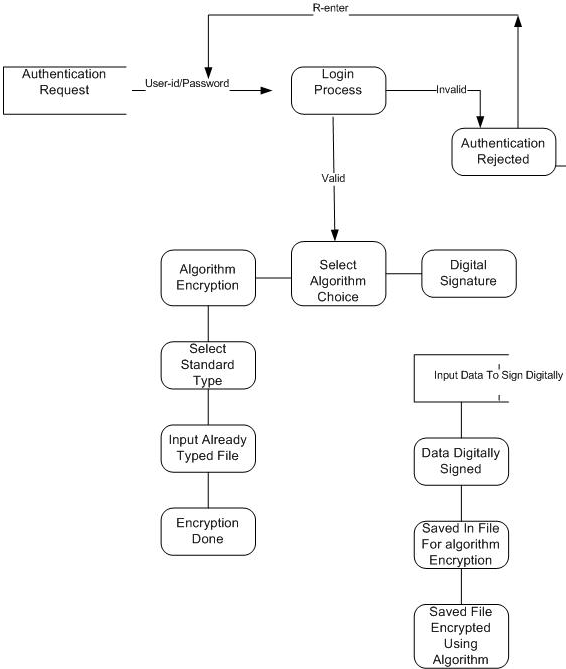
Client side: