Steps in TLS (SSL v 3.3 is indicated as TLS) Handshake
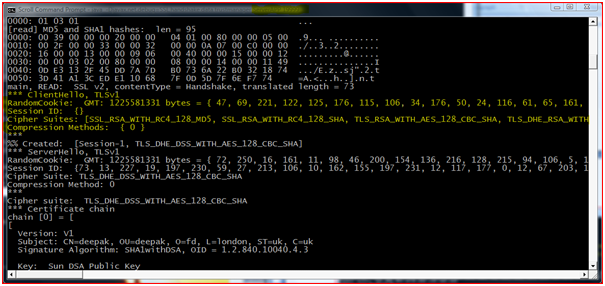
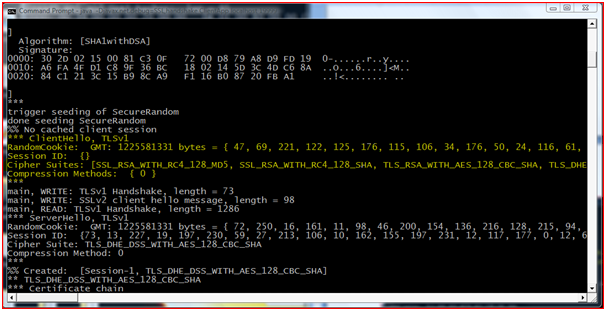
Client Hello: In this step the client initiating the connection would send a hello message to the Server, stating the information about the highest TLS (SSL v 3.3 is indicated as TLS) protocol version it supports, list of cipher suite with the cryptographic algorithms and the key sizes they support and the random sequence number.
Figure : Debug message showing Server Side “Client Hello Message”
Figure : Debug message showing Client Side “Client Hello Message”
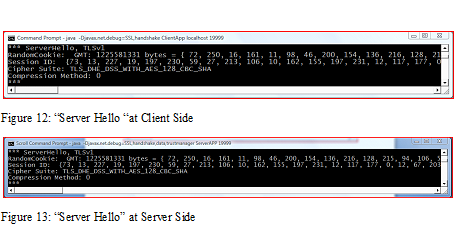
Server Hello: In response the Server will reply with Server Hello message along with the selected highest protocol, cipher suite, random number and compression method.
“Server Hello “at Client Side and “Server Hello” at Server Side
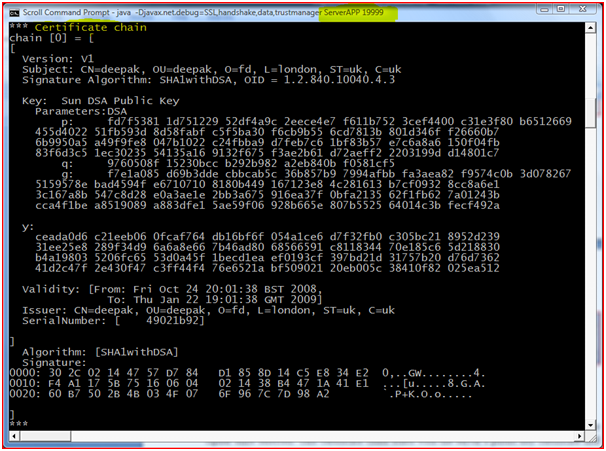
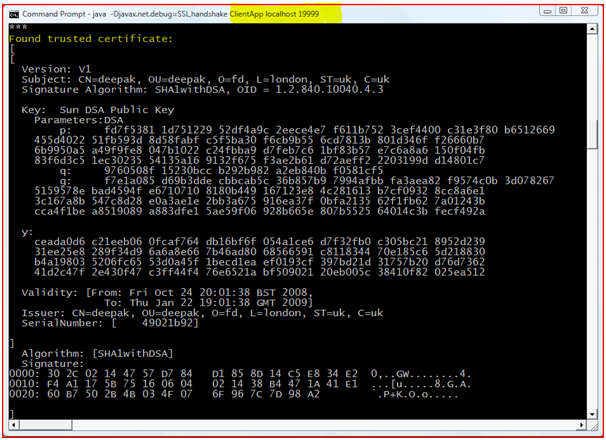
Certificate Exchange: Server will send a Certificate or a certificate chain depending on the cipher suite selected. This certificate chain starts with the server’s public key certificate and ends with the CA’s root certificate (it is an optional step for the server depending on the cipher suite selected).
Figure : “Certificate Chain” at Server Side
Figure : “Certificate Verification” at Client Side
In the above screen shot it is shown that the certificate that has been send by the Server is validated. If the certificate is found to be invalid handshaking is terminated.
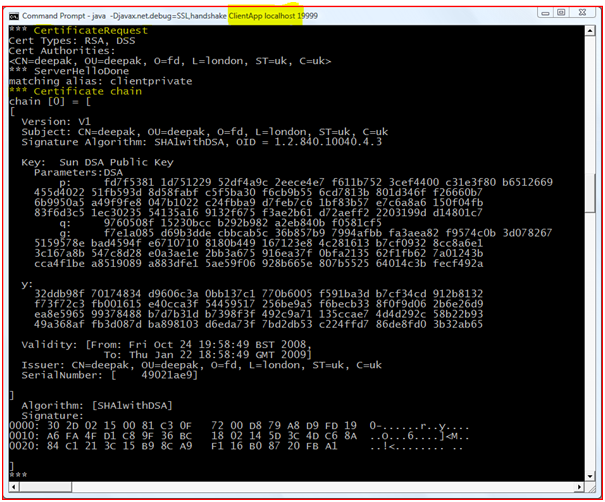
Certificate Request: For mutual authentication server also needs to authenticate the client. Hence server sends the client certificate request.
Figure : “Certificate Request” from Server at Client Side
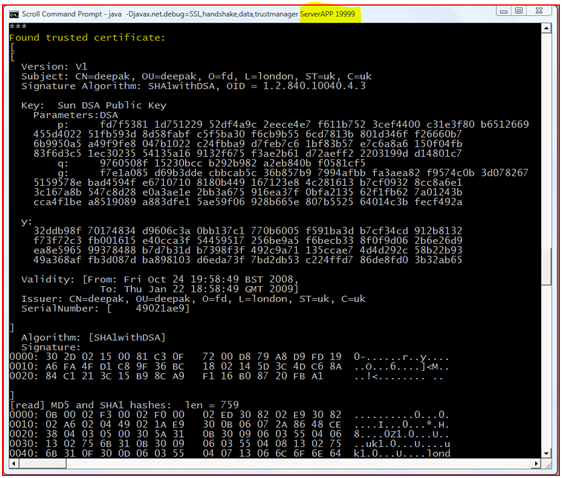
Figure : “Certificate Verification” at Server Side
In the above screenshot it is explained that the certificate send by the client is validated by the Server, hence mutual authentication is done.
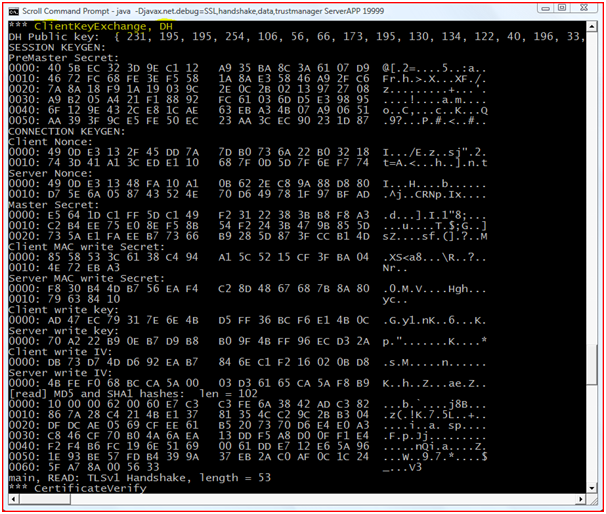
Server Key Exchange-Server requests the client key exchange message if the key information exchanged in the previous step is insufficient.
Figure : Server Requesting Client Key Exchange
Figure : Client Sending the Key Exchange
In the above screenshots it is shown that the Server is sending the client Key Exchange message for extra key information, and the client responds to it respectively.
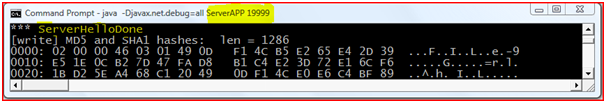
Server Hello Done:When the exchange of all the information for secure communication is done Server sends “Hello Done” message which means that the handshaking is done.
Figure : “Server Hello Done”
Client Certificate: In according to obtain mutual authentication, to the response for the server request, Client certificate will be sent to the server.
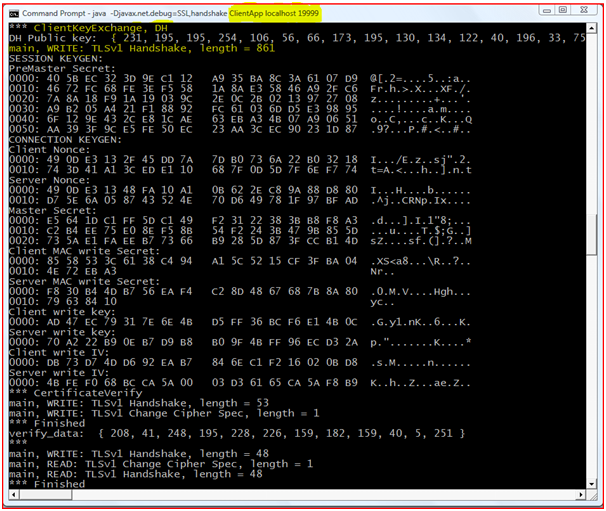
Client Key Exchange: Depending on the Servers selected cipher suite Client will send a Client Key Exchange method containing “premaster secret”, public key. “Premaster secret” is encrypted using public key of the server certificate.
Certificate Verify: Client does the signature over the previous handshake message using its certificates private key using the cryptographic hash function. By receiving the reply message server will decrypt the message using the client’s public key. This will make sure that the client has access to the private key of the certificate and it owns the certificate.
Master Secret: To compute this Client and Server uses a random numbers and PreMaster Secret also known as common secret. This is derived by passing it through a “Pseudorandom Function”. To carry on this connection all the data required is derived from this Master secret.
Change Cipher Specification: By passing this command client is initiating Server to change to encrypted mode. This is a record level protocol 20(Change Cipher Spec).
In this screenshot client is initiating server to change the Cipher suite to make the communication encrypted.
In the above screenshot server reads the request send by the client and it response with the finished message.
Finished: It means that the connection is ready for secure data communication, by sending MAC and Hash value over the previous hand shake messages.
Change Cipher Spec: Server sends the message to tell the client to change to encrypted mode.
Finished: Server decrypts the Client’s “Finished” message and verifies the MAC and HASH values, if this process fails the handshake is failed and the connection is dismantled. It means that this is the end of the TLS (SSL v 3.3 is indicated as TLS) handshake.
Encrypted Data: If the Hand Shaking is successful, then the secure connection is established and Client Server starts communicating using the symmetric encryption algorithm and the Cryptographic Hash functions committed in steps 1 and 2 and the secret key exchanged in the “Client Key Exchange” step.
After successful completion of TLS Handshake client and server will exchange the messages by following the encryption algorithm and key which are obtained using agreed TLS-Handshake process. Check sum is calculated on the encrypted message and this checksum will be encrypted using private key of the private key certificate and it is appended to the encrypted network message and then the message will be sent to the server.
This Project Paper is written & submitted by Deepak V.

How can i get the chat program using tls and ssl? can u mail me the project?